Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: How to configure Splunk to break my sample log...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I have the below log data:
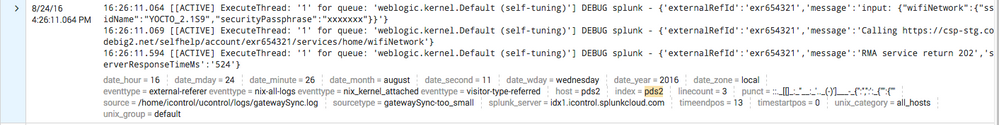
16:37:56.875 [[ACTIVE] ExecuteThread: '4' for queue: 'weblogic.kernel.Default (self-tuning)'] DEBUG splunk - {'externalRefId':'exr654321','message':'input: {"wifiNetwork":{"ssidName":"YOCTO_2.1S9","securityPassphrase":"xxxxxxx"}}'}
16:37:56.883 [[ACTIVE] ExecuteThread: '4' for queue: 'weblogic.kernel.Default (self-tuning)'] DEBUG splunk - {'externalRefId':'exr654321','message':'Calling https://csp-stg.codebig2.net/selfhelp/account/exr654321/services/home/wifiNetwork'}
16:37:57.296 [[ACTIVE] ExecuteThread: '4' for queue: 'weblogic.kernel.Default (self-tuning)'] DEBUG splunk - {'externalRefId':'exr654321','message':'RMA service return 202','serverResponseTimeMs':'413'}
and whenever it is imported into Splunk using the Universal Forwarder, it treats it as one event (see image)
How can I get Splunk to separate each line?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try adding this to your props.conf on the indexer and restart splunk
[sourcetype_stanza_name]
SHOULD_LINEMERGE=true
TIME_FORMAT=%H:%M:%S.%3N
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like you are relying on Splunk to detect your events, given the sourcetype name of gatewaySync-too_small. I recommend you are explicit in defining your sourcetype on the receiving indexer(s) by creating a props.conf file and specifying the settings you want to apply.
Try this:
[yoursourcetypename]
BREAK_ONLY_BEFORE=^\d+:\d+:d+\.\d+
SHOULD_LINEMERGE=false
TIME_FORMAT=%H:%M:%S.%3N
Then set sourcetype=yoursourcetypename in inputs.conf on your forwarder.
This presentation may be helpful, if you are new to Splunk; relevant stuff starting on slide 23.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try adding this to your props.conf on the indexer and restart splunk
[sourcetype_stanza_name]
SHOULD_LINEMERGE=true
TIME_FORMAT=%H:%M:%S.%3N
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
All great answers but I have splunk cloud and therefore no access to props.conf.
I did try this but..... now I get no events 😞
[root@pds2 bin]# ./splunk add monitor /home/icontrol/ucontrol/logs/gatewaySync.log -index pds2 -sourcetype _json
Any way to do this just by using inputs.conf???
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This answers post should give you a pretty good overview of how to work with SplunkCloud for both search-time as well as index-time settings.