Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Re: Verification of SAML assertion using the IDP's...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Verification of SAML assertion using the IDP's certificate provided failed. Error: Failed to verify signature with cert
I have configured SAML 2.0 SSO with our own IdP.
My local splunk app http://khal:8000/ successfully redirect to Assertion consumer URL. Then I enter user and pass there and get an error message on spunk login page:
Verification of SAML assertion using the IDP's certificate provided failed. Error: Failed to verify signature with cert
Here is /opt/splunk/var/log/splunk/splunkd.log:
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecOpenSSLX509StoreVerify:file=x509vfy.c:line=341:obj=x509-store:subj=unknown:error=71:certificate verification failed:X509_verify_cert: subject=/CN=selfSi
gned; issuer=/CN=selfSignedCA; err=20; msg=unable to get local issuer certificate
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecOpenSSLX509StoreVerify:file=x509vfy.c:line=380:obj=x509-store:subj=unknown:error=71:certificate verification failed:subject=/CN=selfSigned; issuer=/CN=s
elfSignedCA; err=20; msg=unable to get local issuer certificate
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecOpenSSLKeyDataX509VerifyAndExtractKey:file=x509.c:line=1505:obj=x509:subj=unknown:error=72:certificate is not found:details=NULL
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecOpenSSLKeyDataX509XmlRead:file=x509.c:line=655:obj=x509:subj=xmlSecOpenSSLKeyDataX509VerifyAndExtractKey:error=1:xmlsec library function failed:
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecKeyInfoNodeRead:file=keyinfo.c:line=117:obj=x509:subj=xmlSecKeyDataXmlRead:error=1:xmlsec library function failed:node=X509Data
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecKeysMngrGetKey:file=keys.c:line=1230:obj=unknown:subj=xmlSecKeyInfoNodeRead:error=1:xmlsec library function failed:node=KeyInfo
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecDSigCtxProcessKeyInfoNode:file=xmldsig.c:line=790:obj=unknown:subj=unknown:error=45:key is not found:details=NULL
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecDSigCtxProcessSignatureNode:file=xmldsig.c:line=503:obj=unknown:subj=xmlSecDSigCtxProcessKeyInfoNode:error=1:xmlsec library function failed:
11-27-2019 16:59:30.229 +0200 ERROR XmlParser - func=xmlSecDSigCtxVerify:file=xmldsig.c:line=341:obj=unknown:subj=xmlSecDSigCtxSignatureProcessNode:error=1:xmlsec library function failed:
11-27-2019 16:59:30.229 +0200 ERROR Saml - Error: Failed to verify signature with cert :/opt/splunk/etc/auth/idpCerts/idpCert.pem;
11-27-2019 16:59:30.229 +0200 ERROR Saml - Unable to verify Saml document
11-27-2019 16:59:30.229 +0200 ERROR UiSAML - Verification of SAML assertion using the IDP's certificate provided failed. Error: Failed to verify signature with cert
Here is /opt/splunk/etc/system/local/authentication.conf:
[saml]
entityId = splunkEntityId
fqdn = http://khal
idpSLOUrl = https://idp.cloud.imprivata.com/BOE/saml2/slo/post
idpSSOUrl = https://idp.cloud.imprivata.com/BOE/saml2/sso/post
inboundSignatureAlgorithm = RSA-SHA1;RSA-SHA256
issuerId = https://idp.cloud.imprivata.com/BOE/saml2
redirectPort = 8000
replicateCertificates = true
signAuthnRequest = true
signatureAlgorithm = RSA-SHA256
signedAssertion = true
sloBinding = HTTP-POST
sslKeysfile = /opt/splunk/etc/auth/server.pem
sslKeysfilePassword = $7$3creInbv0FSAruNBlecI/Ax+eJmCOy2kaKaGi/AYzwNChCylHgv/cQ==
ssoBinding = HTTP-POST
Environment:
OS: 18.04.1-Ubuntu.
Splunk Enterprise: splunk-7.3.3-7af3758d0d5e-linux-2.6-amd64 and splunk-8.0.0-1357bef0a7f6-linux-2.6-amd64
P.S: We are using self signed certificates, so answer in https://answers.splunk.com/answers/543221/problem-with-saml-cert-error-uisaml-verification-o.html doesn't apply.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
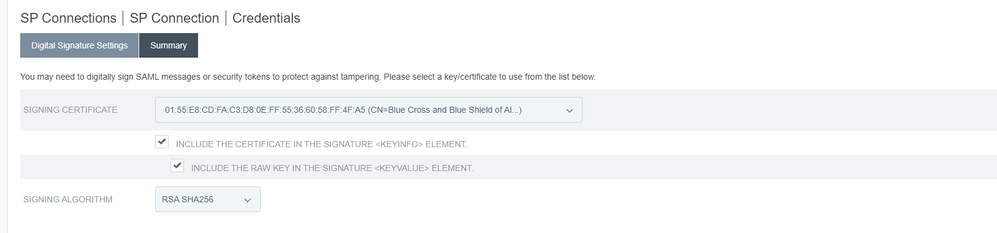
In our case we were configuring Splunk for SAML authentication with Ping as the identity provider (IDP) with Splunk Enterprise version 8.2.7.1. After extensive troubleshooting we discovered that we needed a few check boxes in the Ping certificate configuration.
- INCLUDE THE CERTIFICATE IN THE SIGNATURE <KEYINFO> ELEMENT
- INCLUDE THE RAW KEY IN THE SIGNATURE <KEYVALUE> ELEMENT
We discovered this after comparing the SAMLResponse between a working and non-working environment and noticing that the KeyInfo data was missing in the
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>[CERTIFICATE TEXT REDACTED]
</ds:X509Certificate>
</ds:X509Data>
<ds:KeyValue>
<ds:RSAKeyValue>
<ds:Modulus>[MODULUS TEXT REDACTED]
</ds:Modulus>
<ds:Exponent>AQAB
</ds:Exponent>
</ds:RSAKeyValue>
</ds:KeyValue>
</ds:KeyInfo>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's complaining about your splunkd tls certificate
You need valid ssl certs on the splunk daemon for this to work properly.
Please work with your certificates team to get a valid tls cert for your splunk server. Then install it properly and this error should go away (assuming the idP is trusting the CA that issues your cert).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for responding. Can you please be more specific and provide more details . I don't understand what is the relation between splunkd tls certificate with SAML exchange? It's a sandbox and I use self signed certificates.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You'll find it's nearly impossible to use self signed for saml.
Perhaps if you want to load splunks certs in trusted root stores on all your sandboxed devices... I suppose it could work....
Is your identity provider in your sandbox as well?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IdP is on remote server in cloud while I have local instance of Splunk Enterprise where I test it out.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You'll want use a "valid" cert however you choose how to make it "valid" is up to you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could configure the idP to trust the server.pem file you're specifying in your [saml] stanza for example