- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Problem with time in Edge Processor
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Problem with time in Edge Processor
Hello,
I am receiving darktrace events through my Edge Processor as a Forwarder and I am a bit new to the SPL2 pipeline. It can probably be solved by transforming something in the pipeline.
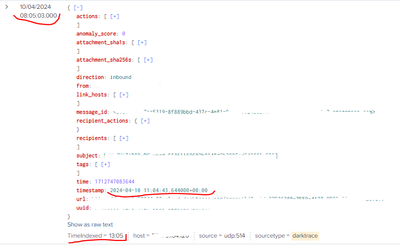
The problem is that I am indexing events with a _time of -5h and a 2h difference from the event time stamp. Here is an example:
Time in the Edge Processor:
It should be noted that the rest of the events that I ingest through this server are arriving at the correct time.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, but nothing relevant
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
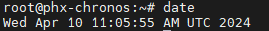
Look at the raw text rather than the JSON to see what Splunk may be using for timestamp detection. The JSON view is sorted and Splunk will only look a certain distance into the event to detect a timestamp (128 bytes by default).
If it cannot find a timestamp, then it will use current time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
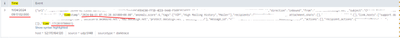
Here the raw:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That looks like it is more than 128 characters into the event, so you should set up MAX_TIMESTAMP_LOOKAHEAD and optionally TIME_PREFIX for your sourcetype for that data.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can I do this? Note that the forwarder is an Edge Processor and you can't touch the conf files, everything is modified in the GUI.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, I'm unsure where the time will get extracted, but have you looked at this document
https://docs.splunk.com/Documentation/SplunkCloud/9.1.2312/EdgeProcessor/TimeExtractionPipeline
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes...