- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Knowledge Management
- :
- sitimechart
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
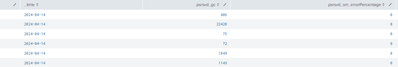
While using sitimechart instead of timechart - The data has been changed.
I would like to calculate an error percentage but the system shows 0 or fields count.
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you would just like to make a timechart, then the timechart command should fit your need better than the sitimechart command. The sitimechart is intended for preparing the data to insert into a summary index so that later on it can be timecharted from the summary index.
Using just timechart:
<your search>
| timechart span=1d avg(errorPercentage) as errorPercentage by Process
If you would like to gather data now into a summary index to produce a timechart very quickly in a later search, you can use sitimechart:
<your search>
| sitimechart span=1d avg(errorPercentage) as errorPercentage by Process
| collect index=yoursummaryindex
Then in a later search:
index = yoursummaryindex <some filter, e.g. for Process=*>
| timechart span=1d avg(errorPercentage) as errorPercentage by Process
The docs page describes the sitimechart usage, but does not explain the meaning of the created fields: https://docs.splunk.com/Documentation/Splunk/9.2.0/SearchReference/Sitimechart
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you would just like to make a timechart, then the timechart command should fit your need better than the sitimechart command. The sitimechart is intended for preparing the data to insert into a summary index so that later on it can be timecharted from the summary index.
Using just timechart:
<your search>
| timechart span=1d avg(errorPercentage) as errorPercentage by Process
If you would like to gather data now into a summary index to produce a timechart very quickly in a later search, you can use sitimechart:
<your search>
| sitimechart span=1d avg(errorPercentage) as errorPercentage by Process
| collect index=yoursummaryindex
Then in a later search:
index = yoursummaryindex <some filter, e.g. for Process=*>
| timechart span=1d avg(errorPercentage) as errorPercentage by Process
The docs page describes the sitimechart usage, but does not explain the meaning of the created fields: https://docs.splunk.com/Documentation/Splunk/9.2.0/SearchReference/Sitimechart