- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Event Detail ++ _time field "+" icon
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there.
Did you saw in many events, exploding the event to detail, the _time field has a "+" icon on its side?
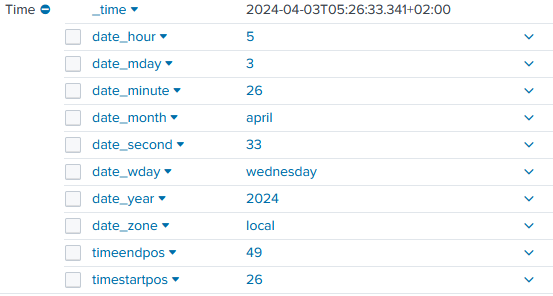
Exploding it, give the detail of created _time field,
What's that?
In other events i can't see the "+" icon, also on same server/path/log,
Is it some kind of,
"+" == I, SPLUNK INDEXER, ELABORATED THE TIMESTAMP WITH MY ALGORITHMS BY MYSELF IN THIS WAY
clean, no "+" == automatic timestamp calculation, no elaboration, i found it yet cooked
?
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @verbal_666,
You can see related documentation below about timestamp information. The events that missing date_* fields may not have extracted time inside.
https://docs.splunk.com/Documentation/Splunk/latest/Knowledge/Usedefaultfields#Use_default_fields
Only events that have timestamp information in them as generated by their respective systems will have date_* fields. If an event has a date_* field, it represents the value of time/date directly from the event itself. If you have specified any timezone conversions or changed the value of the time/date at indexing or input time (for example, by setting the timestamp to be the time at index or input time), these fields will not represent that.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @verbal_666,
You can see related documentation below about timestamp information. The events that missing date_* fields may not have extracted time inside.
https://docs.splunk.com/Documentation/Splunk/latest/Knowledge/Usedefaultfields#Use_default_fields
Only events that have timestamp information in them as generated by their respective systems will have date_* fields. If an event has a date_* field, it represents the value of time/date directly from the event itself. If you have specified any timezone conversions or changed the value of the time/date at indexing or input time (for example, by setting the timestamp to be the time at index or input time), these fields will not represent that.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Clear.
So, an event with _time field with "+", in practice, represents a complete _time extraction with all "date_*" underfields inside 👍
Thanks 👏👏