- Splunk Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Splunk 6.2.3 vulnerability in dashboard
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello guys,
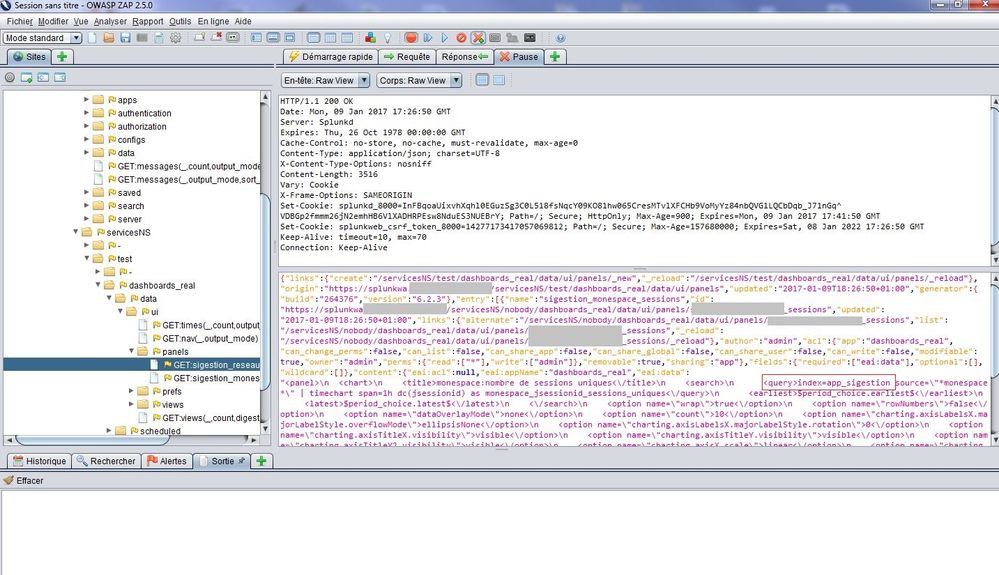
there is a vulnerability in Splunk, it's possible to edit the search of a dashboard using web browser's developer tools or OWASP, this can be restricted by role, however it's possible to remove timechart then show raw logs which we don't want :
//
// SEARCH MANAGERS
//
var search1 = new SearchManager({
"id": "search1",
"status_buckets": 0,
--> "search": "index=myindex | timechart span=1d count", <---
"earliest_time": "-7d@h",
"cancelOnUnload": true,
"latest_time": "now",
"app": utils.getCurrentApp(),
"auto_cancel": 90,
"preview": true,
"runWhenTimeIsUndefined": false
}, {tokens: true, tokenNamespace: "submitted"});
To finish our aim is to avoid user able to see raw data, only table or timechart.
Thanks a lot!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is true, but...
a) search restrictions aka. permissions still apply
b) if you want the user not to see _raw in any case, create a summary index without the (sensitive) data
c) have a look at embedded reports, I have not used them yet, so I am not sure if that will solve your issue
d) in 6.5 included javascript files are no longer visible in the source file list of the browsers dev console as they are loaded into memory somehow, this makes it more difficult to intercept (but anyway not impossible i guess)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is true, but...
a) search restrictions aka. permissions still apply
b) if you want the user not to see _raw in any case, create a summary index without the (sensitive) data
c) have a look at embedded reports, I have not used them yet, so I am not sure if that will solve your issue
d) in 6.5 included javascript files are no longer visible in the source file list of the browsers dev console as they are loaded into memory somehow, this makes it more difficult to intercept (but anyway not impossible i guess)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
summary indexing solved the problem.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
using prebuilt panels is good but still vulnerable through OWASP ZAP (see above) thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello lweber,
could you try this : http://127.0.0.1:8000/fr-FR/splunkd/__raw/servicesNS/admin/search/data/ui/panels/DASHBOARDNAME?outpu...
replace DASHBOARDNAME by your Dashboard or using OWASP ZAP I think javascript is still used in 6.5
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
argh... too late 😉