Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Dashboards & Visualizations
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Issue with mvindex in dashboard eval when using ne...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Issue with mvindex in dashboard eval when using negative index value
eurban
Explorer
09-20-2019
11:40 AM
We are using Splunk 7.2.7.
When I use a negative index value in mvindex in a search eval, it works fine.
However, when I use a negative index value in a dashboard eval, it fails.
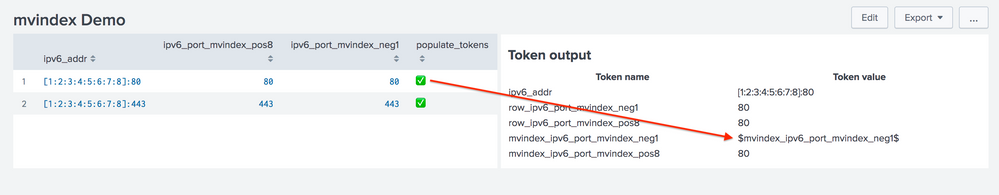
Here is a dashboard to demonstrate the issue.
Click on the "populate_tokens" cell in each row to populate the tokens that will display on the right-hand panel.
<dashboard>
<label>mvindex Demo</label>
<row>
<panel>
<title></title>
<table>
<search>
<query>| makeresults
| eval ipv6_addr="[1:2:3:4:5:6:7:8]:80"
| append [| makeresults | eval ipv6_addr="[1:2:3:4:5:6:7:8]:443"]
| eval ipv6_port_mvindex_neg1 = mvindex(split(ipv6_addr,":"),-1)
| eval ipv6_port_mvindex_pos8 = mvindex(split(ipv6_addr,":"),8)
| eval populate_tokens = "✅"
| fields - _time
| fields ipv6_addr, ipv6_port_mvindex_pos8, ipv6_port_mvindex_neg1, populate_tokens</query>
<earliest>-4h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="count">100</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">cell</option>
<option name="percentagesRow">false</option>
<option name="rowNumbers">true</option>
<option name="totalsRow">false</option>
<option name="wrap">true</option>
<drilldown>
<condition field="ipv6_addr"></condition>
<condition field="ipv6_port_mvindex_pos8"></condition>
<condition field="ipv6_port_mvindex_neg1"></condition>
<condition field="populate_tokens">
<eval token="ipv6_addr">$row.ipv6_addr$</eval>
<eval token="row_ipv6_port_mvindex_neg1">$row.ipv6_port_mvindex_neg1$</eval>
<eval token="row_ipv6_port_mvindex_pos8">$row.ipv6_port_mvindex_pos8$</eval>
<eval token="mvindex_ipv6_port_mvindex_neg1">mvindex(split($row.ipv6_addr$,":"),-1)</eval>
<eval token="mvindex_ipv6_port_mvindex_pos8">mvindex(split($row.ipv6_addr$,":"),8)</eval>
</condition>
</drilldown>
</table>
</panel>
<panel>
<html>
<body>
<h1>Token output</h1>
<table style="width:100%">
<tr>
<th>Token name</th>
<th>Token value</th>
</tr>
<tr>
<td>ipv6_addr</td>
<td>$ipv6_addr$</td>
</tr>
<tr>
<td>row_ipv6_port_mvindex_neg1</td>
<td>$row_ipv6_port_mvindex_neg1$</td>
</tr>
<tr>
<td>row_ipv6_port_mvindex_pos8</td>
<td>$row_ipv6_port_mvindex_pos8$</td>
</tr>
<tr>
<td>mvindex_ipv6_port_mvindex_neg1</td>
<td>$mvindex_ipv6_port_mvindex_neg1$</td>
</tr>
<tr>
<td>mvindex_ipv6_port_mvindex_pos8</td>
<td>$mvindex_ipv6_port_mvindex_pos8$</td>
</tr>
</table>
</body>
</html>
</panel>
</row>
</dashboard>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sev
New Member
03-13-2024
03:54 AM
I know this Question is old and probably not relevant for you anymore, however I stumbled over the same Issue and wanted to share a possible solution.
I could not find any documentation on why mvindex is not working with negative values in the Dasboards, however there is a workaround.
<eval token="mvIndexValue">mvcount(<mvfield>)-1</eval>
<eval token="lastValue">mvindex(<mvfield>, $mvIndexValue$)</eval>
I think it's pretty ugly, but so far I have not found a better solution 😕
Get Updates on the Splunk Community!
Index This | What is broken 80% of the time by February?
December 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Unlock Faster Time-to-Value on Edge and Ingest Processor with New SPL2 Pipeline ...
Hello Splunk Community,
We're thrilled to share an exciting update that will help you manage your data more ...
Splunk MCP & Agentic AI: Machine Data Without Limits
Discover how the Splunk Model Context Protocol (MCP) Server can revolutionize the way your organization uses ...