Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- How to create a field of stats to string for searc...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to create a field of stats to string for search in eval?
Hi splunkers
Why when I do the following query if it gives me the correct data
Query
| inputlookup append=t mitre_lookup
| foreach TA00*
[
| lookup mitre_tt_lookup technique_id as <<FIELD>> OUTPUT technique_name as <<FIELD>>_technique_name
| eval <<FIELD>>_technique_name=mvindex(<<FIELD>>_technique_name, 0)
]
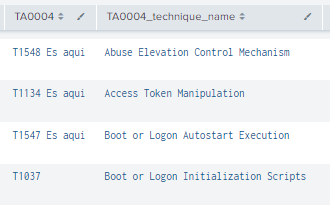
| eval codes_tech = "T1548, T1134,T1547"
| makemv delim=", " codes_tech
| eval TA0004 = if(mvfind(codes_tech, TA0004) > -1, TA0004." Es aqui", TA0004)
Result:
But when the data comes from a stats result it doesn't search for the values:
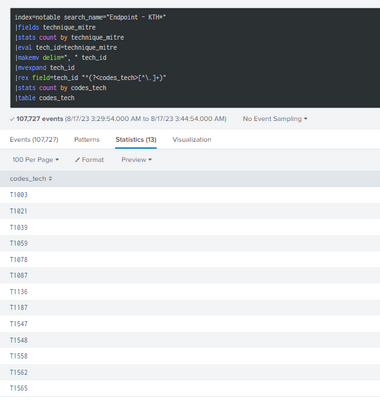
Query:
index=notable search_name="Endpoint - KTH*"
|fields technique_mitre
|stats count by technique_mitre
|eval tech_id=technique_mitre
|rex field=tech_id "^(?<codes_tech>[^\.]+)"
|stats count by codes_tech
|makemv delim=", " codes_tech
|mvexpand codes_tech
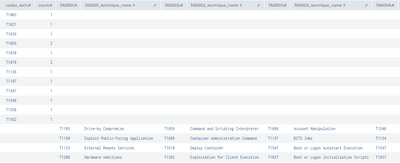
|stats count by codes_tech
| inputlookup append=t mitre_lookup
| foreach TA00*
[
| lookup mitre_tt_lookup technique_id as <<FIELD>> OUTPUT technique_name as <<FIELD>>_technique_name
| eval <<FIELD>>_technique_name=mvindex(<<FIELD>>_technique_name, 0)
]
| eval codes_tech = codes_tech
| eval TA0004 = if(mvfind(codes_tech, TA0004) > -1, TA0004." Es aqui", TA0004)
Result:
I would really appreciate your support
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
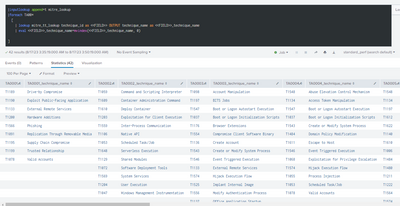
What is it you are trying to do?
Does this help?
|fields technique_mitre
|stats count by technique_mitre
|eval tech_id=technique_mitre
|rex field=tech_id "^(?<codes_tech>[^\.]+)"
|stats count by codes_tech
|makemv delim=", " codes_tech
|mvexpand codes_tech
|stats count by codes_tech
| lookup mitre_tt_lookup technique_id as codes_tech- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi.
What I am trying to do is the following...
I need what I bring in codes_tech to look for it in columns A,B,C, etc and if it finds something that says "Es aqui"
My query is:
index=notable search_name="Endpoint - KTH*"
|fields technique_mitre
|stats count by technique_mitre
|eval tech_id=technique_mitre
|rex field=tech_id "^(?<codes_tech>[^\.]+)"
|stats count by codes_tech
|makemv delim=", " codes_tech
|mvexpand codes_tech
|fields codes_tech
| inputlookup append=t mitre_lookup
| foreach TA00*
[
| lookup mitre_tt_lookup technique_id as <<FIELD>> OUTPUT technique_name as <<FIELD>>_technique_name
| eval <<FIELD>>_technique_name=mvindex(<<FIELD>>_technique_name, 0)
| eval <<FIELD>>=<<FIELD>>_technique_name . " " . <<FIELD>>
|eval <<FIELD>>=split(replace(<<FIELD>>,"\.",".|"),"|")
]
| eval TA0004 = if(mvfind(codes_tech, TA0004) > -1, TA0001." Es aqui", TA0004)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, what do you get when you try my suggestion?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
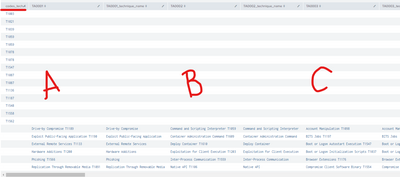
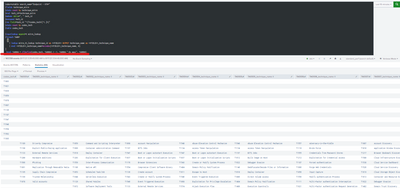
With your suggestion I get the following result:
Can I explain my query in parts? Maybe that's how I understand it better
I have two queries if I execute them separately it gives me the following result
Query 1:
index=notable search_name="Endpoint - KTH*"
|fields technique_mitre
|stats count by technique_mitre
|eval tech_id=technique_mitre
|makemv delim=", " tech_id
|mvexpand tech_id
|rex field=tech_id "^(?<codes_tech>[^\.]+)"
|stats count by codes_tech
|table codes_tech
Query 2:
|inputlookup append=t mitre_lookup
|foreach TA00*
[
| lookup mitre_tt_lookup technique_id as <<FIELD>> OUTPUT technique_name as <<FIELD>>_technique_name
| eval <<FIELD>>_technique_name=mvindex(<<FIELD>>_technique_name, 0)
]
What I did was join the two queries and look for each value that codes_tech brings in the columns TA0001, TA0002, TA0003, etc. For that I thought of using an eval, but it doesn't do anything 😞
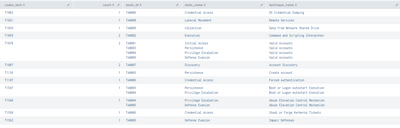
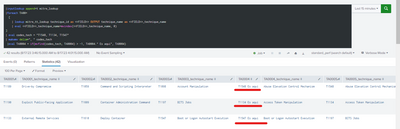
However, something curious happens or I don't know why the following happens...
If I put the values directly in an eval and then separate it by commas if it looks for the values in the lookup, let me show you...
I really don't know how to approach the issue 😞
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am still not entirely sure what your expected output should look like
Please can you provide a mock up of what you are trying to achieve.
In the meantime, does this give you what you need?
|fields technique_mitre
|stats count by technique_mitre
|eval tech_id=technique_mitre
|rex field=tech_id "^(?<codes_tech>[^\.]+)"
|stats count by codes_tech
|makemv delim=", " codes_tech
|mvexpand codes_tech
|stats count by codes_tech
| lookup mitre_tt_lookup technique_id as codes_tech
| foreach tactic_id tactic_name technique_name
[| eval <<FIELD>>=mvindex(<<FIELD>>,part)]
| eval {tactic_id}_tactic_name=tactic_name
| eval {tactic_id}_technique_name=technique_name
| fields - tactic_id tactic_name technique_name
| stats values(*) as * by codes_tech- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I need to do a dashboard in dashboard studio. I already configured some rules and if it triggers any I need to paint it on the dashboard, like this...