- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Collect Windows DNS and PowerShell logs with Splun...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Splunkers, for a customer we are preforming a migration in Windows Logs collection: as suggested by some of you in another topic, we are passing from WMI method to UF one (and it is very, very, very - Have I already told "very"? - better). We encountered a difference with WMI we don't know how to solve, and here I am to ask your help.
First, a little recap of architecture: UF are installed on DC and then data are sent to an HF, which following forward data to a Splunk Cloud instance. So the flow is:
DCs with UF installed -> HF -> Splunk Cloud.
When we configured WMI, we selected the "classic" logs (Security, Application, System) plus DNS and PowerShell. In particular, our SOC is interested in DNS query logs.
When we installed the UF (with graphic wizard), we found only the "classic" options: Security, Application and System.
If we want to collect also DNS query logs and PowerShell one, how can we achieve this using UF? I suspect we need to modify the inputs.conf file, but is my assumption correct? And if yes, how can I go on?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @SplunkExplorer,
Haha I am not a Windows expert either ! But yes the main question is : are we sure that the DNS logs go to a Windows Event channel (from what I read it should be the case) + what is the name of this Win Event channel (if you put a wrong name in the stanza of the inputs.conf file, no data will be forwarded).
If you can RDP to the DNS server, you can open the Windows Event Viewer and search that channel and retrieve its exact name.
But you got the point, once you have the channel name, just add a new stanza block in the inputs.conf file, just like you did for Powershell logs !
Good luck,
GaetanVP
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @SplunkExplorer,
Indeed you're right, you can add some lines in the inputs.conf file to tell your Splunk UF to "Monitor more stuff".
More precisely, during the UF installation, Splunk should have created an application with an inputs.conf file that you can open and modified at this path :
C:\Program Files\SplunkUniversalForwarder\etc\apps\SplunkUniversalForwarder\local
If you want to keep all your monitored files/channels in the same place, you can add the new configuration at the bottom of this file (otherwise you could have created a new app and create a new input.conf file)...
Nevermind, in order to monitor the powershell logs, you can simply add a new stanza with the following :
It will be very similar to the stanza that Splunk created during installation time, since all those type of logs can be retrieved from windows event channels (powershell is just another one, like system, application or security...)
[WinEventLog://Windows PowerShell]
checkpointInterval = 5
current_only = 1
disabled = 0
renderXml = 1
evt_resolve_ad_obj = 1If you want detail of what is the purpose of each key, feel free to check the official inputs.conf doc : https://docs.splunk.com/Documentation/Splunk/9.0.5/Admin/Inputsconf
Do not forget to restart your Splunk UF (restart the service or use the "splunk restart" command) !
For DNS logs, I do not know if the logs are registered in a Win Event Channel... Or do you save the logs in a specific location ? This location could be monitored with the same inputs.conf file.
Hope it helps !
GaetanVP
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
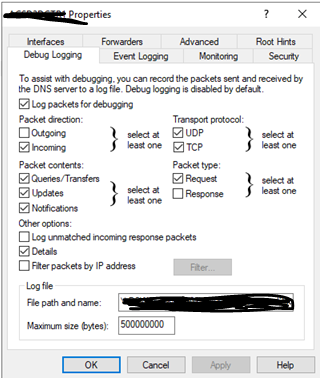
Hi @GaetanVP , I collected the answer by customer and we got this: no particular configuration has been performed, except configure debugging and related archives in a network share:
I'm not a great expert on Windows, but this should be only a copy for debugging purpose, so the normal flow should be a classic Win Event Channel, right? In such a case, a stanza with header:
[WinEventLog://Windows DNS Server]
and proper parameter should de fine, right?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @SplunkExplorer,
Haha I am not a Windows expert either ! But yes the main question is : are we sure that the DNS logs go to a Windows Event channel (from what I read it should be the case) + what is the name of this Win Event channel (if you put a wrong name in the stanza of the inputs.conf file, no data will be forwarded).
If you can RDP to the DNS server, you can open the Windows Event Viewer and search that channel and retrieve its exact name.
But you got the point, once you have the channel name, just add a new stanza block in the inputs.conf file, just like you did for Powershell logs !
Good luck,
GaetanVP
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @GaetanVP, thanks a lot for your fast and kind answer.
Now it totally clear how to add PowerShell logs to collected ones!
Regarding your question on DNS, I don't know the answer; I mean, if your question is related to a config Microsoft side, I have no access to this data, cause customer hosts are on its Data Center and we do not manage the Domain Controller configuration. I have to check with our reference before give you an answer.