Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Re: Why did Infosec App stopped showing data?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why did Infosec App stop showing data?
Hi,
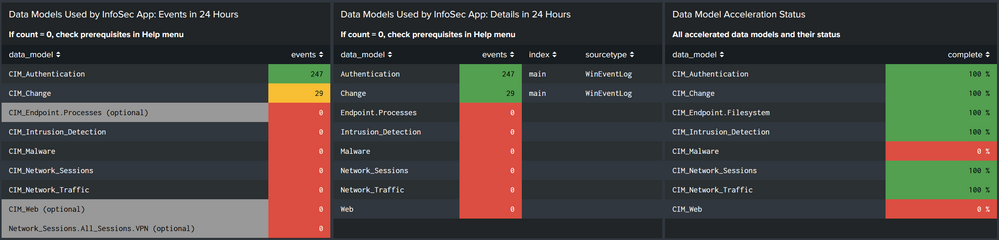
I have configured the Infosec App in my splunk making sure that i had all the steps in prerequisites completed. It was working for a couple of days, but it suddenly sttoped showing data. I have CIM for splunk and I can see in the health panel from infosec that the acceleration for the data models is working but I'm only recieving event and details from the Authentication and Change data model.
going through this documentation https://docs.splunk.com/Documentation/InfoSec/1.7.0/Admin/ValidateDataSources#Identify_tagged_events...
I have checked that only Authentication and Change are getting data, not the rest. If I try to follow the guide there is no tags for the rest of the datamodels.
Is this why infosec stopped working?
Can anyone help with this?
Thank you.
Regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What's the CIM version installed?
On the CIM Setup page, did you verify all the required Data Models are Accelerated?
Are the required indexes in the "Indexes whitelist" aligned with their respective Data Model?
Do you have the required TAs for your log data installed on your Search Head?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Stefanie ,
1.- The CIM version I have installed is 5.0.1.
2.- When i accelerated the models after installing, infosec was reciecing data and after a couple of days sttoped working.
3.- When I check the index whitelist of each data model it's blank, Is there anything I should add to it?
4.- I have installed all required TA's written in the infosec App prerequisites.
Another thing that seems strange is that checking the data model from Settings - Knowledge - Data models. If I choose any model and edit the constraint but without modifying it, an error shows up saying this: "In handler 'datamodeledit': Error in 'Authentication': Dataset constraints must specify at least one index. "
Thanks for your answers.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting.
I had the same problem with my CIM for Enterprise Security. The index whitelist was blank and I wasn't getting events anymore.
In the Indexes Whitelist field, can you put * ? Here's an example of mine.
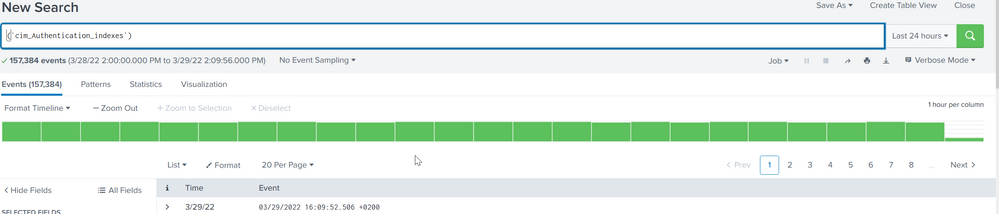
Make that change and let it sit for a few minutes to run. Then try searching that datamodel using a search like
(`cim_Authentication_indexes`)
After verifying data is coming in, you can manually specify the indexes in the Indexes Whitelist by what's showing up using the wildcard.
Let me know how this works for you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Stefanie,
I did what you said in the data models that are needed for the infosec app.
Nothing changed from the health panel view. It keeps only getting data from authentication and change although the acceleration works good for all of them except for malware and web.
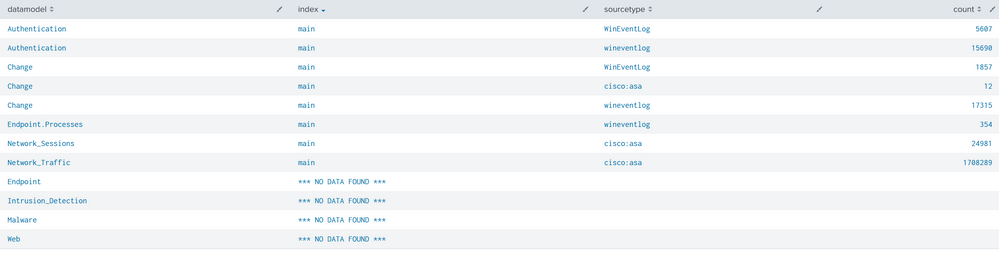
One thing i saw that changed is when running the query to identify indexes that feed the data models.
| makeresults | eval datamodels = "Authentication:Change:Endpoint:Intrusion_Detection:Network_Sessions:Network_Traffic:Malware:Endpoint.Processes:Web" | makemv delim=":" datamodels | mvexpand datamodels | map search="| makeresults | eval notfound=\"*** NO DATA FOUND ***\" | append [| tstats count from datamodel=$datamodels$ by index, sourcetype] | eventstats count as events |eval datamodel=\"$datamodels$\", index=coalesce(index,notfound)| search NOT notfound=* OR events=1 | table datamodel, index, sourcetype,count" | sort datamodel, index, sourcetype
Now i see that network traffic and network sessions data models are no longer indicating "NO DATA FOUND" and they show 1.708.289 and 24.981 events taking them from the main index.
Still not getting that data in infosec... I also did the query that you suggested before and everything seems to be working.
I was wondering if you could post a screenshot of your network traffic data model just to adjust the settings the same way you have them.
When I added the "*" in the data models i saw that your tag whitelist was blank and mine has 4 or 5 tags, is it supposed to be like that?
Thanks for you help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My settings for the Network traffic data model is the same as the screenshot above. The only difference is after I used the wildcard to include all indexes, waited to see what it detected, then I modified the settings to only include the indexes it was aligning to the data model using the search:
(`cim_Network_Traffic_indexes`)
As for your tag whitelist. I removed everything. I didn't understand why those specific tags were there when if you go to the Data Model page in Splunk and look at the Data Models, those tags did not align with the tags it wants. For example the "All Traffic" search for the Network Traffic data model is
(`cim_Network_Traffic_indexes`) tag=network tag=communicate
Those two tags weren't in the tag whitelist in the CIM settings. Try removing them too. Just make sure you have a screenshot or a backup before you do, incase you need them back.