Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Splunk return different event count in verbose vs ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk return different event count in verbose vs fast mode using "where"
Hi!
I'm having a problem with the following simple search in Splunk 6.3.3:
index=myIndex sourcetype=mySourcetype earliest="03/09/2016:08:00:00" latest="03/09/2016:18:00:00"
| eval time=strftime(_time,"%H:%M") | eval day=strftime(_time,"%d/%m/%Y")
| stats first(verso) as FirstVerso first(time) as FirstTime by day,badge_id
| where FirstVerso=1 | stats count as "Users In"
All events have the badge_id and verso fields
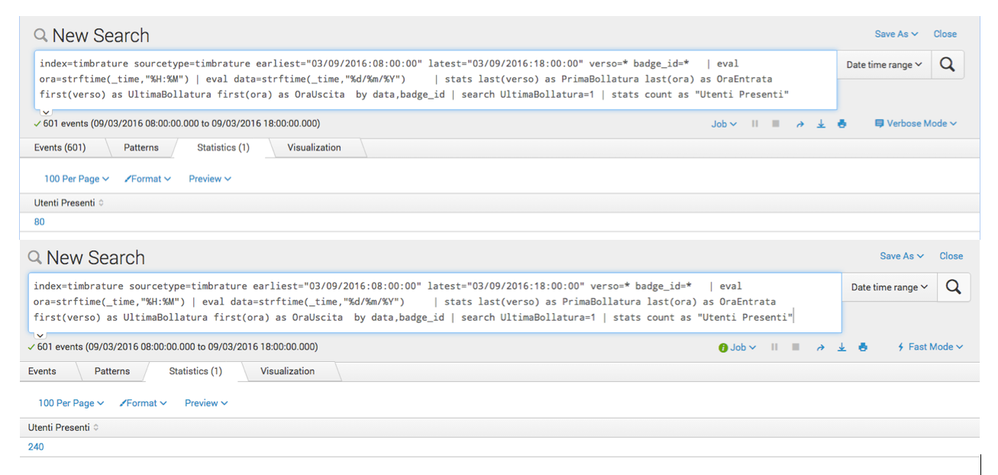
If i run it in Verbose Mode, I get 80 results: running the same search in Fast Mode I get 240 results. The problem is with the "where FirstVerso=1" condition: if I omit this check, I get always the same number of results (325) both in Verbose and Fast mode.
Suggestions?!?!
Regards,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here's a screenshot of my actual searches in Verbose and Fast mode.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For S&Gs try adjusting your initial search to
index=myIndex sourcetype=mySourcetype earliest="03/09/2016:08:00:00" latest="03/09/2016:18:00:00" day=* badge_id=* verso=*
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Runals,
I just try your suggestions, but I still get the same odd behaviour....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are the field verso an custom extracted field OR is it automatically extracted by Splunk?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
No, there's a field extraction to extract those fields using a REPORT commando in props.conf.