- Splunk Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- How to limit the instance for the fields according...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Team,
I am using below query:
index="abc" sourcetype =600000304_gg_abs_ipc2 source="/amex/app/gfp-settlement-raw/logs/gfp-settlement-raw.log" "ReadFileImpl - ebnc event balanced successfully"
| eval True=if(searchmatch("ebnc event balanced successfully"),"✔","")
| eval EBNCStatus="ebnc event balanced successfully"
| table EBNCStatus True
when I selecting last 7 days its showing multiple columns .
I want the value to be displayed according to drop down selected like last 7 days last 30 days.
Can someone please guide me here
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unless you are running your search at exactly midnight, the last 7 days will be spread over 8 days. You need to use the relative option in the time picker and align to the start and end of days to get exactly 7 days worth of events
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your search restrict the output to just two columns regardless of the timeframe. Please provide an example of your expected output.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
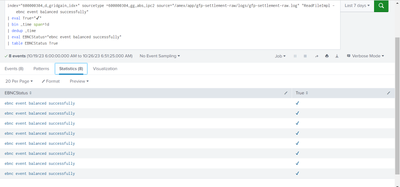
I want two columns only but currently when I am selecting last 7 days its coming more that 7.
If I used dedup command its showing only 1
I want when I select last 7 days it should show only last 7 days
I am selecting last 7 days its showing 60 statistics .
query
index="abc" sourcetype =600000304_gg_abs_ipc2 source="/amex/app/gfp-settlement-raw/logs/gfp-settlement-raw.log" "ReadFileImpl - ebnc event balanced successfully"
| eval True=if(searchmatch("ebnc event balanced successfully"),"✔","")
| eval EBNCStatus="ebnc event balanced successfully"
| table EBNCStatus True
PFA attached screenshot.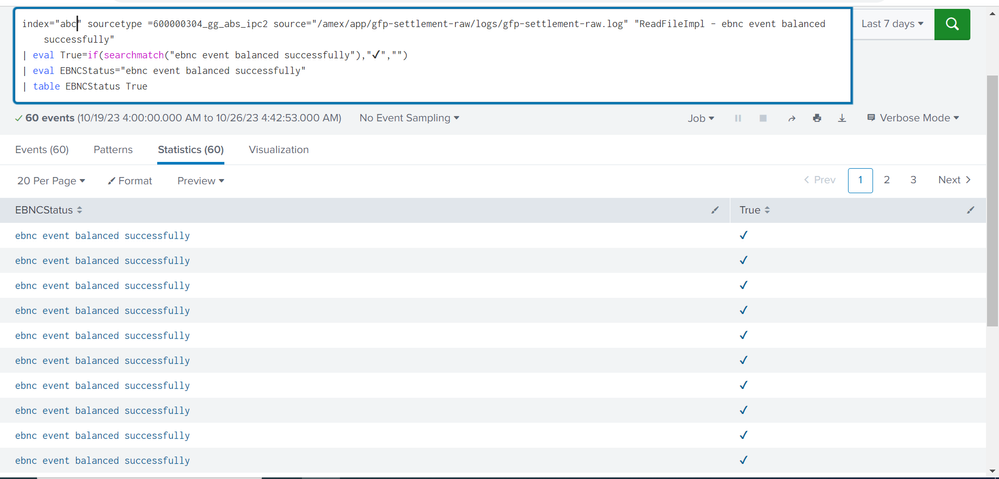
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think you are mixing up rows and columns - you have 60 rows and 2 columns
What result are you expecting?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have 60 events but I want when I select last 7 days from date drop down It should display only 7 results
If I select last 30 days it should display only 30 results.
current query
index="abc" sourcetype =600000304_gg_abs_ipc2 source="/amex/app/gfp-settlement-raw/logs/gfp-settlement-raw.log" "ReadFileImpl - ebnc event balanced successfully"
| eval True=if(searchmatch("ebnc event balanced successfully"),"✔","")
| eval EBNCStatus="ebnc event balanced successfully"
| table EBNCStatus True
@ITWhisperer can you please guide
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which event do you want to use from each day, the first, the last, only those where searchmatch("ebnc event balanced successfully") is true, what do you want to do if none of the events from a particular day have searchmatch("ebnc event balanced successfully") equating to true?
This has been said many times before, you need to be clear what you are trying to achieve.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't want to do anything if none of the events from a particular day have searchmatch
yes , I just want the events where searchmatch("ebnc event balanced successfully") is true.
But I want when I am selecting last 7 days it should show last 7 events only
1 event per day I want.
So if it would be last 7 days it will look something like this:(only 7 events)
EBNCStatus true
ebnc event balanced successfully ✔
ebnc event balanced successfully ✔
ebnc event balanced successfully ✔
ebnc event balanced successfully ✔
ebnc event balanced successfully ✔
ebnc event balanced successfully ✔
ebnc event balanced successfully ✔
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Given the initial search has the same criteria as the searchmatch, True will always be a tick, so you just need to dedup the days
index="abc" sourcetype =600000304_gg_abs_ipc2 source="/amex/app/gfp-settlement-raw/logs/gfp-settlement-raw.log" "ReadFileImpl - ebnc event balanced successfully"
| eval True="✔"
| bin _time span=1d
| dedup _time
| eval EBNCStatus="ebnc event balanced successfully"
| table EBNCStatus True- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried below query
index="600000304_d_gridgain_idx*" sourcetype =600000304_gg_abs_ipc2 source="/amex/app/gfp-settlement-raw/logs/gfp-settlement-raw.log" "ReadFileImpl - ebnc event balanced successfully"
| eval True="✔"
| bin _time span=1d
| dedup _time
| eval EBNCStatus="ebnc event balanced successfully"
| table EBNCStatus TrueWhen I am selecting last 7 days its showing 8 events instead of 7
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unless you are running your search at exactly midnight, the last 7 days will be spread over 8 days. You need to use the relative option in the time picker and align to the start and end of days to get exactly 7 days worth of events
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @ITWhisperer for this help