- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Azure AD SAML Group Claims
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am trying to get Splunk Enterprise to use SAML authentication against Azure AD. I have followed the steps outlined in the directions on the Configure SSO with AzureAD or AD FS as your Identity Provider direction page. I have consulted the Configuring Microsoft’s Azure SAML Single Sign On (SSO) with Splunk Cloud – Using the 'New' Azure Portal blog post as well, even though it is for Splunk cloud and I am using Splunk on prem.
The problem I am running into is when I try to log in, I get an error "SAML response does not contain group information". Using a SAML browser plugin, I can see Azure is not sending the group information in the SAML response. When looking at Azure AD documents for how to Customize claims issued in the SAML token, it states that Azure AD will NOT send the group claims. If Azure AD will not send the group claims, is there anyway for Splunk to do the role mapping? Has anyone else ran into a problem with Azure AD not providing group claims in the SAML response?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
If you use SAML Trace tool, you will notice that group information (object IDs) are within "group" tag.
Like this.
<Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/groups">
<AttributeValue>1bd5ea35-051f-40fd-bc2a-87693900953d</AttributeValue>
<AttributeValue>fec3a8e2-f35c-437d-8191-f850da332f5c</AttributeValue>
</Attribute>
As this article explained ( https://www.splunk.com/blog/2017/11/20/configuring-microsoft-s-azure-security-assertion-markup-langu... ), you need specify "Role alias" and create SAML group in Splunk Cloud. The group name needs to be object ID of your Azure's group's object ID.
In this above example, I created a group in Azure and put my user into the Azure group. The group's object ID is fec3a8e2-f35c-437d-8191-f850da332f5c. So that's why I created "fec3a8e2-f35c-437d-8191-f850da332f5c" SAML group in Splunk Cloud.
Then, everything works perfect.
Please try this. This is confirmed in 2019/Feb/3.
Takashi.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
If you use SAML Trace tool, you will notice that group information (object IDs) are within "group" tag.
Like this.
<Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/groups">
<AttributeValue>1bd5ea35-051f-40fd-bc2a-87693900953d</AttributeValue>
<AttributeValue>fec3a8e2-f35c-437d-8191-f850da332f5c</AttributeValue>
</Attribute>
As this article explained ( https://www.splunk.com/blog/2017/11/20/configuring-microsoft-s-azure-security-assertion-markup-langu... ), you need specify "Role alias" and create SAML group in Splunk Cloud. The group name needs to be object ID of your Azure's group's object ID.
In this above example, I created a group in Azure and put my user into the Azure group. The group's object ID is fec3a8e2-f35c-437d-8191-f850da332f5c. So that's why I created "fec3a8e2-f35c-437d-8191-f850da332f5c" SAML group in Splunk Cloud.
Then, everything works perfect.
Please try this. This is confirmed in 2019/Feb/3.
Takashi.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @tkomatsubara_sp
I have followed the instruction given in the link but still I am seeing the same message(Saml response does not contain group information.) while try to login.
When I try to trace the saml response I don't see the group attribute instead I see role attribute. What is solution to this ?
<Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/role">
<AttributeValue>SplunkAdmin</AttributeValue>
</Attribute>
I have created a group on Azure and assigned, admin role that group.
I have created a group on Splunk using the object ID of the above same group and assigned admin role that group. Rest of the configuration I follwed the document.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
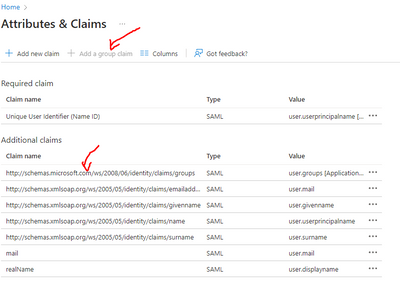
This has been rectified. I had to add Configure group claims for applications by using Azure Active Directory.
For reference I used this link
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After looking into it further, as you have described, the group claims are in the SAMl response. I think the main problem we had was the role alias was not setup at all as described in the article you linked to.