Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- How to parse the format of Windows Event Log, in o...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to parse the format of Windows Event Log, in order to forward these logs to syslog server?
Hi ,
For some reason , I must forward the Windows Event Log to our syslog server.
I configured the indexer server as document described, and it works successfully :
http://docs.splunk.com/Documentation/Splunk/6.5.1/Forwarding/Forwarddatatothird-partysystemsd
( The "Forward syslog data to a third-party host" part )
But I don't know how to parse the Windows Event Log that Splunk forwarded to me.
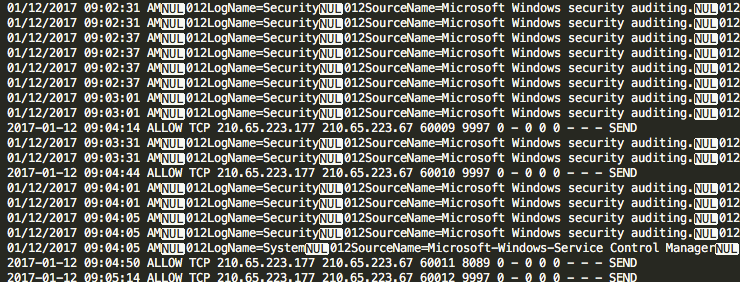
The attached screenshot is the example log I opened with "Sublime" ( Text Editor ).
It looks like Splunk converted the multi-line logs to single lines, and uses some special characters to format the log.
Anyone familiar with this format? How to parse it?
OR what does the character "NUL" exactly mean? and I notice there is a number ( usually 012 , 015 ) follow by this character , I guess they have special meanings ( like \t , \n ... or some control characters.)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
theres an option to sendCookedData in outputs.conf. You want to set that to false.