- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Reporting
- :
- Unable to see report in Searches, Reports, and Ale...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
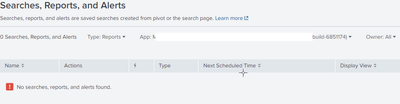
I am having a very wierd issue where I cannot see report in Splunk UI.
When I search using Filter: All, I can see the report but when I set the filter to 0, I get 'no searches, reports, and alerts found'.
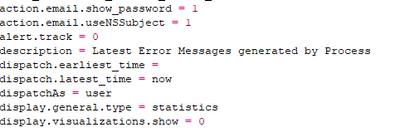
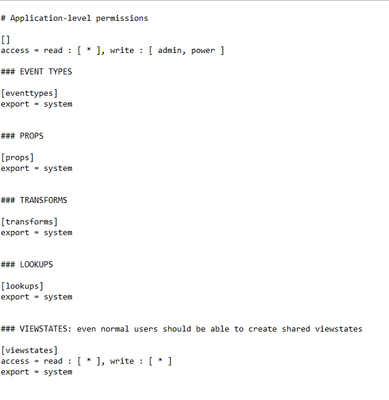
This couldn't be the case of visibilty as the configuration isn't set in the conf file. These are the set specs in the conf file, attched below for reference.
I have also attached the metadata file as there is no access control information set for the specific saved search. There are 6 more savedsearches which I can see when I filter using Report, but not this sepcific one.
No clue how the report is not found during the filter.
Thanks in advance.
Pravin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
I got notifed that this is a bug in Splunk.
Known issues - Splunk Documentation
UNDEFINED keyword shouldn't be used to replace empty cells.
Thanks,
Pravin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
I got notifed that this is a bug in Splunk.
Known issues - Splunk Documentation
UNDEFINED keyword shouldn't be used to replace empty cells.
Thanks,
Pravin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @_pravin,
good for you, see next time!
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_pravin ,
are you sure that these reports and alerts are shared at app level and they are in Search and Reporting App?
try to delesect the app in the search dropdown filter setting All.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
Thanks for responding.
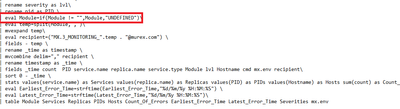
I figured out that the report was not being shown because of the eval command in the search. ( marked in red)
When I remove the line and save the report, I can see the report when the filter is applied.
Not sure how could the eval command affect the report.
Regards,
Pravin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @_pravin .
probably the eval doesn't always match so all the other commands, that use the Module field don't work.
Check if you really need this conditiion and try to replace with the isnull() function.
ciao.
Gioseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
Even I feel that the eval command doesn't always match and so the SPL is not working.
I tried the isnull(), len()>0, and even reversing the condition to look for empty cells, but neither of them worked.
Thanks,
Pravin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_pravin,
please debug your search deleting all the raws until raw before the eval command: what's the value of the Module field?
have you empty values or not?
Please, share your search also in text format.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
The SPL is actually a report, so the data has not even been sent to the function t has been invoked.
I tried to add just the one line to the report and noticed that the report just disappears.
I am also attaching the code below
| mstats sum("mx.process.logs") as count WHERE "index"="mx_metrics" mx.env=$mx.env$ log.type=log span=10s BY pid service.name replica.name service.type module.names severity host cmd mx.env\
| rename module.names as Module
| rename host as Hostname
| rename severity as lvl
| rename pid as PID
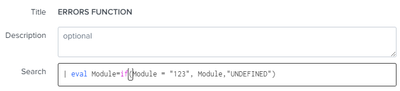
| eval Module=if(Module!="",Module,"UNDEFINED")
| eval temp=split(Module,",")
| mvexpand temp
| eval recipient=("MX_MONITORING_".temp . "@mx.com")
| fields - temp
| rename _time as timestamp
| mvcombine delim="," recipient
| rename timestamp as _time
| fields _time count PID service.name replica.name service.type Module lvl Hostname cmd mx.env recipient
| sort 0 - _time
| stats values(service.name) as Services values(replica.name) as Replicas values(PID) as PIDs values(Hostname) as Hosts sum(count) as Count_Of_Errors earliest_time(replica.name) as Earliest_Error_Time latest_time(replica.name) as Latest_Error_Time values(lvl) as Severities values(recipient) as Owners by Module mx.env
| eval Earliest_Error_Time=strftime(Earliest_Error_Time,"%d/%m/%y %H:%M:%S")
| eval Latest_Error_Time=strftime(Latest_Error_Time,"%d/%m/%y %H:%M:%S")
| table Module Services Replicas PIDs Hosts Count_Of_Errors Earliest_Error_Time Latest_Error_Time Severities mx.envI tried using the line in an another report, and the other report also disapperas in the report filter. Now I feel that this is more of a bug that a code functionality issue.
Please let me know what you feel about this?
Regards,
Pravin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_pravin ,
as I said, if you run
| mstats sum("mx.process.logs") as count WHERE "index"="mx_metrics" mx.env=$mx.env$ log.type=log span=10s BY pid service.name replica.name service.type module.names severity host cmd mx.env\
| rename module.names as Module
| rename host as Hostname
| rename severity as lvl
| rename pid as PID have you null (or similar) values for the Module field?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_pravin ,
see in interesting fields: have you empty values or you don't have values?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
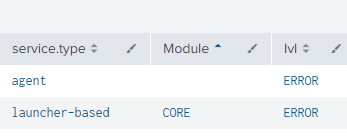
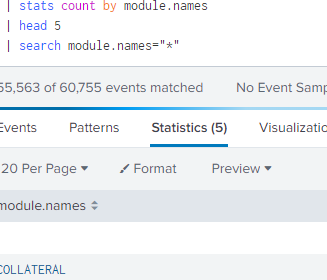
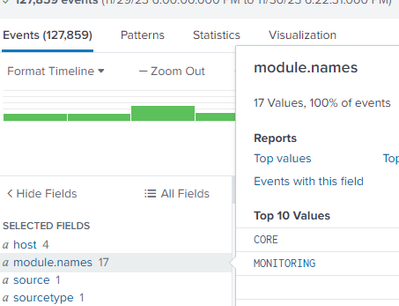
When I run the below search, I get results like these. Not sure if this is empty value or no value.
Regards,
Pravin
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_pravin ,
sorry I wasn't clear; in the events tab, see in the interesting fields if the empty value is present in the Module fields or not.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_pravin ,
did you tried the inverse condition:
| eval Module=if(Module="*",Module,"UNDEFINED") Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content