- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- Authentication CIM tags and mapping
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Authentication CIM tags and mapping
Hello all,
I need help manually mapping a log source that has no supported add on. I entered in two event types with tags to ID which log is a failed login and which is a successful login. They are listed below.
Search: index=index sourcetype=logsource LoginSuccessful=0 Tags: authentication, failure
Search: index=index sourcetype=logsource LoginSuccessful=1 Tags: authentication, success
But in the Auth DM fields, it is showing every event as Authentication.is_Failed_Authentication and every event as Authentication.is_Successful_Authentication. Can someone send me the link to the right mapping doc in Splunk or describe what I am missing here. Do I need to enter a field alias as well?
Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
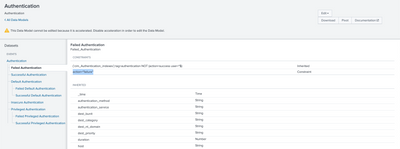
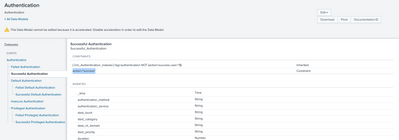
Hello @gwes77, Can you please confirm what's the value of the action field? Because both, success and failed authentication does have "(`cim_Authentication_indexes`) tag=authentication NOT (action=success user=*$)" in common but not action. Below screenshots for your reference -
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi bro sorry for the late reply went to go make dinner for four years.
If I understand your issue correctly, you are having issues finding your authentication CIM via data model search.
In order to map your authentication logs to authentication CIM, you can add the following lines into your tags.conf file (located in TA):
[eventtype=[..]]
authentication = enabled
If you are unsure of your eventtype, you should also have eventtypes.conf where you can map the sourcetype to eventtype.
Hope this clarifies your doubts, I will go eat my dinner now.