- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- "Saml response does not contain group information"...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would appreciate suggestions on how and what to change in our IdP environment and/or our Splunk instance's SAML configuration, to get around this "Saml response does not contain group information" error:
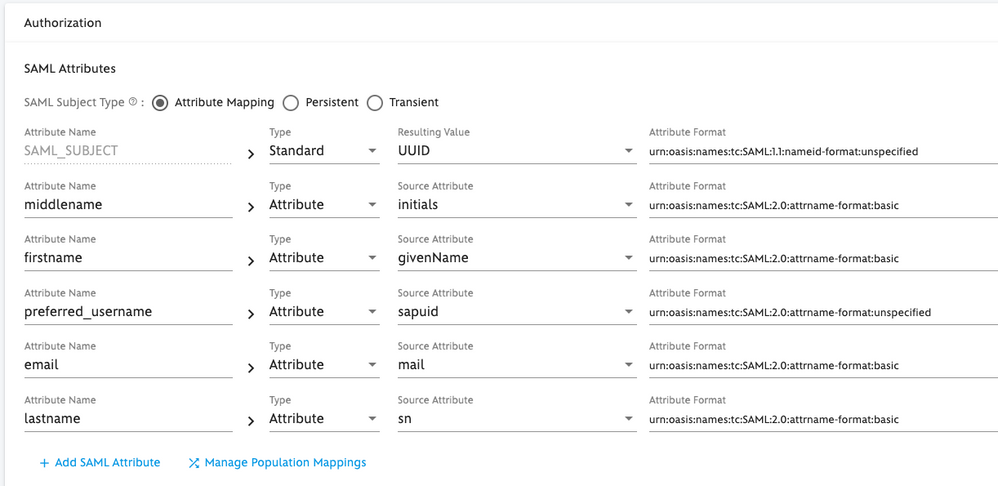
Screenshot of our internal SSO IdP configuration:
Relevant bits from authentication.conf:
[authentication]
authSettings = saml
authType = SAML
[userToRoleMap_SAML]
doerj001 = admin::::joe.doer@whatever.local
smitr003 = user::::roger.smith@whatever.local
incom017 = user::::margarita.incognito@whatever.local
[roleMap_SAML]
admin = doerj001
user = smitr003;incom017
[saml]
clientCert = /opt/splunk/etc/auth/server.pem
entityId = monitor.splunk.bu.whatever.local
fqdn = https://monitor.splunk.bu.whatever.local
idpCertPath = idpCert.pem
idpSSOUrl = https://idp.myid.whatever.local/idp/SSO.saml2
inboundSignatureAlgorithm = RSA-SHA256
issuerId = https://idp.myid.whatever.local
nameIdFormat = urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
redirectAfterLogoutToUrl = https://monitor.splunk.bu.whatever.local/en-US/account/login?loginType=splunk
redirectPort = 443
replicateCertificates = false
signAuthnRequest = true
signatureAlgorithm = RSA-SHA256
signedAssertion = false
sloBinding = HTTP-POST
sslPassword = ************
ssoBinding = HTTP-POST
[authenticationResponseAttrMap_SAML]
role = sapid
Excerpt from the SAML response:
<saml:AttributeStatement>
<saml:Attribute Name="firstname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Roger</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="middlename" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string"></saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="preferred_username"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">smitr003</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="email" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">roger.smith@whatever.local</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="lastname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Smith</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
Appreciate specific suggestions on what we need to change and how, to get this working. (Please do not send me to RTFM - been doing this for the past week and my head hurts - unless the pages you're sending me to contain those specific suggestions.)
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Adding the following mapping resolved the issue:
This way the SAML response from the IdP provided the expected "role" defined in authentication.conf:
[authenticationResponseAttrMap_SAML]
role = sapid
Alternate resolution (guesswork - not tested yet):
[authenticationResponseAttrMap_SAML]
role = preferred_username
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Adding the following mapping resolved the issue:
This way the SAML response from the IdP provided the expected "role" defined in authentication.conf:
[authenticationResponseAttrMap_SAML]
role = sapid
Alternate resolution (guesswork - not tested yet):
[authenticationResponseAttrMap_SAML]
role = preferred_username