Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Knowledge Management
- :
- Error in 'lookup' command: Must specify one or mor...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Error in 'lookup' command: Must specify one or more lookup fields.
I have a lookup table with CVE listed which I dont want to be in our report so we have made the lookup table and adding it to the search
| table Severity, "EC2 Instance ID", "EC2 Instance Name", "Rules Package", Rule, CreatedAt, Links, title, description, recommendation, numericSeverity | lookup ignore_cve.csv
But I am getting an error that " Error in 'lookup' command: Must specify one or more lookup fields."
So Do I have add something else after ignore_cve.csv
Kindly help.@lookup
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have added this " | search NOT [|inputlookup ignore_cve.csv]" but I am still getting all the CVE's which I dont want in my report.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the field name of the CVE in your event results?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rule is the field name.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, so rename your field from the lookup to "Rule":
<yourSearch> NOT [|inputlookup ignore_cve.csv | rename "CVE Number" as Rule | fields Rule]- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am sharing the query with you here so kindly advise.
`aws-inspector-findings` serviceAttributes.assessmentRunArn="*" `aws-inspector-rex-arn` | search (accountId="*") (region="*")| dedup arn| search (severity="*")| spath OUTPUT=agentId assetAttributes.agentId | where isnotnull(agentId)| eval CreatedAt=substr(createdAt, 1, 19) | join type="left" serviceAttributes.rulesPackageArn [search `aws-inspector-runs` arn="*" | dedup rulesPackages{}.arn | rename rulesPackages{}.arn as packageArn, rulesPackages{}.name as packageName| eval row=mvzip(packageArn, packageName, "|") | mvexpand row | rex field=row "(?<packageArn>.*?)\|(?<packageName>.*)" | table packageArn packageName | rename packageArn as "serviceAttributes.rulesPackageArn"]| rename packageName as "Rules Package"| eval Links = if(isnotnull(agentId), "<a id=topology_link>Show in Topology</a> | <a id=ec2_link>Show Instance Details</a>", "") | sort -numericSeverity | join agentId type="left" [search earliest=-1d `aws-description-resource((aws_account_id="*"), (region="*") , "*")` | rename id as agentId ] | rename severity as Severity, id as Rule, agentId as "EC2 Instance ID", tags.Name as "EC2 Instance Name"| fillnull value="N/A" | table Severity, "EC2 Instance ID", "EC2 Instance Name", "Rules Package", Rule, CreatedAt, Links, title, description, recommendation, numericSeverity | search NOT [|inputlookup ignore_cve.csv]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What field name from this search do you want to match against which field name in the lookup?
In general:
<yourSearchReturning <matchField>> NOT [| inputlookup lookupfile.csv | fields <fieldToMatch> | rename <fieldToMatch> as <matchField>]
Of course you only have to rename if the field name in your event search is different from the one in the lookup file.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have used this query at the end of the search and it worked.
| join type=left Rule [inputlookup ignore_cve.csv | eval flag="0"] | search NOT(flag=0) | where isnull(flag)
I also tried your option which you have suggested and please find the result below.
NOT [| inputlookup ignore_cve.csv | fields Rule | rename Rule as CVE] but I am still getting the error though I have used "CVE"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to ensure that the inputlookup subsearch returns a field called "Rule", not CVE.
The field/column you want to match in your lookup is named "CVE Number", so you need to rename that to "Rule" for the NOT condition to work against your events.
NOT [|inputlookup ignore_cve.csv | rename "CVE Number" as Rule | fields Rule]- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
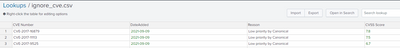
@s2_splunk here is the csv file for your reference and also I will try the suggestion, keep you updated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have followed the below article.
Added this to my search :
NOT [|inputlookup ignore_cve.csv | fields CVE Number, DateAdded, Reason, CVSS Score]
But again getting this error : Error in 'table' command: Invalid argument: 'DateAdded=2021-09-09'
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You probably want something like
index=xyz NOT [ inputlookup ignore_cve.csv ] | table ....lookup is intended for 'translating' things, like key in, value out.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @s2_splunk Thanks for your response and yes this is what I am looking for but seems one more error I am getting " Error in 'table' command: Invalid argument: 'CVE Number"..
CVE Number is my column name and table with vulnerabilities which I dont want to be in my search.
Regards,
Neelesh Tiwari
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try adding quotes to that field "CVE Number" name or remove the space from the csv header? Without seeing the exact layout of your csv file and the current query, it's difficult to provide more advice. Maybe share header row and first couple of lines of your csv?