Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Getting Data In
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Field extraction from simple one-sentense log
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Field extraction from simple one-sentense log
user2020dy
Path Finder
10-08-2020
03:21 AM
Can anybody help me to create props.conf and transforms.conf files to correctly parse such logs?
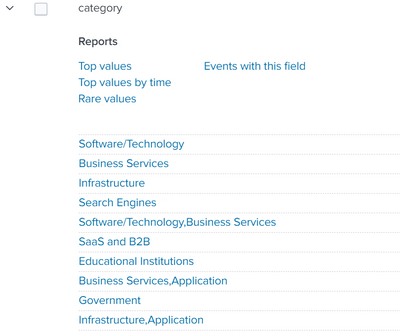
"2020-10-08 09:35:56","Department1","Department2","113.8.10.134","113.8.10.132","Allowed","1 (A)","NOERROR","ant.com.","Search Engines","Networks","Networks","""2020-10-08 09:35:56","Department1","Department2","113.8.10.134","113.8.10.132","Allowed","1 (A)","NOERROR","ant.com.","Search Engines,Malware","Networks","Networks","""2020-10-08 09:35:56","Department1","Department2","113.8.10.134","113.8.10.132","Allowed","1 (A)","NOERROR","ant.com.","Search Engines,Malware, Network","Networks","Networks","""2020-10-08 09:35:56","Department1","Department2","113.8.10.134","113.8.10.132","Allowed","1 (A)","NOERROR","ant.com.","Malware","Networks","Networks",""
As you see, here the log with the category field "Search Engines,Malware" should belong to both categories: Search Engines and Malware. So, the category field can consist of 1, 2, 3 or more values.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
493669
Super Champion
10-08-2020
03:31 AM
@user2020dy try like below-
props.conf -
[sourcetype_name]
LINE_BREAKER = ([\r\n]+)
SHOULD_LINEMERGE = false
category = Custom
TIME_PREFIX = ^\"
MAX_TIMESTAMP_LOOKAHEAD = 30
TIME_FORMAT = %Y-%m-%d %H:%M:%S
REPORT-main = parse transforms.conf -
[parse]
DELIMS = ","
FIELDS = Time,field1,field2,field3,field4,field5,field6,field7,field8,field9,field10,field11,field12,field13
Let me know if it helps! and upvote will be appreciated
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
user2020dy
Path Finder
10-08-2020
05:20 AM
thank you, it helps to parse most logs, but the field category can contain 2 or 3 values
Can you prompt how to delimeter these values?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
493669
Super Champion
10-08-2020
07:21 AM
you can use rex command to separate values within category.
Get Updates on the Splunk Community!
Data Management Digest – December 2025
Welcome to the December edition of Data Management Digest!
As we continue our journey of data innovation, the ...
Index This | What is broken 80% of the time by February?
December 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Unlock Faster Time-to-Value on Edge and Ingest Processor with New SPL2 Pipeline ...
Hello Splunk Community,
We're thrilled to share an exciting update that will help you manage your data more ...