Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- break a json log
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi at all,
I have a json log that in a single json contains many events:
{"response":{"caseEvents":[{"eventDetails":{"eventDescription":"SCT","eventId":"TRX8551","eventTime":"2020-06-24T13:21:00.664+00:00","eventType":"PAYMENT"}},{"eventDetails":{"eventDescription":"SCT","eventId":"TRX8552","eventTime":"2020-06-24T13:21:01.664+00:00","eventType":"PAYMENT"}}}]}
in the same json I have many eventDetails section (here only two with few fields, but they are many more).
I tried to use:
indexed_extractions=JSON
and
LINE_BREAKER = \{\"eventDetails\"
but it still remains one.
How can I approach the problem?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
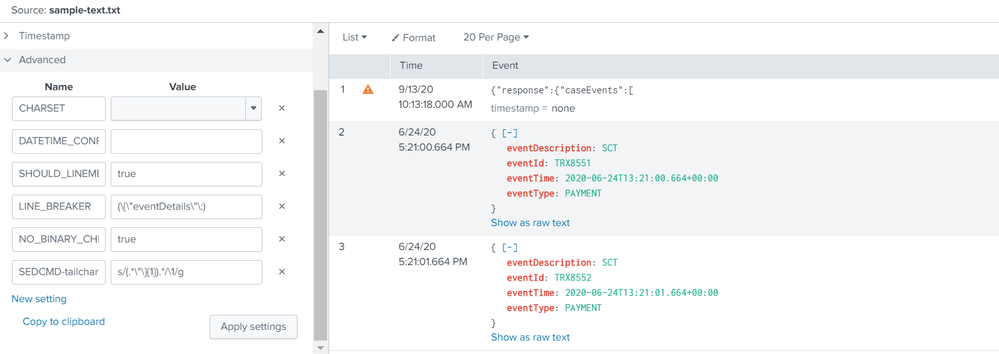
please have a look at below
[ __auto__learned__ ]
SHOULD_LINEMERGE=true
LINE_BREAKER=(\{\"eventDetails\"\:)
NO_BINARY_CHECK=true
SEDCMD-tailchars=s/(.*\"\}{1}).*/\1/g
Added SEDCMD class to remove unwanted characters at end of the line.
you need to deal with pre-text which is in first event.
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
please have a look at below
[ __auto__learned__ ]
SHOULD_LINEMERGE=true
LINE_BREAKER=(\{\"eventDetails\"\:)
NO_BINARY_CHECK=true
SEDCMD-tailchars=s/(.*\"\}{1}).*/\1/g
Added SEDCMD class to remove unwanted characters at end of the line.
you need to deal with pre-text which is in first event.
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, depending on the formatting of the json log files, you at least need the following in props.conf:
SHOULD_LINEMERGE = false
If the data is not prettyprinted, the following should help:
LINE_BREAKER= \}(,)\{
If the data is prettyprinted, the following may be used to allow for whitespaces between the comma and the curly brace:
LINE_BREAKER = \}(,\s*)\{
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
would there be any option to split them before indexing to Splunk? instead of depending on props.conf , is it possible to make changes in modular inputs if you are using one?
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @thambisetty,
I'd like to avoid to pre-elaborate the source with a script before indexing!
I'd like to find a way to split events in Splunk.
Have you another idea?
Ciao.
Giuseppe