- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Edit authentication.conf via CLI
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Edit authentication.conf via CLI
I want to change the ldap account adn its password on all the SHs via CLI.
I tried changing the ldap account and password via a script to edit/relace the account and password , and then restarted Splunk.
But this doesn't seem to work.
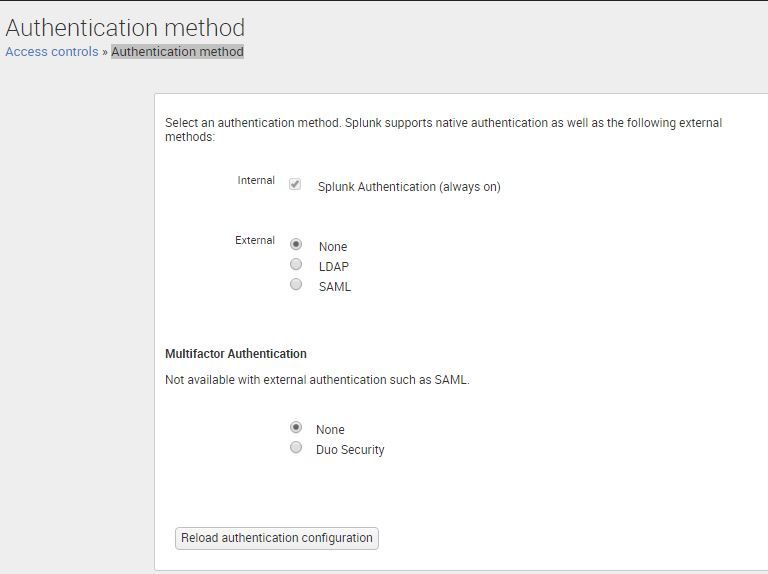
After I did that , I see that there's no Authentication method at all in the Splunk SH UI like below:
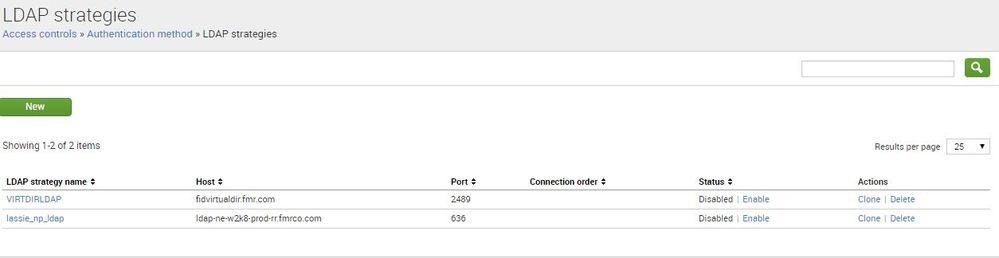
After I select LDAP method I see the two accounts without any AD accounts mapped
How do I to edit the authentication.conf file with new ldap account and password without any breakage like above??
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
our need to create a separate app for Authentication say all_auth.
Deployer:
$SPLUNK_HOME/etc/shcluster/apps/all_auth/local
authentication.conf - only your role mapping like below
[roleMap_ldap_sssd]
role_user_group = ad_group1
authorize.conf - copy authorize.conf from $SPLUNK_HOME/etc/system/local/authorize.conf from one of search head from the cluster.
Search head:
$SPLUNK_HOME/etc/system/local
authentication.conf - only ldap configuration settings.
authorize.conf - there should not be any authorize.conf. Rename authorize.conf to something else
Go to deployer's $SPLUNK_HOME/bin and execute this command ./splunk apply shcluster-bundle -target https://search_head_captain's-ip:8089 -preserve-lookups true
Once pushed check all search head in the cluster should all_auth folder. Then go to GUI splunk instance under settings->access control-> ldap settings->map groups-> all role you have created should be present.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This seems .. unlikely .. I would suspect something unanticipated in your editing of the file.
- I have edited authentication.conf many times directly via the CLI and had no issues like this, especially after a restart. (It is possible to reload most authentication.props properties w/o a restart via the REST API but that is a little off topic for here)
- Authentication.conf (like all other conf files) is subject to btool's merging rules across apps. Make certain you are editing the right authentication.conf file(s) to affect your change.
I think more information is needed (like a before and after of the file itself) before we can give great guidance on what went wrong.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dwaddle
All I did was a script to replace the ldap account and its password.
The file has got replaced with accountname and password but the password has not got encrypted after the splunk restart:
auth.conf Before
[lassie_np_ldap]
sslenabled = 1
anonymous_referrals = 1
binddn = cn=ezp_splunk_ldap,OU=ServiceAccounts,DC=im,DC=tcsco,DC=com
binddnpassword = $1$Hx+uKRbWP/f3
charset = utf8
emailattribute = mail
groupbasedn = OU=FIMT_Managed,OU=Groups,DC=im,DC=tcsco,DC=com
groupbasefilter = (|(cn=FIMT-LASSIE-) (cn=FIMTMON_))
groupmappingattribute = dn
groupmemberattribute = member
groupnameattribute = cn
host = ldapserver.tcsco.com
nestedgroups = 0
network_timeout = 20
port = 636
realnameattribute = displayname
sizelimit = 1000
timelimit = 15
userbasedn = DC=im,DC=tcsco,DC=com
userbasefilter = (objectclass=*)
usernameattribute = samaccountname
auth.conf After:
[lassie_np_ldap]
sslenabled = 1
anonymous_referrals = 1
binddn = cn=ezp_splunk_ldap_dev,OU=ServiceAccounts,DC=im,DC=tcsco,DC=com
binddnpassword = N3F1vSvt
charset = utf8
emailattribute = mail
groupbasedn = OU=FIMT_Managed,OU=Groups,DC=im,DC=tcsco,DC=com
groupbasefilter = (|(cn=FIMT-LASSIE-) (cn=FIMTMON_))
groupmappingattribute = dn
groupmemberattribute = member
groupnameattribute = cn
host = ldapserver.tcsco.com
nestedgroups = 0
network_timeout = 20
port = 636
realnameattribute = displayname
sizelimit = 1000
timelimit = 15
userbasedn = DC=im,DC=tcsco,DC=com
userbasefilter = (objectclass=*)
usernameattribute = samaccountname
Im using $SPLUNK_HOME/splunk/etc/system/local/authentication.conf" on all the SHs to make the changes.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, are the above your whole authentication.conf? There's some things missing. Like I would expect to see:
[authentication]
authSettings = lassie_np_ldap
authType = LDAP
Or something similar .. also a
[rolemap_lassie_np_ldap]
section that specifies the role mappings. As @SloshBurch said prior, "use btool" 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dwaddle ,
I figured out that it was my python script that was causing the problem. It was modifying the file in a fashion that we couldnt figure out all although the contents looked fine.
Thankyou for your support.
However I had another query,
how do we push the config changes for the authentication.file via the deployer to the SHs?
Doesn't shcluster apply bundle push the changes from $SPLUNK_HOME/splunk/etc/shcluster to the SHs?
However the authentication.file is located at $SPLUNK_HOME/splunk/etc/system/local right?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, @saranya_fmr, please be aware that the conf file does not HAVE to live in $SPLUNK_HOME/system/local/. Your config can (and should) live in an app so it can be centrally controlled and deployed.
This is a great page on the topic: http://docs.splunk.com/Documentation/Splunk/latest/Admin/Wheretofindtheconfigurationfiles
If you want to learn more, the Admin and Clustering edu classes should be great.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your need to create a separate app for Authentication say all_auth.
Deployer:
$SPLUNK_HOME/etc/shcluster/apps/all_auth/local
authentication.conf - only your role mapping like below
[roleMap_ldap_sssd]
role_user_group = ad_group1
authorize.conf - copy authorize.conf from $SPLUNK_HOME/etc/system/local/authorize.conf from one of search head from the cluster.
Search head:
$SPLUNK_HOME/etc/system/local
authentication.conf - only ldap configuration settings.
authorize.conf - there should not be any authorize.conf. Rename authorize.conf to something else
Go to deployer's $SPLUNK_HOME/bin and execute this command ./splunk apply shcluster-bundle -target https://search_head_captain's-ip:8089 -preserve-lookups true
Once pushed check all search head in the cluster should all_auth folder. Then go to GUI splunk instance under settings->access control-> ldap settings->map groups-> all role you have created should be present.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please check you have proper file read/write permission on authentication.conf
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"On all Search Heads" is this in a Search Head Cluster? Directly editing the conf files in a SHC could break the cluster.
I agree that you need to check with btool, not the conf file, to see what's up. Sometimes the hashed version of the password ends up getting stored in another conf file and you wouldn't see it until you comment out the one being loaded and see what else is potentially loaded.