Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Deployment Architecture
- :
- Re: Trigger script execution upon bucket change fr...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Trigger script execution upon bucket change from hot to warm
Is it possible to make splunk send notification (or trigger script execution directly) when it moved backet between different states? Specifically from hot to warm.
There is coldToFrozenScript option in indexes.conf (coldToFrozenScript = $SPLUNK_HOME/bin/cold_to_frozen.sh), I'm looking for something like hotToWarmScript.
This is required for backup purpose.
Thank you,
Roman Naumeneko
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
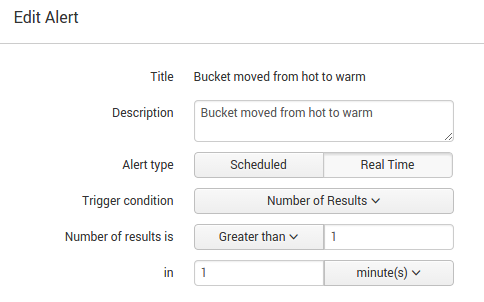
I'm configuring this whole thing simply for sending buckets to S3 as soon as they are eligible (which is warm status).
I'm still confused with search and alert settings. Number of results > 1 should be for which period of time?
And another option, is it "once" or "for each result"? And if "for each result", what should be field value for throttling results, which splunk requires to be set in this case.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now I'm confused about "real time" search.
In the alert config "Alert Type: Real-time"
In the search, if Presets = "All time (real-time)", then query returns nothing. Hmm, how come if there are events during the day and they shown with for example "1 hour window" preset?
I understand that "1 hour window" will return results in realtime + 1 hour back. But what should be set in this case for the search request used in trigger?!
I configured search as "1 hour window" realtime, but I am not sure if it affect trigger anyhow. Does it?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No! There is no hotToWarmScript - and you shouldn't make one! You should not be fiddling with the buckets, until the bucket is moved to frozen. Once the bucket is frozen, it is out of the index and so you can do what you want.
For hot, warm and cold buckets - don't move them, don't edit them, etc. You can make a backup copy, which is what I assume you will do with this alert.
As for the alert, your trigger should be number of results > 1, and you probably want to run the script for each event, not just once per search/trigger. And there is really no reason to run this as a real-time alert. Running it once an hour as a scheduled alert should be more than adequate, unless Splunk is ingesting a lot more than 20GB per hour of data.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cool, it's quite easy to get what's being moved.
The request is
host = splnk-indx index=_internal sourcetype=splunkd "finished moving hot to warm"
I guess this would be the best way to implement same type of functionality as option coldToFrozenScript provides in indexes.conf?
http://docs.splunk.com/Documentation/Splunk/6.2.0/Alert/Configuringscriptedalerts
Or maybe there is undocumented option hotToWarmScript, no? 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Start with this search:
index=_internal sourcetype=splunkd component=BucketMover
There will be a lot of events, so you will need to add additional constraints to this search. When it works the way you want, save it as an alert that runs once a day (or once an hour, or whatever you want). Have the alert execute the script.
More info here: Configure a script for an alert