Join the Conversation
- Find Answers
- :
- Apps & Add-ons
- :
- Splunk Development
- :
- Splunk Dev
- :
- how to compare two search results and display only...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how to compare two search results and display only missing values in one searched result respect to other
i have two set of result which give AVC_ID and what i want is compare these two set of result and only display missing AVC_ID with respect to the each searched results.
like search result1
AVC1
AVC2
AVC3
search result 2
AVC1
AVC3
AVC4
expecting output
1. missed value in search result 1 with respect to search result 2
AVC4
2. missed value in search result 2 with respect to search result 1
AVC2
i tried below query and getting error:
search 1:
eventtype="li_specific" |eval (AVC_ID=case(searchmatch("AVC*"),"AVC*") |dedup AVC_ID,_time |append [search eventtype="hfc" |eval (AVC_ID=case(searchmatch("AVC*"),"AVC*") |dedup AVC_ID,_time ] |table AVC_ID
search 2:
eventtype="ne_config" |eval (AVC_ID=case(searchmatch("AVC*"),"AVC*") |dedup AVC_ID,_time |table AVC_ID
comparison query:
eventtype="li_specific" |eval (AVC_ID=case(searchmatch("AVC*"),"AVC*") |dedup AVC_ID,_time |append [search eventtype="hfc" |eval (AVC_ID=case(searchmatch("AVC*"),"AVC*") |dedup AVC_ID,_time ] NOT ([search eventtype="ne_config" |eval (AVC_ID=case(searchmatch("AVC*"),"AVC*") |dedup AVC_ID,_time |table AVC_ID |rename AVC_ID as "avc missing in ne config"])
error which i got while running comparison search:
: Error in 'append' command: The last argument must be a subsearch
could you please help me how to achieve this.
Thanks in Advance.
Mani
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
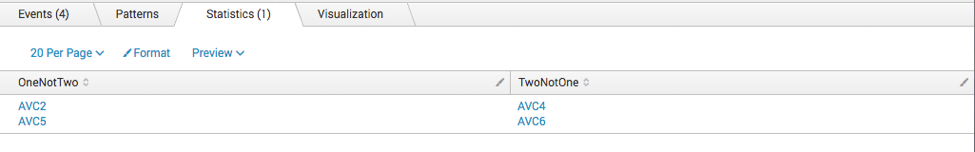
Try using multisearch. This isn't super fast, but it did the trick. I added an extra value to each list to play around with when there were multiple differences.
| multisearch
[ search source="result1.csv" NOT
[ search index="scratchpad" sourcetype="results" source="result2.csv"
| fields AVC_ID]
| eval OneNotTwo=AVC_ID
| fields OneNotTwo]
[ search source="result2.csv" NOT
[ search index="scratchpad" sourcetype="results" source="result1.csv"
| fields AVC_ID]
| eval TwoNotOne=AVC_ID
| fields TwoNotOne]
| stats values(OneNotTwo) as OneNotTwo values(TwoNotOne) as TwoNotOne