- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Re: Need help in extraction of %utilization value ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to extract %utilization value from the raw field or message field using rex command and add it as field?
Dataframe row : {"_c0":{"0":null,"1":"00:00:01","2":"13:30:01"},"_c1":{"0":null,"1":"CPU","2":"all"},"_c2":{"0":"Linux","1":"%user","2":"1.05"},"_c3":{"0":"3.10.0-1160.76.1.el7.x86_64","1":"%nice","2":"0.34"},"_c4":{"0":"(fraasdwhbdd1.de.db.com)","1":"%system","2":"0.83"},"_c5":{"0":"16\/05\/23","1":"%iowait","2":"0.05"},"_c6":{"0":"_x86_64_","1":"%steal","2":"0.00"},"_c7":{"0":"(8","1":"%idle","2":"97.73"},"_c8":{"0":"CPU)","1":"%utilization","2":"2.27"}}.
The above event is a sample event that has been received to our splunk portal. We need to extract the %utilization value from the above event which is the value of 2.27. This %utilization value is dynamic. we need to extract it using rex command. Please help us on this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
%utilization\",.+:\"(?<utilization>[\d\.]+)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ITWhisperer,
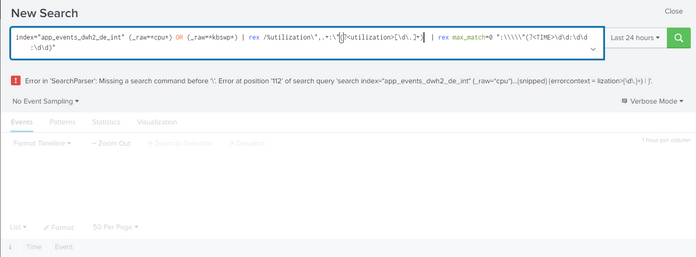
Thanks for your reply. I tried using the given command, but I am facing an error like below. Please help us on this.
Please help us on the above thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try removing the / at the beginning of the rex (did you get this from regex101.com as this was not in the expression I shared?)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ITWhisperer,
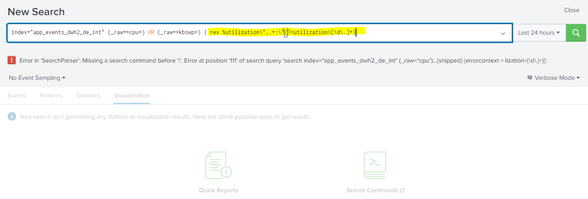
I have tried by removing the / at the rex, but it is showing the same error like below.
I request you to kindly look into this and help us on this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Put the expression in quotes
| rex "%utilization\",.+:\"(?<utilization>[\d\.]+)"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ITWhisperer,
Thanks this has worked for the extraction of Utilization Value. But when I tried to extract the other fields such as %idle of value 97.73 or the %user value I am not able to extract using the same method. Can I get the reason please.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please share the extraction (in a code block </> not an image) of the failing extraction commands
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ITWhisperer,
Thanks for your email. Below is the code in which I am trying to extract %idle, %user, %steal, %nice, %system, %iowait values and add them as a separate fields.
Dataframe row : {"_c0":{"0":null,"1":"00:00:01","2":"13:30:01"},"_c1":{"0":null,"1":"CPU","2":"all"},"_c2":{"0":"Linux","1":"%user","2":"1.05"},"_c3":{"0":"3.10.0-1160.76.1.el7.x86_64","1":"%nice","2":"0.34"},"_c4":{"0":"(fraasdwhbdd1.de.db.com)","1":"%system","2":"0.83"},"_c5":{"0":"16\/05\/23","1":"%iowait","2":"0.05"},"_c6":{"0":"_x86_64_","1":"%steal","2":"0.00"},"_c7":{"0":"(8","1":"%idle","2":"97.73"},"_c8":{"0":"CPU)","1":"%utilization","2":"2.27"}}.
Please help us on this.
I have tried to extract those values using the same method which was done earlier for extracting the utilization, but it was not working.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please share what you actually tried
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have tried the below command to extract the % idle value in the sample event
index="app_events_dwh2_de_int" (_raw=*cpu*) OR (_raw=*kbswp*) | rex ": %idle\",.+:\"(?<idle>[\d\.]+)"
Dataframe row : {"_c0":{"0":null,"1":"00:00:01","2":"13:30:01"},"_c1":{"0":null,"1":"CPU","2":"all"},"_c2":{"0":"Linux","1":"%user","2":"1.05"},"_c3":{"0":"3.10.0-1160.76.1.el7.x86_64","1":"%nice","2":"0.34"},"_c4":{"0":"(fraasdwhbdd1.de.db.com)","1":"%system","2":"0.83"},"_c5":{"0":"16\/05\/23","1":"%iowait","2":"0.05"},"_c6":{"0":"_x86_64_","1":"%steal","2":"0.00"},"_c7":{"0":"(8","1":"%idle","2":"97.73"},"_c8":{"0":"CPU)","1":"%utilization","2":"2.27"}}.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your expression doesn't match your event because you have introduced a space instead of a \" between the : and %idle
Regex work by matching to anchor text; if the anchor text is not correct, the match (and extraction) doesn't work.
Please examine your expressions and data carefully.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also the mentioned above value is Dynamic and that 2.27% value sometimes may reach up to 99.90%. Please help us in how to extract the above value and add it as a separate field.