Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Why am I receiving errors setting up forwarding en...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why am I receiving errors setting up forwarding encryption?
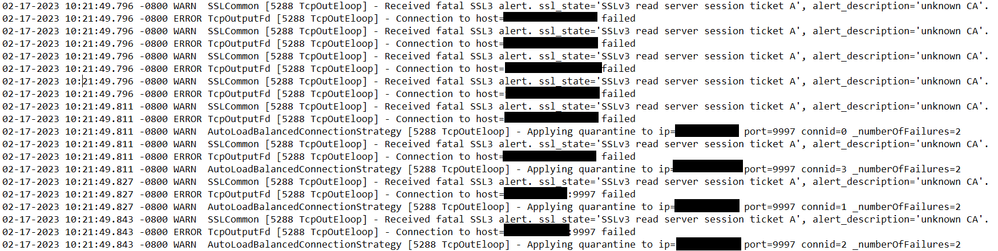
I am attempting to set up encryption between a Splunk Universal Forwarder (verion 9.0.3) and a Splunk Heavy Forwarder (version 9.0.3). I followed the instructions found on this Splunk community site exactly (with the exception of changing the IPs of course to reflect my environment, but am getting the errors below in the splunkd.log file on the Universal Forwarder (the Heavy Forwarder is listening for connections on 9997).
Splunk Coimmunity Site URL https://community.splunk.com/t5/Security/How-do-I-set-up-SSL-forwarding-with-new-self-signed-certifi...
Please advise.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To be specific, this is the error I am getting now ----
02-17-2023 11:46:17.588 -0800 WARN X509Verify [7248 HTTPDispatch] - X509 certificate (O=SplunkUser,CN=SplunkServerDefaultCert) should not be used, as it is issued by Splunk's own default Certificate Authority (CA). This puts your Splunk instance at very high-risk of the MITM attack. Either commercial-CA-signed or self-CA-signed certificates must be used.- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, I think I may have figured out how to resolve this issue......
Since the certificates are self-signed, I needed to edit the line (from the outputs.conf on the UF --- AND ---- from the inputs.conf on the HF):
current >>>> sslVerifyServerCert = true
new >>>> sslVerifyServerCert = false
What I need to figure out now is how to get these signed with a legitimate CA. I am assuming there are certs installed on the Splunk HF/UF instances that I can use to sign with --- any help/links would be appreciated.