Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: Why are there duplicate MV Fields with JSON da...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why are there duplicate MV fields with JSON data?
Hello there!
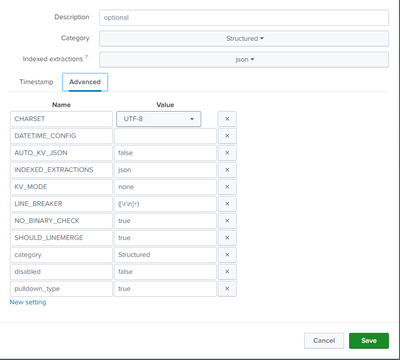
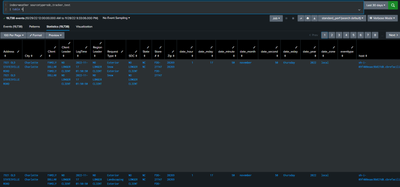
I'm trying to ingest JSON data via the Splunk Add-on for Microsoft Cloud Services app. I created a sourcetype with INDEXED_EXTRACTIONS=json and left all other settings to their default values. The data got ingested, however, when I table my events I start seeing mv fields with duplicate data. I'm even seeing the "Interesting Fields" section add up to 200% (instead of the expected 100%).

https://community.splunk.com/t5/All-Apps-and-Add-ons/JSON-format-Duplicate-value-in-field/m-p/306811
I then followed the advice given in this post ^^^ (i.e., setting KV_MODE=none, AUTO_KV_JSON=false, etc.) but the issue persists.
I have attached screenshots to this post to better understand my situation. I'm currently on Splunk Cloud.
Any help with this is greatly appreciated
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One common mistake is described in Structured Data Header Extraction and configuration.
* When 'INDEXED_EXTRACTIONS = JSON' for a particular source type, do not also set 'KV_MODE = json' for that source type. This causes the Splunk software to extract the JSON fields twice: once at index time, and again at search time. * Default: not set
