- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk Add-on for Microsoft Office 365 Reporting Web Service 2.0.0 404 ERROR- How to resolve?
We've upgrade this add-on to version 2.2.0 and Using Modern Authentication (OAuth), when configured in HF, the internal log shows 404 error as below:
127.0.0.1 - splunk-system-user [14/Aug/2022:20:08:03.558 -0700] "GET /servicesNS/nobody/TA-MS_O365_Reporting/storage/collections/data/TA_MS_O365_Reporting_checkpointer/MDSLAB_obj_checkpoint_oauth HTTP/1.1" 404 140 "-" "curl" - 1ms
Would anybody can know the cause of this error? Any solutions? Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That 404 error indicates a KV store issue. Try cloning your input and then disabling or deleting the existing input.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Having the same issue, keen to hear any solutions.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, has anyone been able to configure the add-on with modern auth? Im getting this same error along with 401 Client Error: Unauthorized for url: https://reports.office365.com/ecp/reportingwebservice/reporting.svc
Followed all the steps, the MS official doc also suggest to add Security Reader role for the App Registration. Shouldn't in theory there be an option to specify the tenant along with client ID and secret? Maybe @jconger might know this one.
Thanks for anyone's reply.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
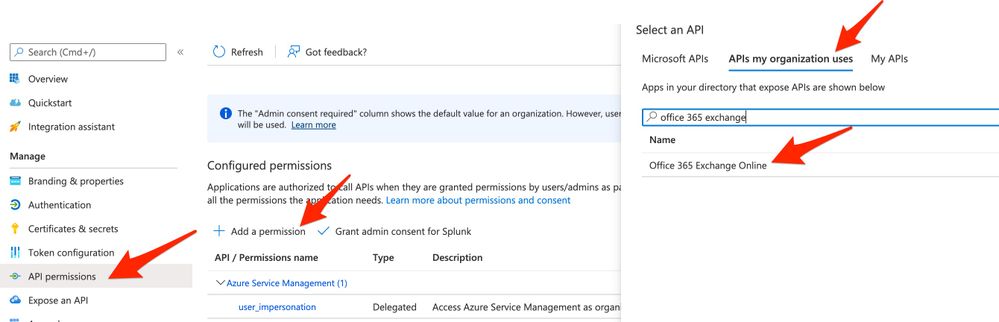
Setting up the permissions for this add-on is a 2 step process:
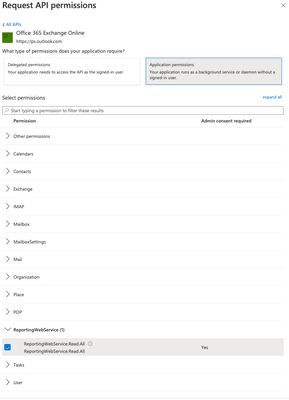
- For the Azure AD app registration, add the ReportingWebService.Read.All API permission.
- This can be found by going to APIs my organization uses => Office 365 Exchange Online. See the attached screenshot
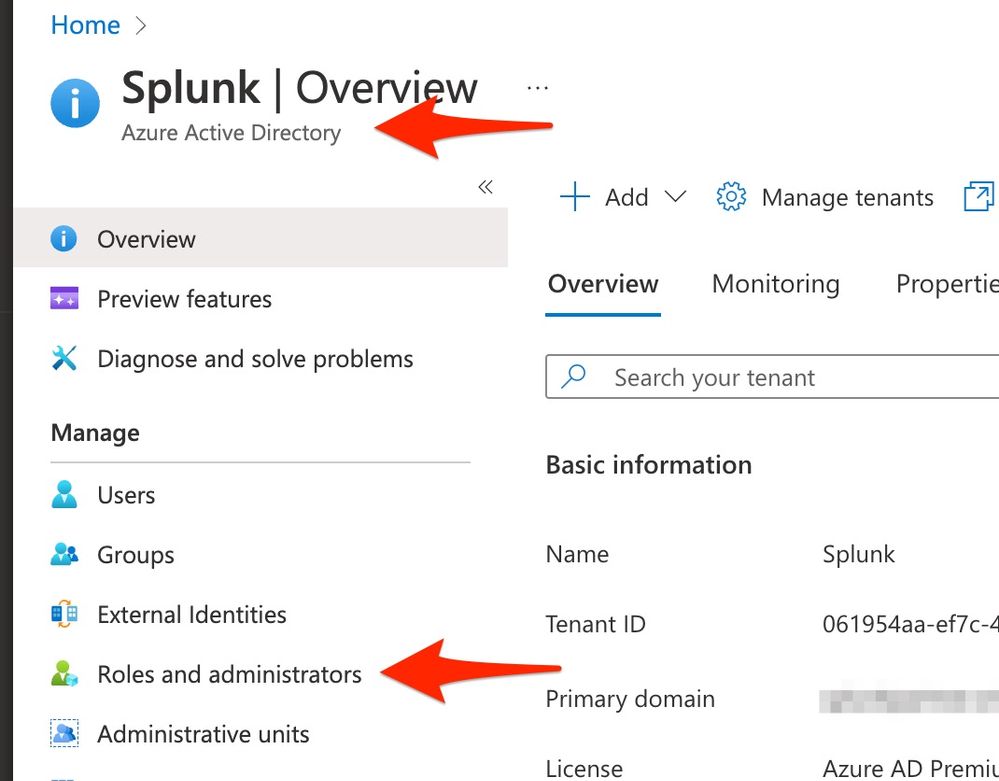
- The Azure AD app registration needs to be assigned a directory role.
- The minimum role that works is Global Reader. Here is a walkthrough on how to do that => https://docs.microsoft.com/en-us/azure/active-directory/roles/manage-roles-portal
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply @jconger. I did try to recreate the input and restart splunkd on the forwarder. I've also given it the ReportingWebService.Read.All under Applications permissions as stated here https://docs.google.com/spreadsheets/d/1YJAqNmcXZU-7O9CxVKupOkR6q2S8TXriMeLAUMYmMs4/ as well as Exchange Administrator and Global Reader role.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
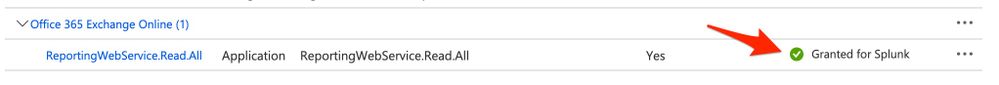
Was the API permission granted?
Also, was the role added at the directory level?
The input recreation suggestion was for the OP since they were getting a 404 on the KV store.
A question about the tenant was mentioned in the thread above. The tenant is specified at the input level. Are you setting up a "Microsoft Office 365 Message Trace (OAuth)" input? That input requires the tenant ID; whereas, the "Microsoft Office 365 Message Trace (Basic Auth)" input does not.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah theres the problem then, thank you. I did not create a new input but rather copy existing one that was set up with basic auth. Makes more sense for the tenant field to be specified on the account along with the client and secret. Thanks anyway.