Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Other Usage
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Other Usage
- :
- How do I Exclude Blocked IPs from Threat Activity ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do I Exclude Blocked IPs from Threat Activity Detected Rule?
cookislands
New Member
06-27-2023
08:49 PM
Hey,
I am wondering how can we modify the below query/rule to exclude IPs that have been blocked by firewall. orig_sourcetype="fortigate_utm".
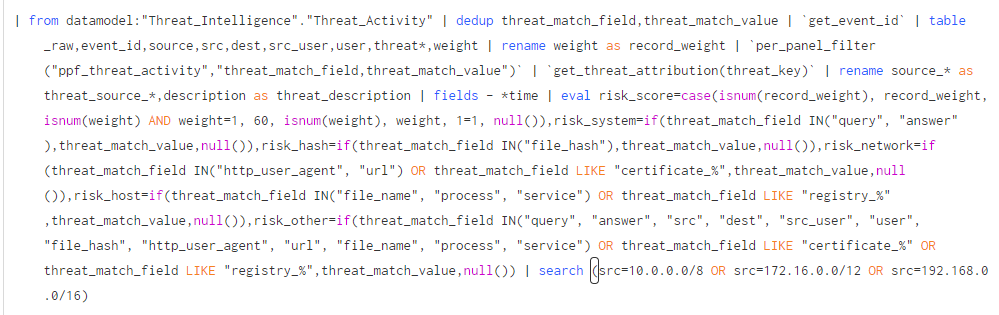
Query:
| from datamodel:"Threat_Intelligence"."Threat_Activity" | dedup threat_match_field,threat_match_value | `get_event_id` | table _raw,event_id,source,src,dest,src_user,user,threat*,weight | rename weight as record_weight | `per_panel_filter("ppf_threat_activity","threat_match_field,threat_match_value")` | `get_threat_attribution(threat_key)` | rename source_* as threat_source_*,description as threat_description | fields - *time | eval risk_score=case(isnum(record_weight), record_weight, isnum(weight) AND weight=1, 60, isnum(weight), weight, 1=1, null()),risk_system=if(threat_match_field IN("query", "answer"),threat_match_value,null()),risk_hash=if(threat_match_field IN("file_hash"),threat_match_value,null()),risk_network=if(threat_match_field IN("http_user_agent", "url") OR threat_match_field LIKE "certificate_%",threat_match_value,null()),risk_host=if(threat_match_field IN("file_name", "process", "service") OR threat_match_field LIKE "registry_%",threat_match_value,null()),risk_other=if(threat_match_field IN("query", "answer", "src", "dest", "src_user", "user", "file_hash", "http_user_agent", "url", "file_name", "process", "service") OR threat_match_field LIKE "certificate_%" OR threat_match_field LIKE "registry_%",threat_match_value,null()) | search (src=10.0.0.0/8 OR src=172.16.0.0/12 OR src=192.168.0.0/16)
Get Updates on the Splunk Community!
Index This | What’s a riddle wrapped in an enigma?
September 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
BORE at .conf25
Boss Of Regular Expression (BORE) was an interactive session run again this year at .conf25 by the brilliant ...
OpenTelemetry for Legacy Apps? Yes, You Can!
This article is a follow-up to my previous article posted on the OpenTelemetry Blog, "Your Critical Legacy App ...