Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Re: How to limit the 'All' option to what query ac...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would like to be able to limit the 'All' option to what my query actually returns and not for * entries for targetAppAlternateId.
<form theme="dark">
<label>Logins</label>
<fieldset submitButton="false">
<input type="dropdown" token="myApp">
<label>Application:</label>
<fieldForLabel>targetAppAlternateId</fieldForLabel>
<fieldForValue>targetAppAlternateId</fieldForValue>
<search>
<query>index=myIndex targetAppAlternateId="App1.*" OR targetAppAlternateId="App2" | dedup targetAppAlternateId
| sort by targetAppAlternateId</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<choice value="*">All</choice>
</input>
Any help would be greatly appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you Please try below example?
<form>
<label>Limit All Option in Search</label>
<fieldset submitButton="false">
<input type="dropdown" token="myApp">
<label>Application:</label>
<fieldForLabel>targetAppAlternateId</fieldForLabel>
<fieldForValue>targetAppAlternateId</fieldForValue>
<search>
<query>index=myIndex targetAppAlternateId="App1.*" OR targetAppAlternateId="App2" | dedup targetAppAlternateId
| sort by targetAppAlternateId</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<choice value="*">All</choice>
<change>
<condition match="$value$=="*"">
<set token="condition_tkn">targetAppAlternateId="App1.*" OR targetAppAlternateId="App2"</set>
</condition>
<condition>
<set token="condition_tkn">targetAppAlternateId="$value$"</set>
</condition>
</change>
</input>
</fieldset>
<row>
<panel>
<html>
$myApp$ <br/>
$condition_tkn$
</html>
</panel>
</row>
</form>
My Sample XML :
<form>
<label>Limit All Option in Search</label>
<fieldset submitButton="false">
<input type="dropdown" token="myApp">
<label>Application:</label>
<fieldForLabel>sourcetype</fieldForLabel>
<fieldForValue>sourcetype</fieldForValue>
<search>
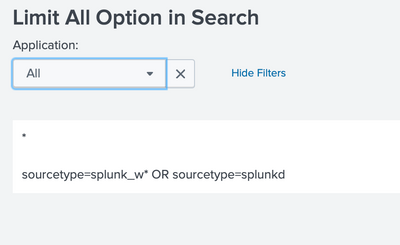
<query>index=_internal sourcetype=splunk_w* OR sourcetype=splunkd | stats count by sourcetype</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<choice value="*">All</choice>
<change>
<condition match="$value$=="*"">
<set token="condition_tkn">sourcetype=splunk_w* OR sourcetype=splunkd</set>
</condition>
<condition>
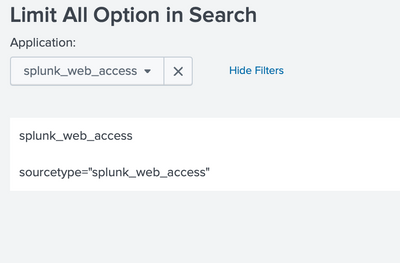
<set token="condition_tkn">sourcetype="$value$"</set>
</condition>
</change>
</input>
</fieldset>
<row>
<panel>
<html>
$myApp$ <br/>
$condition_tkn$
</html>
</panel>
</row>
</form>
Thanks
KV
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you Please try below example?
<form>
<label>Limit All Option in Search</label>
<fieldset submitButton="false">
<input type="dropdown" token="myApp">
<label>Application:</label>
<fieldForLabel>targetAppAlternateId</fieldForLabel>
<fieldForValue>targetAppAlternateId</fieldForValue>
<search>
<query>index=myIndex targetAppAlternateId="App1.*" OR targetAppAlternateId="App2" | dedup targetAppAlternateId
| sort by targetAppAlternateId</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<choice value="*">All</choice>
<change>
<condition match="$value$=="*"">
<set token="condition_tkn">targetAppAlternateId="App1.*" OR targetAppAlternateId="App2"</set>
</condition>
<condition>
<set token="condition_tkn">targetAppAlternateId="$value$"</set>
</condition>
</change>
</input>
</fieldset>
<row>
<panel>
<html>
$myApp$ <br/>
$condition_tkn$
</html>
</panel>
</row>
</form>
My Sample XML :
<form>
<label>Limit All Option in Search</label>
<fieldset submitButton="false">
<input type="dropdown" token="myApp">
<label>Application:</label>
<fieldForLabel>sourcetype</fieldForLabel>
<fieldForValue>sourcetype</fieldForValue>
<search>
<query>index=_internal sourcetype=splunk_w* OR sourcetype=splunkd | stats count by sourcetype</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<choice value="*">All</choice>
<change>
<condition match="$value$=="*"">
<set token="condition_tkn">sourcetype=splunk_w* OR sourcetype=splunkd</set>
</condition>
<condition>
<set token="condition_tkn">sourcetype="$value$"</set>
</condition>
</change>
</input>
</fieldset>
<row>
<panel>
<html>
$myApp$ <br/>
$condition_tkn$
</html>
</panel>
</row>
</form>
Thanks
KV
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am sure I am doing something wrong but it is not working for me. Below is the full sample I am testing:
<form theme="dark">
<label>Logins</label>
<fieldset submitButton="false">
<input type="time" token="selectTime">
<label>Time:</label>
<default>
<earliest>-7d@h</earliest>
<latest>now</latest>
</default>
</input>
<input type="dropdown" token="myApp">
<label>Application:</label>
<fieldForLabel>targetAppAlternateId</fieldForLabel>
<fieldForValue>targetAppAlternateId</fieldForValue>
<search>
<query>index=myIndex targetAppAlternateId="App1.*" OR targetAppAlternateId="App2" | dedup targetAppAlternateId
| sort by targetAppAlternateId</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<choice value="*">All</choice>
<change>
<condition match="$value$=="*"">
<set token="condition_tkn">targetAppAlternateId="App1.*" OR targetAppAlternateId="App2"</set>
</condition>
<condition>
<set token="condition_tkn">targetAppAlternateId="$value$"</set>
</condition>
</change>
</input>
</fieldset>
<row>
<panel>
<chart>
<search>
<query>index=myIndex targetAppAlternateId="$myApp$"
| stats count by targetAppAlternateId</query>
<earliest>$selectTime.earliest$</earliest>
<latest>$selectTime.latest$</latest>
<refresh>1m</refresh>
<refreshType>delay</refreshType>
</search>
<option name="charting.chart">pie</option>
<option name="charting.drilldown">none</option>
<option name="refresh.display">none</option>
</chart>
</panel>
</row>
</form>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just update your pie chart search with below one. 🙂
<query>index=myIndex $condition_tkn$
| stats count by targetAppAlternateId</query>
Thanks
KV
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much! Works perfectly!