- Find Answers
- :
- Splunk Administration
- :
- Monitoring Splunk
- :
- Symantec End point Protection Dashboard
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
We have installed and configured Splunk Add on for symantec endpoint protection successfully.
Splunk has started receiving logs (index=symantec) but we can see nothing on its symantec dashboard as it showing No Results found.
We restarted splunk but it didn't worked.
Please help.
Regards,
Rahul
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rahul2gupta ,
as you can see, you have a macro inside another macro, so you have to open the sep_index macro and see what's containing.
If the symantec index isn't present, you have to insert in it.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rahul2gupta ,
check if in the searches there the filter "index=symantec".
If not, Splunk run search on the default indexes and probably sysmantec isn't one of them.
You have two solutions:
- insert "index=symantec" in every search (in this case it's better to create an eventtype containing this filter);
- add symantec to the default indexes for the roles that have to use the dashboards.
I don't like the second one even if is quicker to implement: I prefer the first because it need more time to implement, but it has more performaces.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
We have already inserted index="symantec" in inputs.conf.
[monitor://%SEPM_HOME%\data\dump\scm_admin.tmp]
sourcetype = symantec:ep:admin:file
index=symantec
disabled = false
[monitor://%SEPM_HOME%\data\dump\agt_behavior.tmp]
sourcetype = symantec:ep:behavior:file
index=symantec
disabled = false
[monitor://%SEPM_HOME%\data\dump\scm_agent_act.tmp]
sourcetype = symantec:ep:agent:file
index=symantec
disabled = false
[monitor://%SEPM_HOME%\data\dump\scm_policy.tmp]
sourcetype = symantec:ep:policy:file
index=symantec
disabled = false
But although we are getting nothing on dashboard.
Regards,
Rahul
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rahul2gupta ,
if you run a simple search index="symantec", what are the results?
if you have events, the problem is in the dashboard, and I think that's the one I described below.
I you haven't events there's a problem in input.
What's your situation?
Only one additional heck: are the users using the dashboard administrators? if not, check if thei role has the grants on the symantec index.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
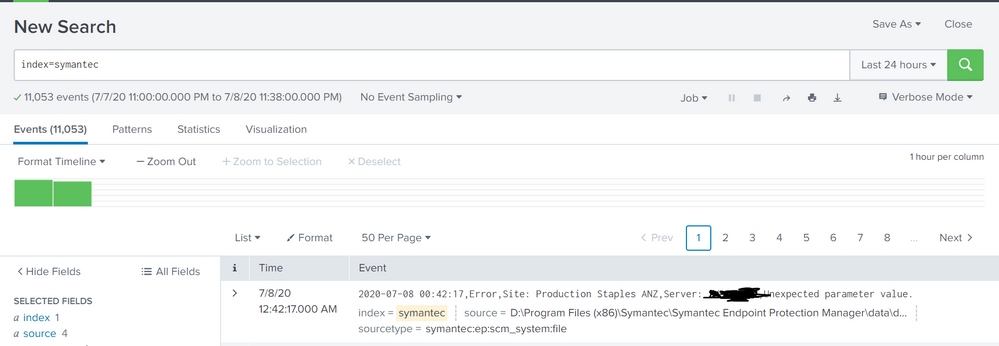
Hi @gcusello ,
When we run the query index="symantec",we get the following output.
Only one additional heck: are the users using the dashboard administrators? if not, check if there role has the grants on the symantec index. -- How to check this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @rahul2gupta ,
running a search and having results means that your user has the grants to access the index, but you probably are an administrator, maybe the users has different roles, so check in [Settings -- Roles] if the roles associated to the users that are using the dashboard has access to the index.
Anyway, the presence of logs in index=symantec means that input is correct, now, you have to check why data aren't displayed in dashboard.
You can open in search one of dashboard panels clicking on the magnifying glass (bottom right).
Then you can check if in the main search there is or not "index=symantec" so it's possible to understand where's the problem.
If you want help, share one of these searches.
To avoid path problems, go in [Settings -- Roles -- <your_role> -- Indexes] and flag the symantec index in both the columns (Included and Default).
In few words, if you don't explain in your search the index to search, Splunk searches on all the indexes in the default path, for this reason I always prefer to insert index in the main search.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
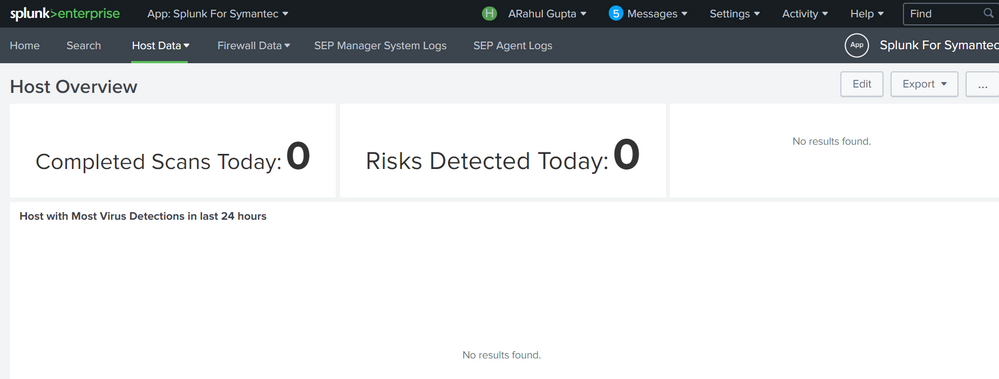
Hi @gcusello ,
This is the dashboard of splunk for symantec.
I checked for "Host with Most Virus Detections in last 24 hours" in main search.
What should i do now?
Regards,
Rahul
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rahul2gupta ,
dashboard panel is populated using a macro, so you have to go in [Settings -- Advanced Search -- Search Macros] and open in edit the macro contained in your panel (in your screenshot "host_overview_most_viruses_last_24hours"), viewing if there's the index in the main search.
If not (I think so) add it and save the macro.
Otherwise you can add the symantec index to the default path as I described in a previous answer.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
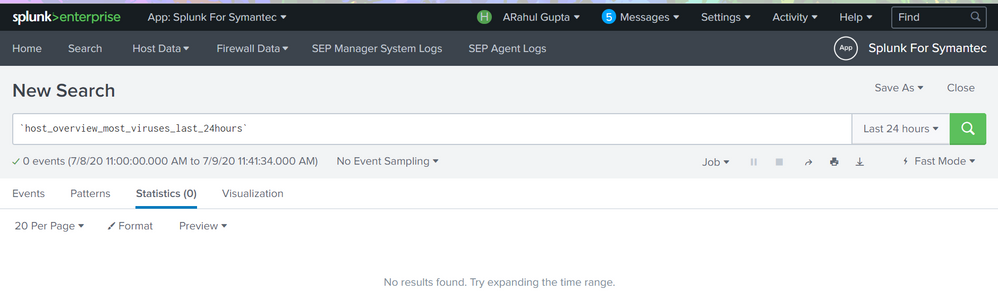
Hi @gcusello ,
Following is the search.
`sep_index` `sep_risk_sourcetype` action=allowed OR action=deferred AND risk_type="Virus found" | rename actual_action as "Action" dest_nt_host as "Host" dest_ip as "Host IP" user as "User" risk_type as "Detection Type" signature as "Malware Name" | stats count by Host "Host IP" User | sort -count
What modifications do I need to do.
Regards,
Rahul
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rahul2gupta ,
as you can see, you have a macro inside another macro, so you have to open the sep_index macro and see what's containing.
If the symantec index isn't present, you have to insert in it.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
Thank you very much for your continuous support.This problem is resolved.
Regards,
Rahul
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content