- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Configuring Google IDP SAML for Group membership b...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Configuring Google IDP SAML for Group membership based SSO?
Hi,
I am trying to use our Google Idp (Google workspace) to enable SSO on our Splunk.
I followed this link and it worked successfully when adding custom attribute individually to each user.
Now I need to use Google groups for Splunk RBAC so authentication and Authorisation is handled using groups membership.
When using the Groups membership, I couldnt find any clear answer from Google or Splunk about what to be used here as App Attribute
I only found this link
which is useless
I raised a support ticket with google and got this answer
Could you advise on how to setup RBAC using google groups membership or help with Google SAML IDP setup
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had been struggling with the same problem. After a lot of experimentation with different ideas and inspecting SAML payloads. My two main findings as best as I can tell are:
- When you configure a Google Groups mapping in Google SAML configuration, Google will send the group name as an attribute identically to if it were an attribute set up in the attribute mapping.
- When Splunk receives a SAML assertion with a role attribute, I think it will try to match it against roles as well as SAML groups. Though in my case all of the role attributes I use are SAML group names, so I cannot confirm that it will match the "role" attribute against an actual role name.
But also crucially, when you update Google SAML configurations, it can take 5-10 minutes for the update to "go live". So watch the SAML assertions that you are actually sending to Splunk as you experiment, because otherwise you'll make a changes and even if you get it right it'll appear to not work, you'll make more changes, and suddenly things work, but actually the working configuration was n attempts ago, and it will break itself as it slowly updates to your later configuration attempts, and all you'll know is that something you tried at some point over the last however long was correct.
So the net result:
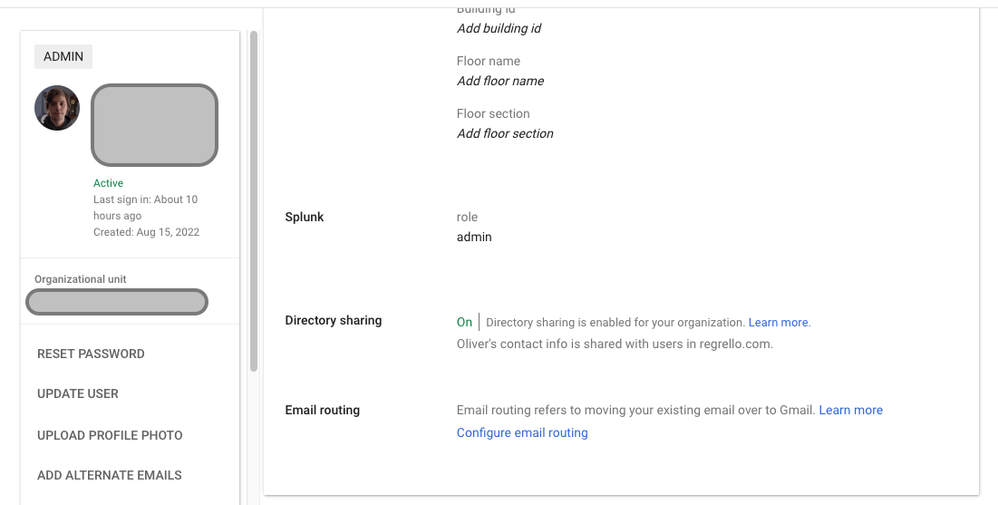
- Set the "App attribute" to "role", exactly like you did in your screenshot. If you have created a role in splunk whose name is the same as your Google group, you're done.
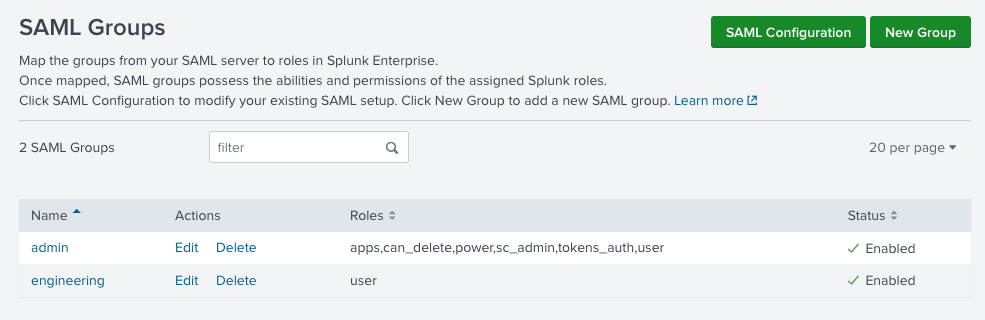
- If your Google group has a different name than your role, then set up a SAML group in Splunk with the same name as your google group and assign it the role you want. Splunk will lowercase the group name, that's fine, it'll still match.
- As a result, you can actually use both (e.g. a group to grant "user" access, and individual user attributes to grant admin access)
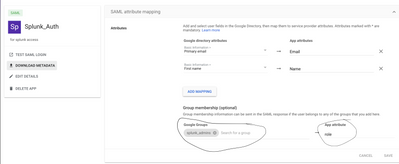
In my case, I already had a Google group called "Engineering" that I wanted to set up with the "user" role. Here are my configs:
Splunk:
1. Configure SAML groups with names corresponding to your Google groups
2. Configure your Google SAML configuration. If you plan to use both user attributes and Google groups, set both a user attribute and a Group membership, both pointing to the "role" App attribute. If you only plan on using groups, you can omit the user attribute. In my case, as you can see from my Splunk config above, I want the "Engineering" google group to all have "user" access to Splunk:

4. If it isn't working, decode and review the SAML assertion that Splunk is receiving. It can take a surprisingly long time for changes made in Google's SAML configuration to go "live". You will likely observe that you're passing along a SAML assertion that does not reflect your most recent Google configuration changes -- if that's the case, just wait a while and try again in a bit.