Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Deployment Architecture
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Deployment Architecture
- :
- Search Affinity Disabled on multisite cluster : Se...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Search Affinity Disabled on multisite cluster : Search results are incomplete
amey2407

Splunk Employee
08-24-2021
11:42 PM
Hi,
We have a multisite cluster with 1 indexer on each site with 1 SH on primary site. Currently, when search affinity is enabled and we run a search for index "crowdstrike" , we can see past 30 days data. But when search affinity is disabled on the search head, the same search displays recent data and not the past 30 days.
Question: Is there something missing configuration wise?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
manikumarv
Explorer
10-12-2021
08:09 AM
Were you able to get this resolved? We are experiencing the same when search affinity is disabled.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
amey2407

Splunk Employee
10-12-2021
05:53 PM
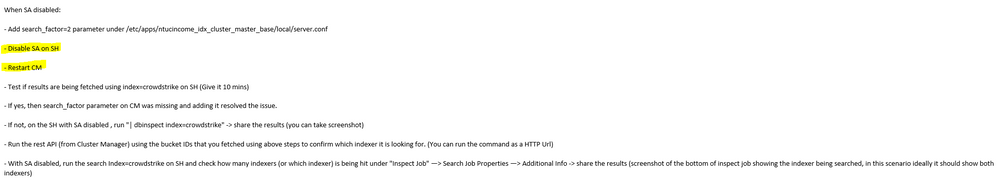
@manikumarv Following were the steps followed by customer to resolve the issue. Hope this helps.
Apparently, the key steps are the ones highlighted below.
At the start of the MW, I've tried to add the search_factor=2 and restarted the CM for it to take effect, then to disable SA and restarted the SH.
Waited 10 mins or so but still the outcome was the same as before.
But I tried restarting the CM again, to ensure that all steps were followed to the key.
Almost immediately, the old events appeared.
Before
After
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
manikumarv
Explorer
10-13-2021
12:56 PM
@amey2407 Thanks for the details.
We do have the [single-site] SF setting already on the CM as you noted. But I did not try restarting CM after disabling SA on the SH. I'll give that a try and let you know.
Get Updates on the Splunk Community!
Index This | Why did the turkey cross the road?
November 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Enter the Agentic Era with Splunk AI Assistant for SPL 1.4
🚀 Your data just got a serious AI upgrade — are you ready?
Say hello to the Agentic Era with the ...
Feel the Splunk Love: Real Stories from Real Customers
Hello Splunk Community,
What’s the best part of hearing how our customers use Splunk? Easy: the positive ...