- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Knowledge Management
- :
- Splunk CIM Network Traffic issue with the field ac...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have adjusted one of the FWs to be CIM compline.
I have 2 type of action parameters:
- one called "Action" that contains 100% of the values.
- one called "action" that contains 3% of the values.
Link: https://docs.splunk.com/Documentation/CIM/5.1.1/User/NetworkTraffic
The query is:
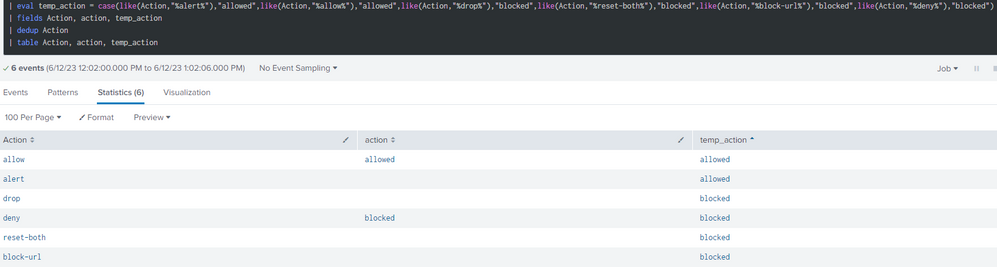
case(like('Action',"%alert%"),"allowed",like('Action',"%allow%"),"allowed",like('Action',"%drop%"),"blocked",like('Action',"%reset-both%"),"blocked",like('Action',"%block-url%"),"blocked",like('Action',"%deny%"),"blocked")
It works when I query this in the SPL command line however is not works when it rans as a calculated field.
Does Someone familiar with this issue? I will really appreciate your help 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
enter in [Settings > dataModels] and choose the Network Traffic DataModel.
if acelerated (it should be), disable acceleration.
Click on Add Field (button on the right side of the dashboard.
Click on Eval Expression and insert the expression.
Enable accelaration.
Obviously this new field doesn't contain any value for old records: you can rebuild Data Model or wait for new records.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
why do you use apex for field names?
please try:
case(like(Action,"%alert%"),"allowed",like(Action,"%allow%"),"allowed",like(Action,"%drop%"),"blocked",like(Action,"%reset-both%"),"blocked",like(Action,"%block-url%"),"blocked",like(Action,"%deny%"),"blocked")in calculated fields.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Gcusello,
I have changed it and waited for like 30 minutes and still not works unfortunately.
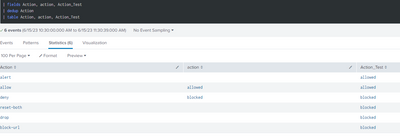
Here is the chart that it currently generates:
You can see that the calculated field is not works (the permissions are global it should work)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
if the values of Action are only one word, you don't need to use like, but your can use equal:
case(Action="alert","allowed",Action="allow","allowed",Action="drop","blocked",Action="reset-both","blocked",Action="block-url","blocked",Action="deny","blocked")Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello,
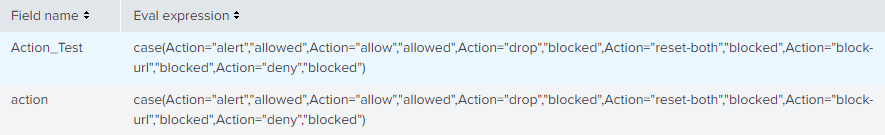
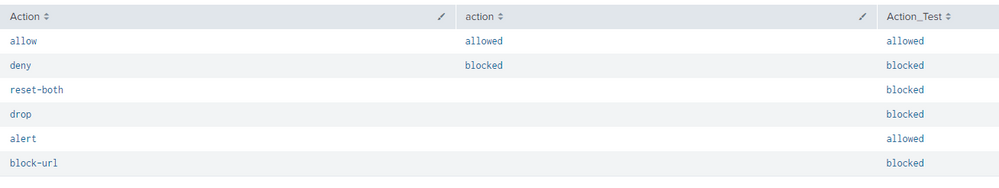
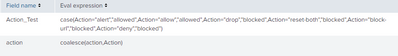
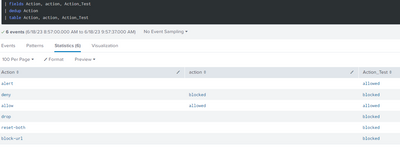
I have tried what you meant in the previous suggest unfortanually this did not worked as well, I have created additional parameter called Action_Test to see if the name of the parameter is might be the issue and this are the results:
Seems like the source issue comes from the name itself, cause your query defiantly works but not when I try to add this to the action field..
Do you might have another idea how to resolve this case? 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
are you sure that the action field isn't already existent?
try to make an eval
| eval action=coalesce(Action_Test,action)or a rename
| rename Action_Test As actionCiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello,
The value indeed exist already from the vendor itself he provide to values "Action" and "action".
The Action consist 100% of the values and action consists only 3%, There fore I wanted to transfer all the values to be in the action field as supposed to be according to the Network Traffic Data Model.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
if you want to have the action value when present and the Action value when action is empty, please try this:
| eval action=coalesce(action,Action_Test)before ina a search, then in a calculated field
ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello,
First of all I really appreciate your help in this case!
Secondly, I have tried what you meant; It is working if i query this from the command line.
However, Is not working if I put it as a calculated field that is my major problem If I want my index to be complied with the Data Model (Traffic Network).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
this could not be a problem because in the datamodel definition you can insert an eval calculation.
Anyway, did you tried to create also a calculated field with the coalesce?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello,
sorry for not replying I had an issue to sign in, In the last 2 days.
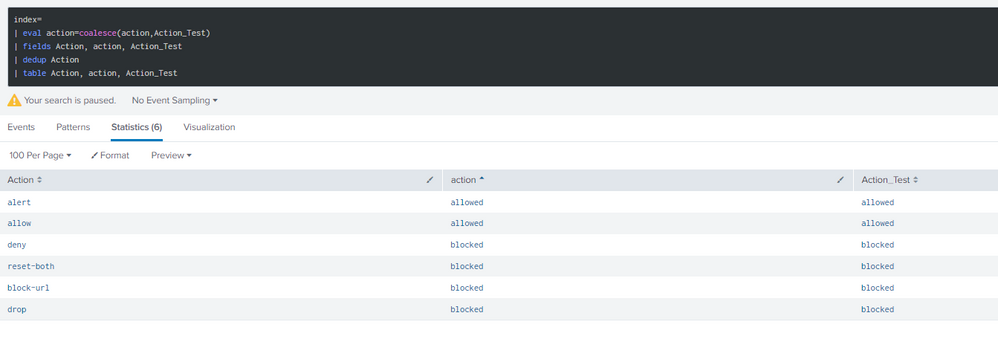
I did made the coalesce that you have sent and it still not works.
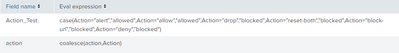
This is the calculated fields:
Looks like the actual issue is the fact the the field action already exist and therefore can not calculate this field as supposed to be, Since the attempt of Action_Test did worked.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal ,
please try this calculated field:
if(action="allowed" OR action="blocked",action,Action)if it doesn't run, opena a case to Splunk Support.
Ciao.
giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see, Good to know 🙂
Yeah I have added this as a calculated field still not works..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
soryy i I forgot it: did you tried:
if(action="allowed" OR action="blocked",action,Action)?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
Can you please explain how is it supposed to help in our case?
under what value should I calculate this fields? action?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
as you displayed, the action field coud have the values "alowed" or "blocked".
If it has one of these values, the value is taken, otherwise to the action field os assigned the value from the Action field.
Try this approach to see in in this case the calculated field works as it should do.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello,
I have tried what you have suggested I don't see it is actually works..
I see the Action_Test works perfectly I think the fact that we already have a value called action is the reason why it breaks, Do you think it is possible to be the reason?
Thanks,
Eyal
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Eyal,
did you tested my last solution?
If it continues to fail I haven't any solution!
I'm sorry!
Last try: did you tried to add my last solution, directly in the data Model Add field feature, not passing through Calculated fields?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello,
Can you please provide me the steps how do I use the Add field feature directly in the data Model?
I tried to find it without any success, I would like try this solution before we give up 🙂
Thanks!!