Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Knowledge Management
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Knowledge Management
- :
- Question on extract the fields from the lines foll...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Question on extract the fields from the lines following a particular string
prettysunshinez
Explorer
07-14-2021
06:49 AM
Hi,
I would like to extract the details that is present in the event followed by the event which the search string is present.Below is a sample data and the expected output.[7/14/21 3:00 CDT] 3 IDs are found for the type 234456 and for the subtype 12334^12344
[7/14/21 3:00 CDT] It is being sent to will@sons
[7/14/21 3:01 CDT] It is being sent to william@sons
[7/14/21 3:01 CDT] It is being sent to heather@sons
Expected Output
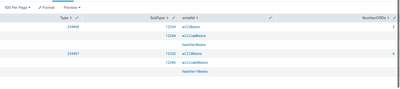
Type Subtype ID "No.of ID's"
234456 12334 will@sons 3
12344 william@sons
heather@sons
Thanks in advance!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
07-14-2021
09:43 AM
Can you please try this?
YOUR_SEARCH
| rex field=_raw "(?<NumberOfIDs>\d*) IDs are found for the type (?<Type>\d*) and for the subtype (?<SubType>.*)"
| rex field=_raw "sent to (?<emailId>.*)" | filldown Type SubType NumberOfIDs
| streamstats count by Type
| eval SubType=mvindex(split(SubType,"^"),count-2),Type=if(count=2,Type,null()), NumberOfIDs=if(count=2,NumberOfIDs,null()) | where count!=1
| table Type SubType emailId NumberOfIDsMy Sample Search :
| makeresults | eval raw="[7/14/21 3:00 CDT] 3 IDs are found for the type 234456 and for the subtype 12334^12344|[7/14/21 3:00 CDT] It is being sent to will@sons|[7/14/21 3:01 CDT] It is being sent to william@sons|[7/14/21 3:01 CDT] It is being sent to heather@sons|[7/14/21 3:02 CDT] 4 IDs are found for the type 234457 and for the subtype 12335^12345|[7/14/21 3:02 CDT] It is being sent to will3@sons|[7/14/21 3:03 CDT] It is being sent to william3@sons|[7/14/21 3:03 CDT] It is being sent to heather1@sons"
| eval raw=split(raw,"|")| mvexpand raw | rename raw as _raw
|rename comment as "Upto Now is sample data only"
| rex field=_raw "(?<NumberOfIDs>\d*) IDs are found for the type (?<Type>\d*) and for the subtype (?<SubType>.*)"
| rex field=_raw "sent to (?<emailId>.*)" | filldown Type SubType NumberOfIDs
| streamstats count by Type
| eval SubType=mvindex(split(SubType,"^"),count-2),Type=if(count=2,Type,null()), NumberOfIDs=if(count=2,NumberOfIDs,null()) | where count!=1
| table Type SubType emailId NumberOfIDs
Thanks
KV
▄︻̷̿┻̿═━一
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
Get Updates on the Splunk Community!
Upcoming Webinar: Unmasking Insider Threats with Slunk Enterprise Security’s UEBA
Join us on Wed, Dec 10. at 10AM PST / 1PM EST for a live webinar and demo with Splunk experts! Discover how ...
.conf25 technical session recap of Observability for Gen AI: Monitoring LLM ...
If you’re unfamiliar, .conf is Splunk’s premier event where the Splunk community, customers, partners, and ...
A Season of Skills: New Splunk Courses to Light Up Your Learning Journey
There’s something special about this time of year—maybe it’s the glow of the holidays, maybe it’s the ...