Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Re: Why are CEF Events not all extracting correctl...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why are CEF Events not all extracting correctly, shifting key-value pairs for pipe-delimited fields?
Hi Folks,
I'm ingesting CEF events coming in from ArcSight and getting pushed over SYSLOG to a file, which I have Splunk read. I use this method for a few different types of sources, but with one of them the parsing isn't happening correctly.
It's as if it ignores the cef_vendor field value and puts the cef_product value in there instead. So instead of saying "cef_vendor = McAfee" (I can see within the event that McAfee is occurring after the first pipe in "CEF:0|McAfee|ePolicyOrchestrator|..." ), it will say ePolicyOrchestrator, which is actually the cef_product. And from there other CEF "pipe-delimited" fields are populating wrong. After the CEF pipe-delim fields everything seems to be parsing correctly (the extension fields)
I don't understand why this is parsing incorrectly. All my other feeds come in the same manner, with arcsight-->syslog--->splunk file/folder reader. I shoulod also note that my KV_MODE is set to NONE for this input.
Thanks in advance!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you get this working?
I found some regex errors with "+" meaning one or more. Change these out to "*" and you'll get cef parsing even if the field is empty.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CEF standard says that the version field is mandatory, so "+"es are not an error.
Header Information
CEF uses syslog as a transport mechanism. It uses the following format, comprised of a syslog prefix, a header and an extension, as shown below:
Jan 18 11:07:53 host CEF:Version|Device Vendor|Device Product|Device Version|Signature ID|Name|Severity|[Extension]
The CEF:Version portion of the message is a mandatory header. The remainder of the message is formatted using fields delimited by a pipe ("|") character
...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jravida
You tagged "CEF (Common Event Format) Extraction Utilities" App to your post, but I didn't see you mention it anywhere in the content. I just wanted to check, but have you actually been using that app to parse your CEF Arcsight logs? Sometimes people tag applications in their question on accident because it's the first tag that populates on a list so just wanted to make sure. If not, then that app might help with your field extraction issue. Here's the link to the app's page https://apps.splunk.com/app/487/
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am in fact using the CEF extraction util
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Happy to hear that.
Now back to your question - could you please provide data examples so I'd be able to try figuring out what causes parsing problems with McAfee events?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This one doesn't work:
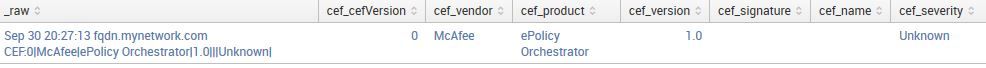
Sep 30 20:27:13 fqdn.mynetwork.com CEF: 0|McAfee|ePolicy Orchestrator|1.0|||Unknown|
But this one extracts and parses fine.
Sep 30 20:27:13 fqdn.mynetwork.com CEF: 0|McAfee|ePolicy Orchestrator|1.0|10196|Access Logged - start|Unknown|
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm unable to reproduce the problem with the data in your example
BTW, your data has space between "CEF:" and "0". Is this way in your real data?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jravida Could you please send me data examples for both correctly and incorrectly parsed events?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
LukeMurphey - app's documentation says that it's for sending Splunk data to ArcSight, and not the other way around...
[
The Splunk App for CEF enables you to aggregate and augment Splunk Enterprise events, transforming them into the Common Event Format (CEF), an open log management standard.
The Splunk App for CEF produces output that consists of your search results reformatted into the Common Event Format. You can then use the CEF output for further processing in compatible applications such as HP ArcSight.]1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In case you are interested, there is an officially supported solution for getting CEF data into Splunk from ArcSight. See https://apps.splunk.com/app/1847/.