- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk Universal Forwarder Windows Install Local User
Hi
According to the Splunk Docs from version 9.1:
"the installer creates a virtual account as a "least privileged" user called splunkfwd"
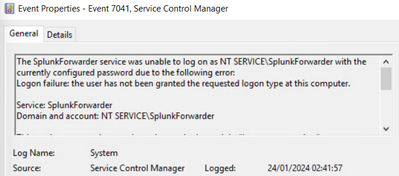
After an upgrade to version 9.1.2 I am having trouble with the UF autostarting. Looking at Windows Event Logs I can see the following error:
Which suggests the account is actually "SplunkForwarder" not "splunkfwd"
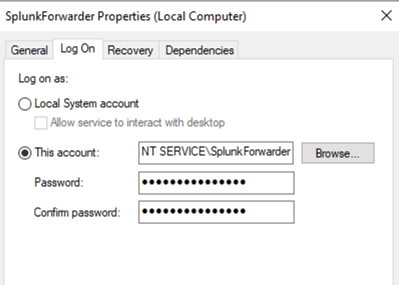
When I check the Windows Service Log On user I also see the user "SplunkForwarder":
And "SplunkForwarder" is also the only Splunk related user I can see when I run the following command to list all users:
get-service | foreach {Write-Host NT Service\$($_.Name)}
Can someone confirm that the Doc is incorrect and the virtual account created is in fact SplunkForwarder? Or is "splunkfwd" created somewhere else?
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
based on your screenshots it’s just like you said and docs told this wrongly. You should leave comment/ corrections on that doc page. They are happy to get feedback and will correct this sooner or later.
On Linux that user is splunkfwd as docs told.
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the process of raising a Splunk case I was able to find a Knowledge Article (000012459) that explained how to install the Splunk UF as the LocalSystem user as was previously standard:
For silent installation, a Windows universal forwarder from the command line to use LOCAL_SYSTEM account (which is not a security best practice) looks like below:
msiexec.exe /i splunkforwarder-9.1.2-b6b9c8185839-x64-release.msi LAUNCHSPLUNK=0 AGREETOLICENSE=Yes GENRANDOM PASSWORD=1 SERVICESTARTTYPE=auto USE_VIRTUAL_ACCOUNT=0 USE_LOCAL_SYSTEM=1 /quiet
by using flags: USE_VIRTUAL_ACCOUNT=0 USE_LOCAL_SYSTEM=1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@a_kearney - I have not upgraded Splunk UF to the latest version yet.
I recommend you create a Splunk support ticket for a quick answer to your question.
I hope this helps!!! Kindly upvote if it does!!