Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Getting Data In
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Duplicated Events: Local Log4net_xml Monitor
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Duplicated Events: Local Log4net_xml Monitor
JacobCarrell
Explorer
07-28-2020
07:21 AM
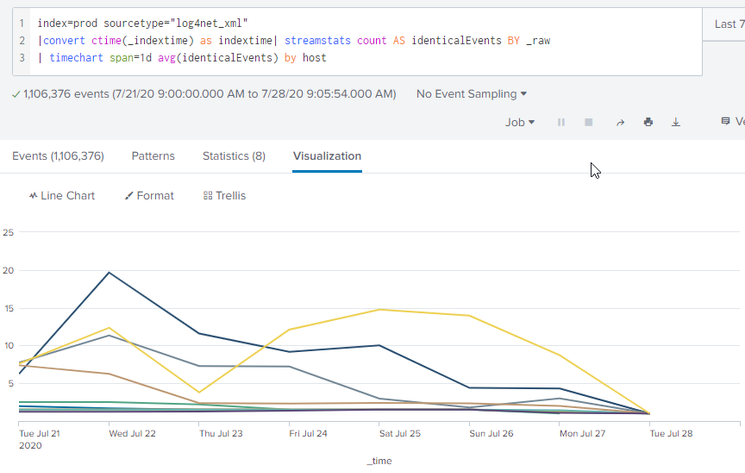
I've got an issue where a significant portion of my ingested Log4Net_xml sourcetype logs have duplicate events. I'm currently using a file monitor on a Ubuntu 16.04 LTS, Splunk 7.3.0 machine with a local Monitor stanza to ingest the logs which looks like this:
[monitor:///mnt/CALogs/.../*.log]
disabled = 0
host_segment = 4
index = ca
sourcetype = log4net_xml
#initCrcLength = 1024 # Tried this, it started reindexing all the log file.Our Log4Net configs looks like this:
<appender name="RollingFile" type="log4net.Appender.RollingFileAppender">
<file type="log4net.Util.PatternString" value="\\server1\ca\Logs\Application\%property{log4net:HostName}\Application.log" />
<appendToFile value="true" />
<rollingStyle value="Size" />
<maximumFileSize value="5MB" />
<staticLogFileName value="true" />
<maxSizeRollBackups value="10" />
<layout type="log4net.Layout.XMLLayout" />
</appender>I have that directory mounted over SMB/CIFS with the following entry in fstab:
//server1/LogsCA /mnt/CALogs cifs username=user,password=Password,domain=somedomain.dev,sec=ntlm 0 0
Can anybody spot what I'm doing wrong?
Here's a picture of the search that I'm using to estimate duplicates:
Get Updates on the Splunk Community!
Application management with Targeted Application Install for Victoria Experience
Experience a new era of flexibility in managing your Splunk Cloud Platform apps! With Targeted Application ...
Index This | What goes up and never comes down?
January 2026 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Splunkers, Pack Your Bags: Why Cisco Live EMEA is Your Next Big Destination
The Power of Two: Splunk + Cisco at "Ludicrous Scale"
You know Splunk. You know Cisco. But have you seen ...