Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Reporting
- :
- Re: Regex to extract fields between strings
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello guys I hope you are doing well,
It turns out I am in need of a regex that will allow me to extract a "fixed" or "static" pattern within a field that is called HEAD in a splunk search that I have... this so-called HEAD field will start with any kind of words/numbers/strings... but will always have at some point the pattern "***\|Hotel=YY-4857UU45547|" wich is three (*) followed by "\|Hotel=" and then a combination of words and numbers and this pattern with always end with a "|" .... this will may always have some other kinds of words of number after that last "|" so what i an trying to acchive is estracting only the pattern that we know to be always consistent... to show you an example this is one of the real values of that field:
| makeresults
| eval HEAD=" 487542 For Flight Toronto AV TAX VIP client UBER_LIFT_ 78547 ***\|Hotel=YY-4857UU45547| aws not equip Need end seat 1U"and I would like a regex that will allow me to extract:
YY-4857UU45547
and put it in a new field name: RESERV_CODE
I have tried all day and all nig I will ne so thankful to any of you lovely people who can help me out tahnk you so much
love;
cindy
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you try this?
<your_search_goes_here>
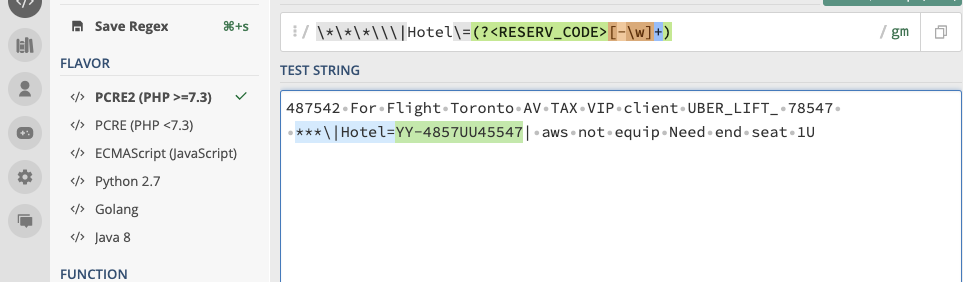
| rex field="HEAD" "\*\*\*\\\|Hotel\=(?<RESERVE_CODE>[-\w]+)"--
An upvote would be appreciated and Accept solution if it helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you try this?
<your_search_goes_here>
| rex field="HEAD" "\*\*\*\\\|Hotel\=(?<RESERVE_CODE>[-\w]+)"--
An upvote would be appreciated and Accept solution if it helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @venkatasri thank you for your help !!! Your code is great but... It does not give the RESERV_CODE until the last "|" but rather gives me the rest of the string in HEAD.. am I doing something wrong?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@cindygibbs_08 Looks fine to me, is that same sample that you have tested?
Can you share how the end result looks like and what was the original event?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@venkatasri hi! Yeah is the same but When I put it in splunk I get everything after the "=" basically...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@cindygibbs_08 can you try this.
<your_search_goes_here>
| rex field=HEAD "Hotel\=(?<RESERV_CODE>[-\w]+)\|"--
An upvote would be appreciated and Accept solution if it helps!