Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- windows event Ids not parsing all events correctly
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
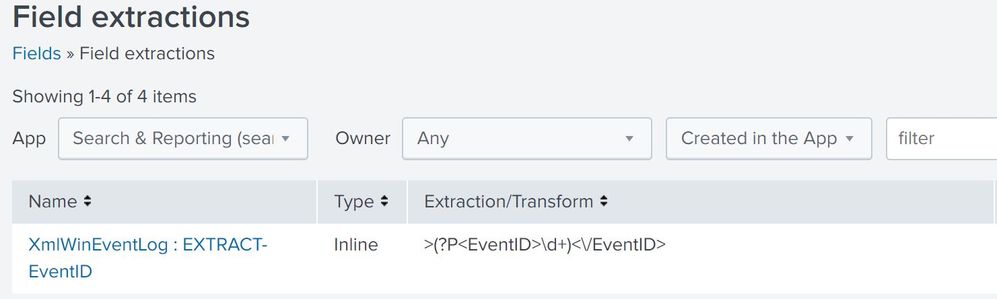
I have tried to create a field extractor with the regx ">(?P\d+)<\/EventID>" as noted here https://visibleninja.guru/problemwith-eventid-field-extraction-in-windows_ta-app/.
This did not seem to parse out the event ids correctly. Where else should I put the regx key?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should be using the Splunk Add-on for Microsoft Windows AKA Splunk_TA_windows here:
https://splunkbase.splunk.com/app/742/
When you use this, all of the field extractions should be in place and work fine. If not, then open a support case with Splunk.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should be using the Splunk Add-on for Microsoft Windows AKA Splunk_TA_windows here:
https://splunkbase.splunk.com/app/742/
When you use this, all of the field extractions should be in place and work fine. If not, then open a support case with Splunk.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How are you ingesting the Windows Event logs? Have you taken a look at the docs for both getting data in the the Windows TA? The TA takes care of the extraction of all your needed fields.
Skalli
