- News & Education
- :
- Blog & Announcements
- :
- Product News & Announcements
- :
- Security | I Am The Snake Now: Analysis of Snake M...
Security | I Am The Snake Now: Analysis of Snake Malware
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark Topic
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The Snake implant is a highly advanced cyber espionage tool, developed and employed by Russia's Federal Security Service's (FSB) Center 16 for persistent intelligence gathering on important targets. They established a clandestine global peer-to-peer network of Snake-infected computers to carry out operations. This network includes relay nodes that facilitate encrypted and fragmented traffic between Snake implants and FSB's targets, designed to evade detection and data collection.
Snake infrastructure has been identified in over 50 countries across all continents, including the US and Russia. While its infrastructure spans all sectors, Snake's targeting is tactical and intentional. FSB has leveraged Snake globally to extract sensitive intelligence from key targets like government networks, research establishments, and journalists. For instance, they used Snake to access and leak confidential diplomatic documents from a victim in a NATO country. Within the US, FSB has targeted sectors such as education, small businesses, media, government facilities, financial services, critical manufacturing, and communications.
For more information on FSB and Russian state-sponsored cyber activity, please see the joint advisory Russian State-Sponsored and Criminal Cyber Threats to Critical Infrastructure and CISA’s Russia Cyber Threat Overview and Advisories webpage.
This blog provides an overview of the process the Splunk Threat Research Team used to develop Atomic Simulations with ChatGPT based on the indicators provided in the report and simulate the activity. It also provides an overview of new security content developed to identify adversaries. You can find a more detailed outline of how the team utilized ChatGPT to develop Atomic Simulations in the attached document.
Leveraging IOCs to Build Atomic Simulations and Content
Within the report there are 4 main Host-Based Detections described in plain English, however no malicious samples were provided. The Splunk Threat Research Team looked at each as if they were software requirements and prompted ChatGPT to build Atomic Simulations which met these requirements. Note that most of our interactions with ChatGPT were conversational - we did not typically accept the first response from ChatGPT, but worked with it to refine the result until we had something that more closely aligns with the requirement.
After development, we tested the Atomic Simulations using Splunk Attack Range, an easy-to-use and open source tool that can automatically configure and deploy a full Splunk Environment, including endpoints, in minutes. Attack Range is the perfect tool for simulating and understanding attacks since it forwards log data to a Splunk instance out-of-the-box.
Below is a breakdown of each host-based detection and corresponding indicators, Atomic Simulation, and resulting security content.
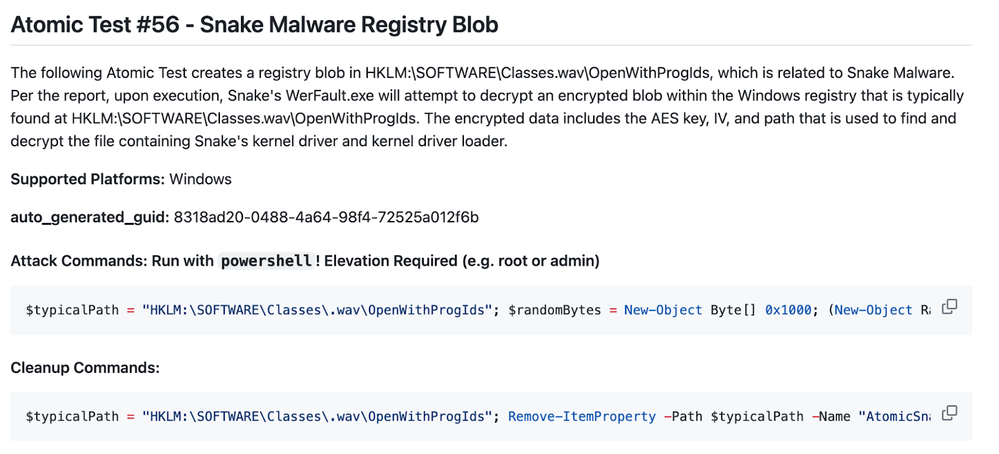
Registry Blob
Indicators of Compromise:
The registry blob is generally found at the location listed below. If it is not present at its typical location, the registry blob can be found by searching the full registry for a value of at least 0x1000 bytes in size and entropy of at least 7.9.
- Typical Name: Unknown (RegBlob)
- Typical Path: HKLM\SOFTWARE\Classes\.wav\OpenWithProgIds
- Characteristics: High Entropy
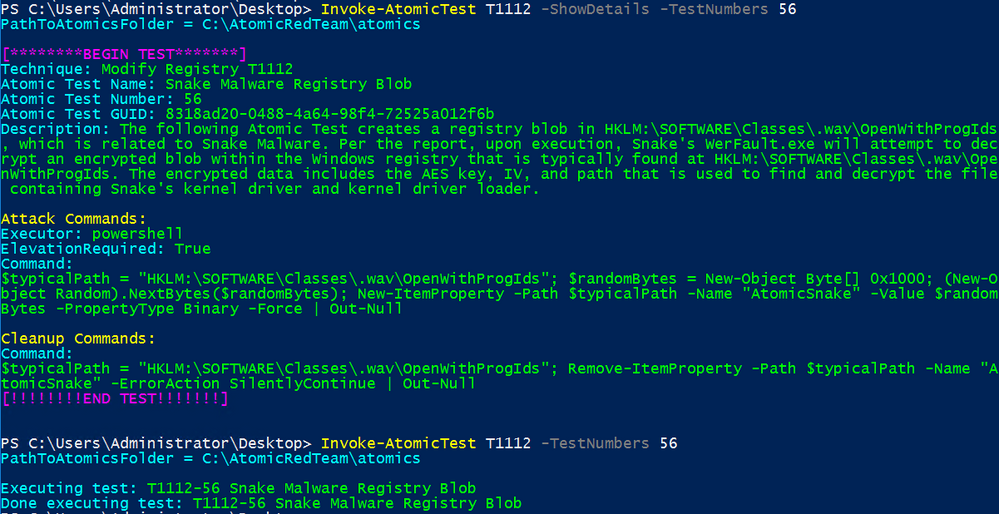
The final result in the Atomic Red Team page T1112:
With Invoke-AtomicRedTeam, we ran this simulation
Invoke-AtomicTest T1112 -TestNumbers 56 -showdetailsbrief
Invoke-AtomicTest T1112 -TestNumbers 56
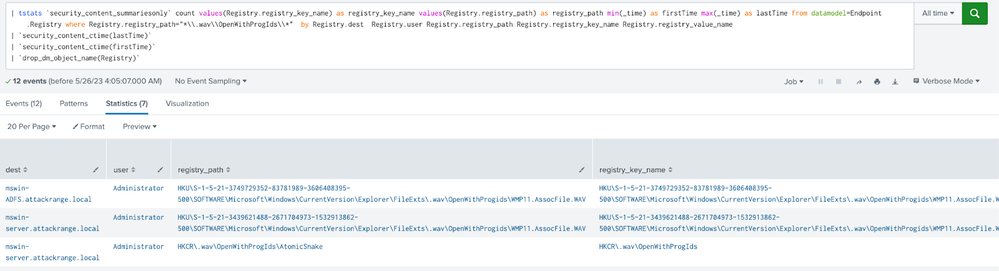
Splunk security content:
Windows Snake Malware Registry Modification wav OpenWithProgIds
This analytic identifies the registry being modified at .wav\OpenWithProgIds\, which is related to the Snake Malware campaign. Upon execution, Snake's WerFault.exe will attempt to decrypt an encrypted blob within the Windows registry that is typically found at HKLM:\SOFTWARE\Classes.wav\OpenWithProgIds. The encrypted data includes the AES key, IV, and path that is used to find and decrypt the file containing Snake's kernel driver and kernel driver loader.
|
| tstats `security_content_summariesonly` count values(Registry.registry_key_name) as registry_key_name values(Registry.registry_path) as registry_path min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Registry where Registry.registry_path="*\\.wav\\OpenWithProgIds\\*" by Registry.dest Registry.user Registry.registry_path Registry.registry_key_name Registry.registry_value_name | `security_content_ctime(lastTime)` | `security_content_ctime(firstTime)` | `drop_dm_object_name(Registry)` |
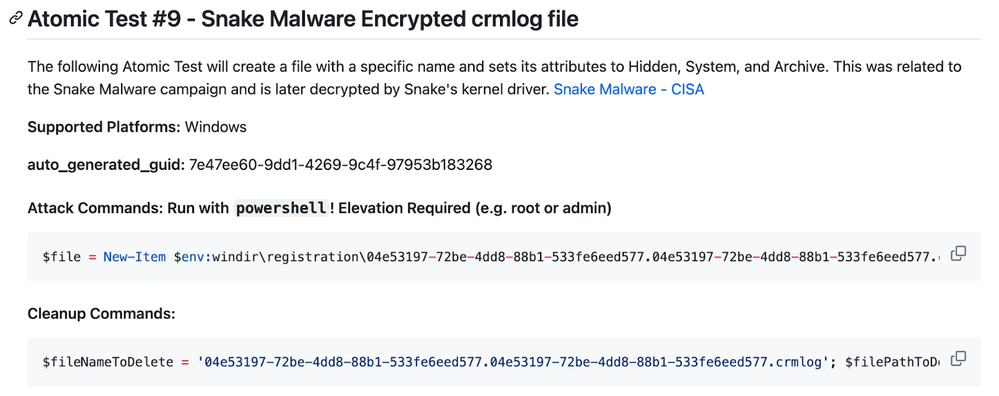
Queue File
The next host-based indicator provided in the report was the queue file, which is described as “The last host-based artifact to discuss is the Queue File. Typically, this file has been found within the %windows%\Registration directory with the format of .crmlog, and is decrypted by Snake’s kernel driver. Due to the complexity and importance of the Queue File, its details are discussed at length in the following subsection.”
Indicator of compromise:
- Typical Name: < RANDOM_GUID >..crmlog
- Typical Path: %windows\registration\
- Unique Characteristics: High Entropy, file attributes of hidden, system, and archive
- Role: Snake Queue File
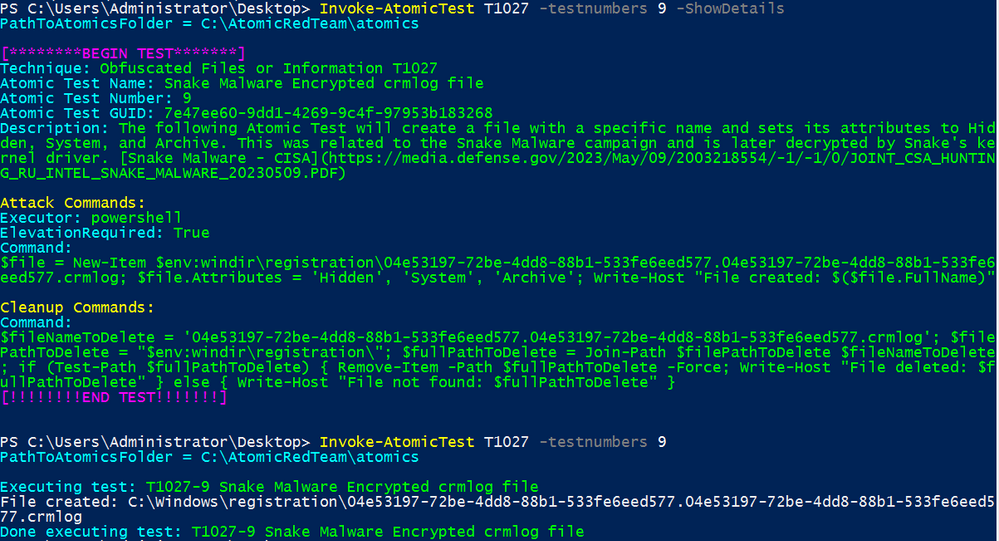
Atomic Red Team test, T1027 test number 9, simulates the activity.
Running the following with Invoke-AtomicTest:
Invoke-AtomicTest T1027 -testnumbers 9 -ShowDetails
Invoke-AtomicTest T1027 -testnumbers 9
Splunk security content:
Windows Snake Malware File Modification Crmlog
This analytic identifies a .crmlog written to windows\registration. Per the report, typically, this file has been found within the %windows%\Registration directory with the format of <RANDOM_GUID>.<RANDOM_GUID>.crmlog and is decrypted by Snake's kernel driver.
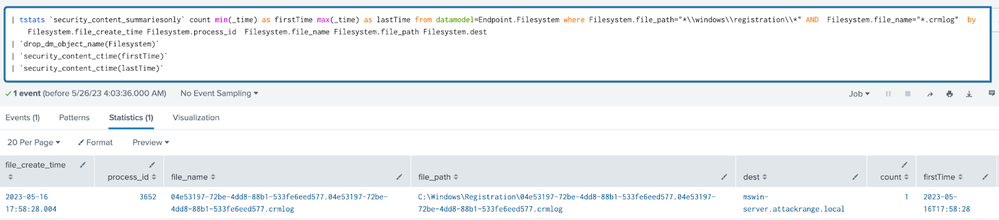
|
| tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Filesystem where Filesystem.file_path="*\\windows\\registration\\*" AND Filesystem.file_name="*.crmlog" by Filesystem.file_create_time Filesystem.process_id Filesystem.file_name Filesystem.file_path Filesystem.dest | `drop_dm_object_name(Filesystem)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` |
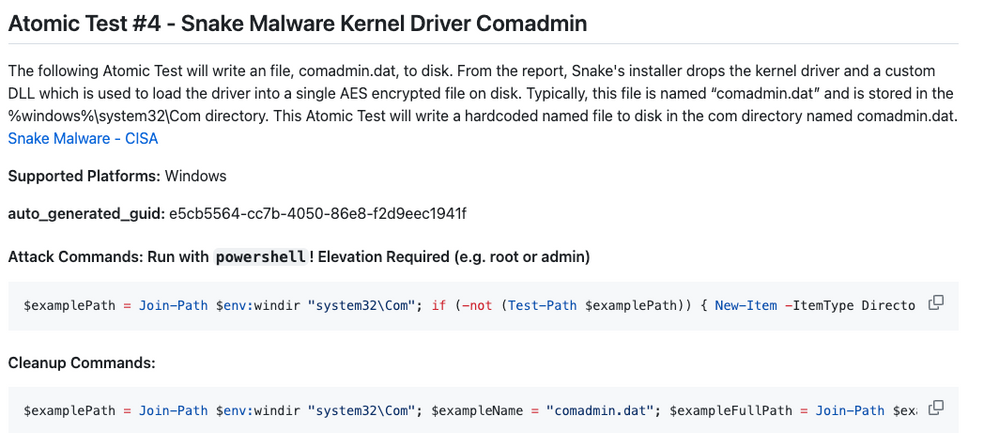
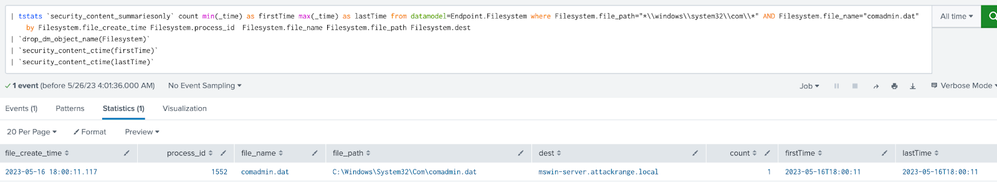
Comadmin
Per the CISA report, Snake’s installer drops the kernel driver and a custom DLL which is used to load the driver into a single AES encrypted file on disk. Typically, this file is named “comadmin.dat” and is stored in the %windows%\system32\Com directory. The STRT took this as part of the requirement that we shared with ChatGPT to generate this behavior.
Indicator of compromise:
- Typical Name: comadmin.dat
- Typical Path: %windows%\system32\Com
- Unique Characteristics: High Entropy
- Role: Houses Snake’s kernel driver and the driver’s loader
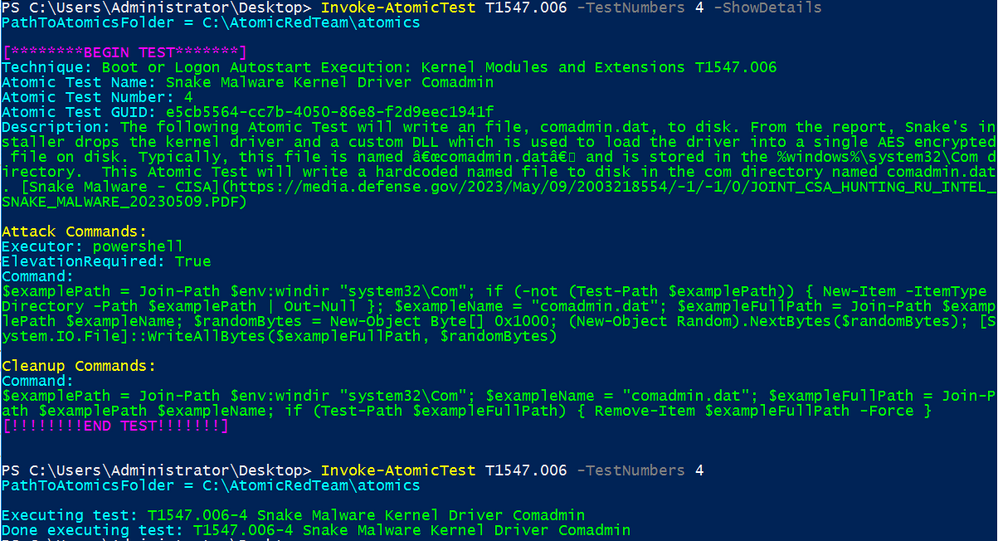
The Atomic Test is under T1547.006 and may be simulated with the following command:
Invoke-AtomicTest T1547.006 -TestNumbers 4
Invoke-AtomicTest T1547.006 -TestNumbers 4 -ShowDetails
Invoke-AtomicTest T1547.006 -TestNumbers 4
Splunk security content:
Windows Snake Malware Kernel Driver Comadmin
This analytic identifies the comadmin.dat file written to disk, which is related to Snake Malware. From the report, Snake's installer drops the kernel driver and a custom DLL which is used to load the driver into a single AES encrypted file on disk. Typically, this file is named comadmin.dat and is stored in the %windows%\system32\Com directory.
|
| tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Filesystem where Filesystem.file_path="*\\windows\\system32\\com\\*" AND Filesystem.file_name="comadmin.dat" by Filesystem.file_create_time Filesystem.process_id Filesystem.file_name Filesystem.file_path Filesystem.dest | `drop_dm_object_name(Filesystem)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` |
Werfault
Indicator of compromise:
- Typical Name: Werfault.exe
- Typical Path: %windows%\WinSxS\x86_microsoft-windowserrorreportingfaults_31bf3856ad364e35_4.0.9600.16384_none_a13f7e283339a0502\
- Unique Characteristics: Icon is different than that of a valid Windows Werfault.exe file
- Role: Persistence mechanism
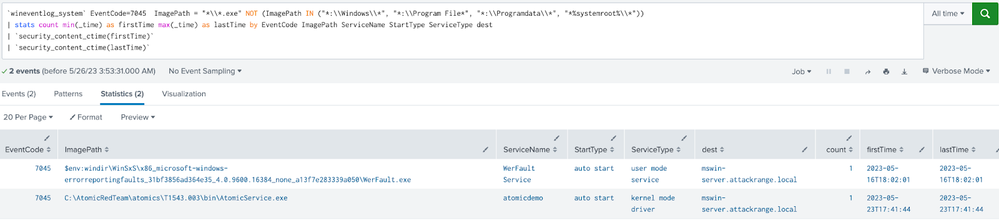
We used the EventID 7045 to develop the analytics that monitor service creations. The Snake malware was found to register a service located in the WinSxS path with a specific name. Holistically, it’s best to monitor for any new service creations across the fleet and monitor for non-standard paths or binary names.
Splunk security content:
Windows Service Created with Suspicious Service Path
|
`wineventlog_system` EventCode=7045 ImagePath = "*\\*.exe" NOT (ImagePath IN ("*:\\Windows\\*", "*:\\Program File*", "*:\\Programdata\\*", "*%systemroot%\\*")) | stats count min(_time) as firstTime max(_time) as lastTime by EventCode ImagePath ServiceName StartType ServiceType dest | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` |
This analytic identifies the creation of a new service that does not occur within these directories (":\Windows\", ":\Program File", ":\Programdata\", "%systemroot%\"). For Snake malware, it would create its service in the WinSxS path, which is uncommon.
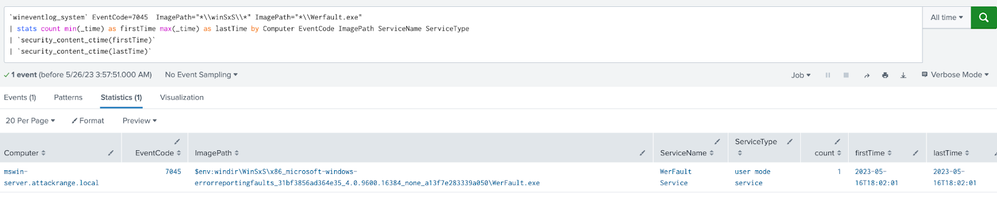
Windows Snake Malware Service Create
For Snake malware, we created a more precise analytic based on the Snake behaviors outlined in the report and what we created during our simulation.
|
`wineventlog_system` EventCode=7045 ImagePath="*\\windows\\winSxS\\*" ImagePath="*\Werfault.exe" | stats count min(_time) as firstTime max(_time) as lastTime by Computer EventCode ImagePath ServiceName ServiceType | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` |
Why Should You Care?
This security content enables Splunk customers to identify Snake Malware and the process outline helps the community understand how LLM tools like ChatGPT can recreate endpoint artifacts without malicious software samples. By understanding the behaviors, the Splunk Threat Research Team was able to generate telemetry and datasets to develop and test Splunk detections designed to defend and respond against this threat.
Learn More
You can find the latest content about security analytic stories on GitHub and in Splunkbase. Splunk Security Essentials also has all these detections available via push update.
For a full list of security content, check out the release notes on Splunk Docs.
Feedback
Any feedback or requests? Feel free to put in an issue on GitHub and we’ll follow up. Alternatively, join us on the Slack channel #security-research. Follow these instructions if you need an invitation to our Splunk user groups on Slack.
Contributors
We would like to thank Michael Haag, Eric McGinnis and Teoderick Contreras for authoring this document and the entire Splunk Threat Research Team for their contributions: Mauricio Velazco, Lou Stella, Bhavin Patel, Rod Soto, and Patrick Bareiss.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Detecting Remote Code Executions With the Splunk Threat Research Team
Observability | Use Synthetic Monitoring for Website Metadata Verification
More Ways To Control Your Costs With Archived Metrics | Register for Tech Talk
-
Customer Experience
10 -
Data Stream Processor
1 -
Edge Processor
2 -
OpenTelemetry
1 -
other
7 -
Product Announcements
1 -
Splunk APM
20 -
Splunk Cloud Platform
62 -
Splunk Community
1 -
Splunk Enterprise
45 -
Splunk Enterprise Security
43 -
Splunk Ideas
1 -
Splunk Infras Monitoring
17 -
Splunk ITSI
11 -
Splunk Lantern
1 -
Splunk Mission Control
4 -
Splunk Observability Cloud
80 -
Splunk On-Call
2 -
Splunk Security Cloud
21 -
Splunk SOAR
15 -
Splunk UBA
2 -
Splunkbase Apps & Add-Ons
16 -
User Groups
1
- « Previous
- Next »