Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Deployment Architecture
- :
- Fileds missing when searching index=_audit on SH
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fileds missing when searching index=_audit on SH
Hello splunkers,
I'm trying to find users command history on my SH but when I'm running the following command I have zero results:
index=_audit action=search info=granted search=* NOT "search_id='scheduler" NOT "search='|history" NOT "user=splunk-system-user" NOT "search='typeahead" NOT "search='| metadata type=* | search totalCount>0" | stats count by user search _time | sort _time | convert ctime(_time) | stats list(_time) as time list(search) as search by user
I realized that a lot of fields missing.
When I run index=_audit I have only host, index,source and sourcetype fileds, all the other(search, user, etc) are missing.
Do you have any idea why I have this strange phenomenon?
I did the test to another SH and the command works perfect and I have all the fields.
Is there any conf file that could be deleted (or modified) accidentally by an other admin?
Thank you in advance.
Michael
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mvagionakis,
Have you pointed all your search heads to indexers in outputs.conf?
Please check below link which might help you.
http://docs.splunk.com/Documentation/Splunk/latest/DistSearch/Forwardsearchheaddata
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
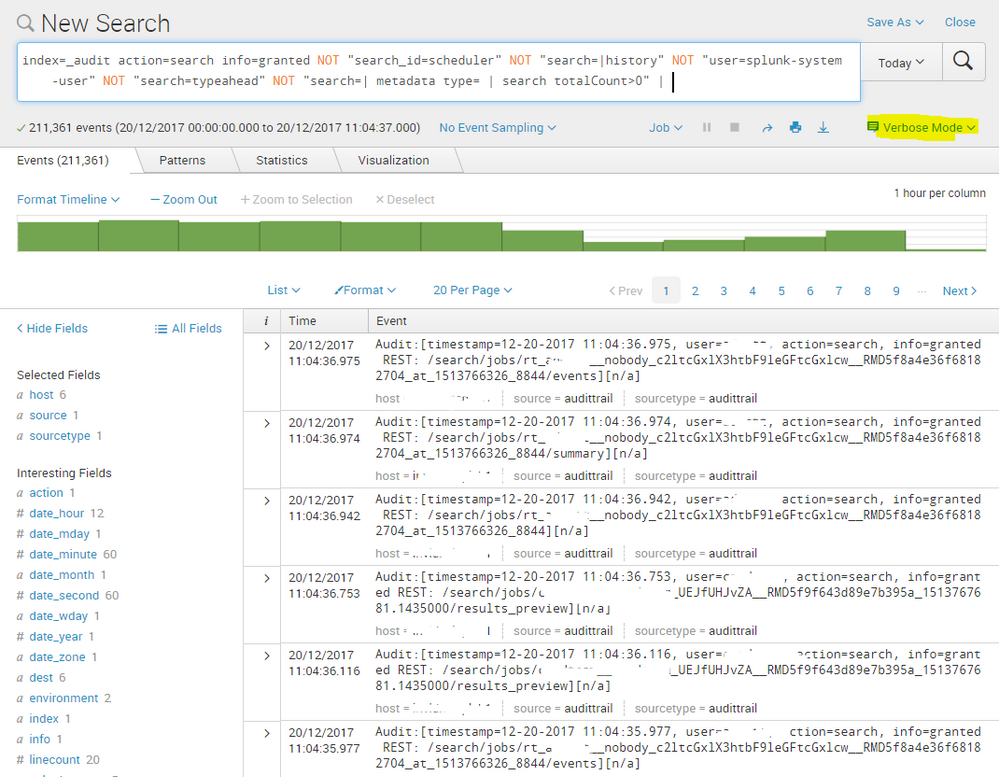
It sounds like you may be searching in fast-mode. try enabling verbose mode and see if the results are different.
Fast mode
Verbose Mode
I also corrected your search which had an error - try this:
index=_audit action=search info=granted NOT "search_id=scheduler" NOT "search=|history" NOT "user=splunk-system-user" NOT "search=typeahead" NOT "search=| metadata type= | search totalCount>0" | stats count by user search _time | sort _time | convert ctime(_time) | stats list(_time) as time list(search) as search by user
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, nickhillscpl ,
I'm already in verbose mode.
Also, as I said , even if I run index=_audit, I have no field detected except those four that I said.
thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Can you please post your query in Code Sample format (101010) ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi,
it's done
thank you