Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Getting Data In
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Updated : JSON event break for multiple source typ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Updated : JSON event break for multiple source type and single event in multiple lines.
AKG1_old1
Builder
05-21-2018
10:43 AM
Hi,
I am uploading json file having 2 different source type and single event is split multiple lines.
I am very close to solution but having issue with a small problem.
Problem: I am not be able to use these together in props.conf. only 1 is working at a time.
1.
SEDCMD-remove_bracket = s/\[|\]//g
SEDCMD-remove_coma = s/\},/}\n/g
2.
MUST_BREAK_AFTER = \}
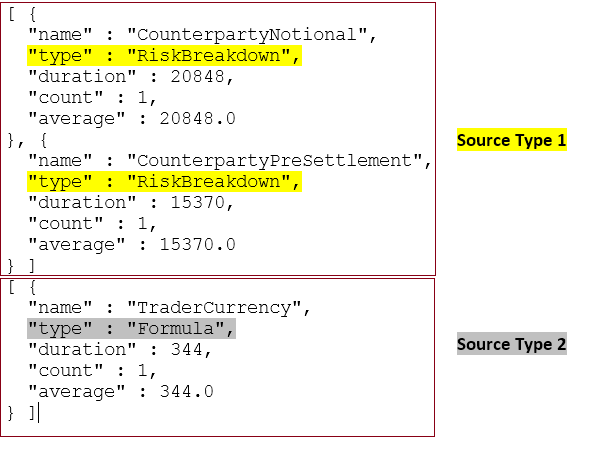
JSON logs after removing extra charaters(" [ , ] , }, ") to convert it in correct Json format
{
"name" : "CounterpartyNotional",
"type" : "RiskBreakdown",
"duration" : 20848,
"count" : 1,
"average" : 20848.0
}
{
"name" : "CounterpartyPreSettlement",
"type" : "RiskBreakdown",
"duration" : 15370,
"count" : 1,
"average" : 15370.0
}
{
"name" : "TraderCurrency",
"type" : "Formula",
"duration" : 344,
"count" : 1,
"average" : 344.0
}
transform.conf
[reset_profiler_formula]
DEST_KEY = MetaData:Sourcetype
REGEX = \"type\" : \"RiskBreakdown\"
FORMAT = sourcetype::reset_profiler:risks
[reset_profiler_risks]
DEST_KEY = MetaData:Sourcetype
REGEX = \"type\" : \"Formula\"
FORMAT = sourcetype::reset_profiler:formula
prop.conf
[reset_profiler]
SEDCMD-remove_bracket = s/\[|\]//g
SEDCMD-remove_coma = s/\},/}\n/g
KV_MODE = json
NO_BINARY_CHECK = true
MUST_BREAK_AFTER = \}
TRANSFORMS-sourcetye_routing = reset_profiler_formula,reset_profiler_risks
[reset_profiler:formula]
KV_MODE= json
[reset_profiler:risks]
KV_MODE= json
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
05-21-2018
11:25 AM
Give this a try
props.conf (on indexer/heavy forwarder whichever comes first)
[reset_profiler]
SHOULD_LINEMERGE = false
LINE_BREAKER = (\r\n]+)(?=\[\s*\{)
DATETIME_CONFIG = CURRENT
TRANSFORMS-sourcetye_routing = reset_profiler_st_override
transforms.conf (on indexer/heavy forwarder whichever comes first)
[reset_profiler_st_override]
DEST_KEY = MetaData:Sourcetype
REGEX =\"type\"\s*\:\s*\"([^\"]+)\"
FORMAT = sourcetype::reset_profiler:$1
props.conf (on search head)
[reset_profiler:formula]
KV_MODE= json
[reset_profiler:risks]
KV_MODE= json
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AKG1_old1
Builder
05-21-2018
02:46 PM
@somesoni : Thanks for reply but now all events in one file taken as single event.
Get Updates on the Splunk Community!
[Puzzles] Solve, Learn, Repeat: Dynamic formatting from XML events
This challenge was first posted on Slack #puzzles channelFor a previous puzzle, I needed a set of fixed-length ...
Enter the Agentic Era with Splunk AI Assistant for SPL 1.4
🚀 Your data just got a serious AI upgrade — are you ready?
Say hello to the Agentic Era with the ...
Stronger Security with Federated Search for S3, GCP SQL & Australian Threat ...
Splunk Lantern is a Splunk customer success center that provides advice from Splunk experts on valuable data ...