Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Reporting
- :
- Re: How do you find the number of users logged in ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are two sample events
Event 1 -
2018-09-10 11:17:57,982 INFO [http-nio-127.0.0.1-8085-exec-130] [BreakssFogFilter] BF27462 GET https://rambo.ixngames.com/start.action 7485905kb
Event 2 -
2018-09-10 11:10:55,644 INFO [http-nio-127.0.0.1-8085-exec-51] [BreakssFogFilter] ZD07220 POST https://rambo.ixngames.com/userLogout.action 1615031kb
Event 1 indicates that a user just logged in. Event 2 indicates a user logged out. Around 30 similar events get created with slightly different format events when a users logs in or logs out. It also specifies the user name in the events.
We are trying to figure out How many users(distinct) are logged in to the server at any specific hour by analyzing the events from the above mentioned event formats.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hey @zacksoft try this
<your_search>| rex field=_raw ".*\]\s(?<user>\w+)\s\w+" | timechart span=1h dc(user)
let me know if this helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hey @zacksoft try this
<your_search>| rex field=_raw ".*\]\s(?<user>\w+)\s\w+" | timechart span=1h dc(user)
let me know if this helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mayurr98
It executed for five minutes and the visualization was rendering well then all of a sudden it stopped and gave me an error
Streamed search execute failed because: Error in 'rex' command: regex=".*]\s(?\w+)\s\w+" has exceeded configured match_limit, consider raising the value in limits.conf
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I might have to change the rex. I have written rex based on just 1 sample event given.
ok tell me do you have [BreakssFogFilter] common in every sampling event then try this :
<your_search>| rex field=_raw "\[BreakssFogFilter\]\s(?<user>\w+)" | timechart span=1h dc(user)
Also, try this
<your_search>| rex field=_raw "\[\w+\]\s(?<user>\w+)\s\w{3,6}" | timechart span=1h dc(user)
Run it for a shorter period and see if it is giving you correct results then for longer one.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mayurr98
When I run for only 'last 4 hours' it works.
Here are two sample events
Event 1 -
2018-09-10 11:17:57,982 INFO [http-nio-127.0.0.1-8085-exec-130] [BreakssFogFilter] BF27462 GET https://rambo.ixngames.com/start.action 7485905kb
Event 2 -
2018-09-10 11:10:55,644 INFO [http-nio-127.0.0.1-8085-exec-51] [BreakssFogFilter] ZD07220 POST https://rambo.ixngames.com/userLogout.action 1615031kb
Event 1 indicates that a user just logged in, , Event 2 indicates user logged out. Around 30 similar events gets created when a users logs in or logs out specifying the user name in the events.
We are trying to figure out How many users(distinct) are logged in to the server at any specific hour.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
then you can write something like this in your base search to filter only logged in events.
<base search> "https://rambo.ixngames.com/start.action" | rex field=_raw "\[BreakssFogFilter\]\s(?<user>\w+)" | timechart span=1h dc(user)
If this solves your problem. accept the answer to close this question.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mayurr98
You Sir, are a genius !
Accepting your Answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this.
| rex field=_raw "\w+\]\s(?<user_name>\w{7})\s"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
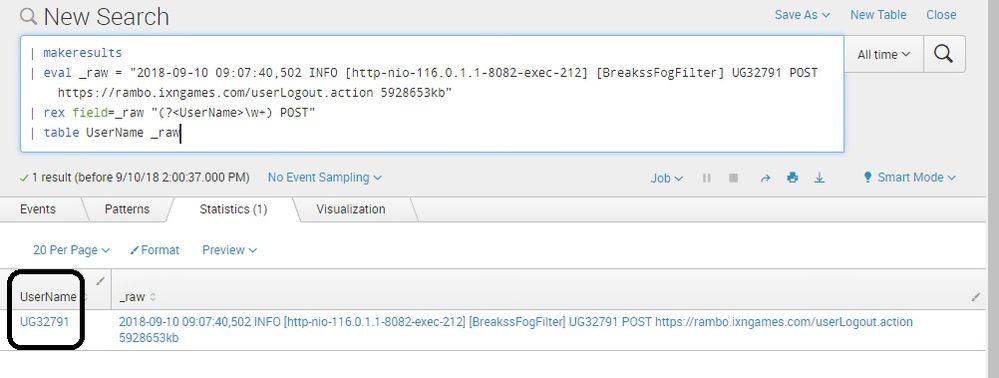
Please check this rex query... as i dont have logs, stats dc wont work on this SPL.. you can test it on your splunk..
| makeresults
| eval _raw = "2018-09-10 09:07:40,502 INFO [http-nio-116.0.1.1-8082-exec-212] [BreakssFogFilter] UG32791 POST https://rambo.ixngames.com/userLogout.action 5928653kb"
| rex field=_raw "(?<UserName>\w+) POST"
| table UserName _raw
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@inventsekar
Could you help parse the user name from this event, the user name being gz71606.
2018-09-10 11:24:33,555 INFO [http-nio-124.0.0.1-8082-exec-155] [MyfaultAuthenticator] login : 'gz71606' could not be authenticated with the given password
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex field=_raw "\slogin\s\:\s\'(?<user>\w+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mayurr98
This is perfect.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
something like <your index>| rex field=_raw "\s\[BreakssFogFilter](?<user>.*?)P" |timechart span=1h count by user