Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- AWS Grand Central Add-on with nested AWS OUs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AWS Grand Central Add-on with nested AWS OUs
We installed the Grand Central 3.0.7 add-on installed in our Splunk Cloud environment and were working on configuring it for our AWS Master Account…We got through the first several steps and since we were seeing it pull in the AWS accounts, we were pretty happy that things were working….then we got to the AWS Stacksets…and it looks like AWS Organizational Units only show up if those OUs are off the root OU and also that OU contains an AWS account. In our environment, we have OUs that are nested within other OUs and our AWS accounts reside in the child OUs. Here is what we found:
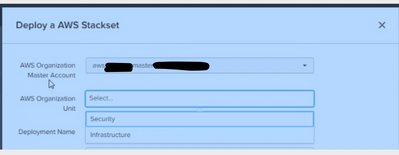
Notice in this Grand Central dialog, only the ‘Security’ and ‘Infrastructure’ OUs show up in the drop-down:
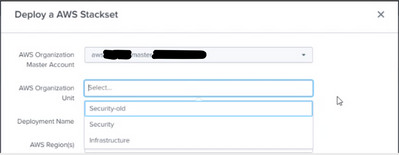
See in this AWS OU screenshot, most of the OUs in AWS did not show up in the Grand Central AWS OU drop-down. The ‘Business Units’ OU is one that contains child OUs whose child AWS accounts we would want to be managed/collected via Grand Central. Notice the OU named ‘Security-old’…it only has a “grandchild” AWS account (a child of the ‘GC-Testing01’ OU) and no AWS account is directly contained within the ‘security-old’ OU.
To test, we moved the ‘security_acct’ AWS account from the ‘Security-old / GC-Testing01’ OU to the ‘Security-old’ OU….and then after refreshing things in Grand Central, it shows up in the drop down.
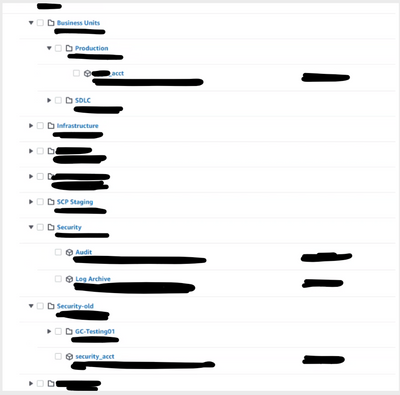
Here is the OU structure that we found will work in Grand Central (Notice that the ‘security-acct’ AWS account is now in the ‘security-old’ OU (right off the root):
Notice above, the ‘security_acct’ AWS account is now contained directly within the ‘Security-old’ OU.
I need to find a way to get Grand Central to work with the way we have structured our OUs and AWS accounts. I am told we have structured our OUs generally following the recommended best practices from AWS: https://aws.amazon.com/blogs/mt/best-practices-for-organizational-units-with-aws-organizations/
I’m looking for any guidance on next steps forward for us to be able to push stacksets to all our AWS accounts as they lay in their nested OUs. Any thoughts or ideas?
Thank you,
REID