- Splunk Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Why won't data passing from global search to child...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
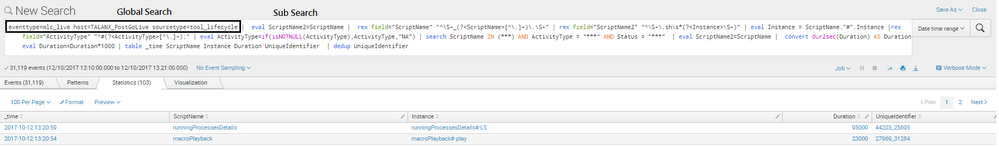
In my dashboard, I am using one global search and multiple sub search queries(which use global search query data).
Issue is data is not getting displayed on dashboard, but when i click on search button its append sub search to global search and displaying results. Now sure why its not getting displayed on dashboard.
Global Search
<search id="globalSearch">
<query>eventtype=mlc_live host=$host_token$ sourcetype=tool_lifecycle </query>
<earliest>$time_token.earliest$</earliest>
<latest>$time_token.latest$</latest>
</search>
Sub Search
<search base="globalSearch">
<query> | eval ScriptName2=ScriptName | rex field="ScriptName" "^\S+_(?<ScriptName>[^\.]+)\.\S+" | rex field="ScriptName2" "^\S+\.sh\s*(?<Instance>\S+)" | rex field="ActivityType" "^#(?<ActivityType>[^\.]+);" | eval ActivityType=if(isNOTNULL(ActivityType),ActivityType,"NA") | search ScriptName IN (*$script_name_token$*) AND ActivityType = "*$activity_type_token$*" AND Status = "*$status_token$*" | table _time ScriptName Instance StartDate StartTime EndDate EndTime Duration UniqueIdentifier Status ActivityType | sort 0 _time desc | dedup UniqueIdentifier</query>
<earliest>$time_token.earliest$</earliest>
<latest>$time_token.latest$</latest>
</search>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI,
I'm just putting extraction into base search. Can you please try if It is not affecting your business logic ??
<search id="globalSearch">
<query>eventtype=mlc_live host=$host_token$ sourcetype=tool_lifecycle | eval ScriptName2=ScriptName | rex field="ScriptName" "^\S+_(?<ScriptName>[^\.]+)\.\S+" | rex field="ScriptName2" "^\S+\.sh\s*(?<Instance>\S+)" | rex field="ActivityType" "^#(?<ActivityType>[^\.]+);" | table _time ScriptName Instance StartDate StartTime EndDate EndTime Duration UniqueIdentifier Status ActivityType </query>
<earliest>$time_token.earliest$</earliest>
<latest>$time_token.latest$</latest>
</search>
<search base="globalSearch">
<query>eval ActivityType=if(isNOTNULL(ActivityType),ActivityType,"NA") | search ScriptName IN (*$script_name_token$*) AND ActivityType = "*$activity_type_token$*" AND Status = "*$status_token$*" | table _time ScriptName Instance StartDate StartTime EndDate EndTime Duration UniqueIdentifier Status ActivityType | sort 0 _time desc | dedup UniqueIdentifier</query>
</search>
Please correct my syntax if any typo.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI,
I'm just putting extraction into base search. Can you please try if It is not affecting your business logic ??
<search id="globalSearch">
<query>eventtype=mlc_live host=$host_token$ sourcetype=tool_lifecycle | eval ScriptName2=ScriptName | rex field="ScriptName" "^\S+_(?<ScriptName>[^\.]+)\.\S+" | rex field="ScriptName2" "^\S+\.sh\s*(?<Instance>\S+)" | rex field="ActivityType" "^#(?<ActivityType>[^\.]+);" | table _time ScriptName Instance StartDate StartTime EndDate EndTime Duration UniqueIdentifier Status ActivityType </query>
<earliest>$time_token.earliest$</earliest>
<latest>$time_token.latest$</latest>
</search>
<search base="globalSearch">
<query>eval ActivityType=if(isNOTNULL(ActivityType),ActivityType,"NA") | search ScriptName IN (*$script_name_token$*) AND ActivityType = "*$activity_type_token$*" AND Status = "*$status_token$*" | table _time ScriptName Instance StartDate StartTime EndDate EndTime Duration UniqueIdentifier Status ActivityType | sort 0 _time desc | dedup UniqueIdentifier</query>
</search>
Please correct my syntax if any typo.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great !! Thanks. Can you pls mark it as Answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
shifted to Answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are not following many of the best practices for base/global searches and post-processing.
- Passing raw events to a post-processing search, i.e., not transforming the data in the base search
- Didn't indicate the base search what fields are needed in post-processing
- Not limiting the search results in any way
See here: http://docs.splunk.com/Documentation/Splunk/7.0.0/Viz/Savedsearches#Post-process_searches_2
You need to rethink your use case and strip down the base searches to use more suitable usage.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for clearing concept about base/global search. It helped 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI
There is no need to put earliest & latest in sub search. Can you please then?
Does your sub search panel shows No rec Found Or Waiting for input??
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for reply. I tried by removing earliest and latest time but its not working. Its showing "No Results Found"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I added a table command with the required fields and that resolved it.