- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Can you answer my fundamental question about the d...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you answer my fundamental question about the date time picker?
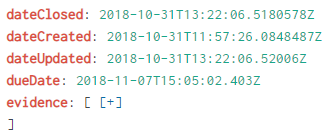
I have a fundamental question regarding dealing with multiple dates per log message. Below is a typical log that I've ingested (as part of a historical data load) and I'm allowing Splunk to assign _time to the time that this record is ingested.
The reason I allowed it to index _time it was ingested is because each of these times are equally valid for querying against. This obviously leads to issues with utilizing the date/time picker as it only looks at the _time field.
I have to believe others have dealt with this, so I'm wondering what the best practice is? Do people create separate indexes for this? I think I saw some individuals using different source types, which, in this case, I don't think would make sense. I've seen some references to creating transactions for dealing with this scenario too. Really appreciate any advice on how to appropriately handle this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I might have answered my own question as the following seems to work.
index="myindex"
| addinfo
| eval createdEpoch = strptime(dateCreated, "%Y-%m-%dT%T")
| where createdEpoch >= info_min_time