Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- merge a string in a list relatively to another str...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello everyone,
I want to add a string in a list which is in a field compared to another string which also is in another field.
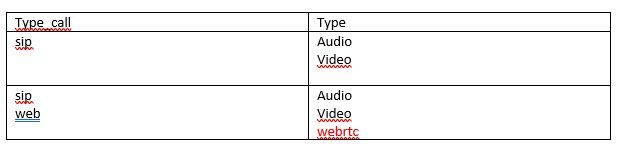
I want to add the string "webrtc" in the list in the field Type where in the field Type_call there is "web"
I tried with the command eval(if(in)) but it didn't start because it replace the entire list in Type by "webrtc"
How can do that, please ?
Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this.
| eval Type=if(match(Type_call,"web"), mvappend(Type, "webrtc"), Type)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this.
| eval Type=if(match(Type_call,"web"), mvappend(Type, "webrtc"), Type)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| makeresults
| eval _raw="Type_call,Type
sip,Audio#Video
sip#web,Audio#Video"
| multikv forceheader=1
| foreach "Type*"
[ eval <<FIELD>> = split('<<FIELD>>',"#")]
| table Type_call Type
| nomv Type_call
| eval Type=if(match(Type_call,"web"), mvappend(Type, "webrtc"), Type)
It works, thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it works thank you @to4kawa .
I used that :
...| table pole participant type_call_leg type | eval type=if(match(type_call_leg,"acano"), mvappend(type, "webrtc"), type)
and it works with the "match" and not "mvfind"
thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The use of match and nomv rather then mvfind, is an indicator that the field was not multivalue or was hitting some MV field limit. In principle mvfind should work as a general rule.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ok thanks for this clarification.
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I hadn't noticed that you have a similar approach in yours. 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks to you @arjunpkishore5 also for your request it works with the match
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| makeresults
| eval _raw="Type_call,Type
sip,Audio#Video
sip#web,Audio#video"
| multikv forceheader=1
| foreach Type*
[eval <<FIELD>> = split('<<FIELD>>',"#")]
| table Type_call Type
`comment("this is sample base data")`
| eval Type=if(mvfind(Type_call,"web") > 0, mvappend(Type,"webtrc"),Type)
Hi, try this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello to4kawa,
Thank you for you answer.
How do you do that but without the makeresults and the sample of data and the foreach?
My data is contained as the table above and i have other string in addition to "Audio" and "Video".
I have a field type_call and type and I want to do what I explained above but without using a data sample but with the data contained in the fields as splunk does.
Thank you
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the relevant line that does the work
eval Type=if(mvfind(Type_call,"web") > 0, mvappend(Type,"webtrc"),Type)
The rest is setup. The mvfind is looking for the string 'web' in the Type_call and if found (>0) the it adds the webtrc field to the existing multivalue Type field
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @bowesmana , that's right.
so, hi @amir_bnp
| makeresults
| eval _raw="Type_call,Type
sip,Audio#Video
sip#web,Audio#Video"
| multikv forceheader=1
| foreach "Type*"
[ eval <<FIELD>> = split('<<FIELD>>',"#")]
| table Type_call Type
Have you checked this result first?
Type_call Type
sip Audio
Video
----------------------------
sip Audio
web Video
From this result, webtrc is added when the query eval is executed.
But if this doesn't work, it seems that Type_call is not multivalue, unlike the example given.
what's your query?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @to4kawa ,
your request works for the small table that I gave as an example but how do I change the request for it to work on a table containing the same fields but with thousands of lines?
thank you and sorry if I did not understand at first.
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @bowesmana ,
I already tried this but it didn't work.
In my row which contains "sip" and "web" in the field Type_call, I don't have the "webrtc" which is added in the "Type" fields.
Thanx
Amir