Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Joining fields from another index to the fields th...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Joining fields from another index to the fields that is generated by |snowincidentalert
So I have an spl query, that does these things:
-gets all the values from index=rds_db that is equal to transfer_status to failure
-passes all the field values (those eval fields) to service now to create an incident ticket
-|snowincidentalert creates tickets. (all those fields before the command are rendered as unusable)
-"Incident Number" , "Incident Link", "Correlation ID" are one of those fields that appears after the command
-field mapping the Incident Number field to the number field from index=snow_incident
-using regex to the description to get the fields needed to supply the email lookup and later the email integration (source_sys_name, target_sys_name)
-using source_sys_name to map the email_group field which is on the email_lookup
-creating a case condition that will match the group to the correct email
- table the fields needed so to use this as a parameter for the email integration and send those emails
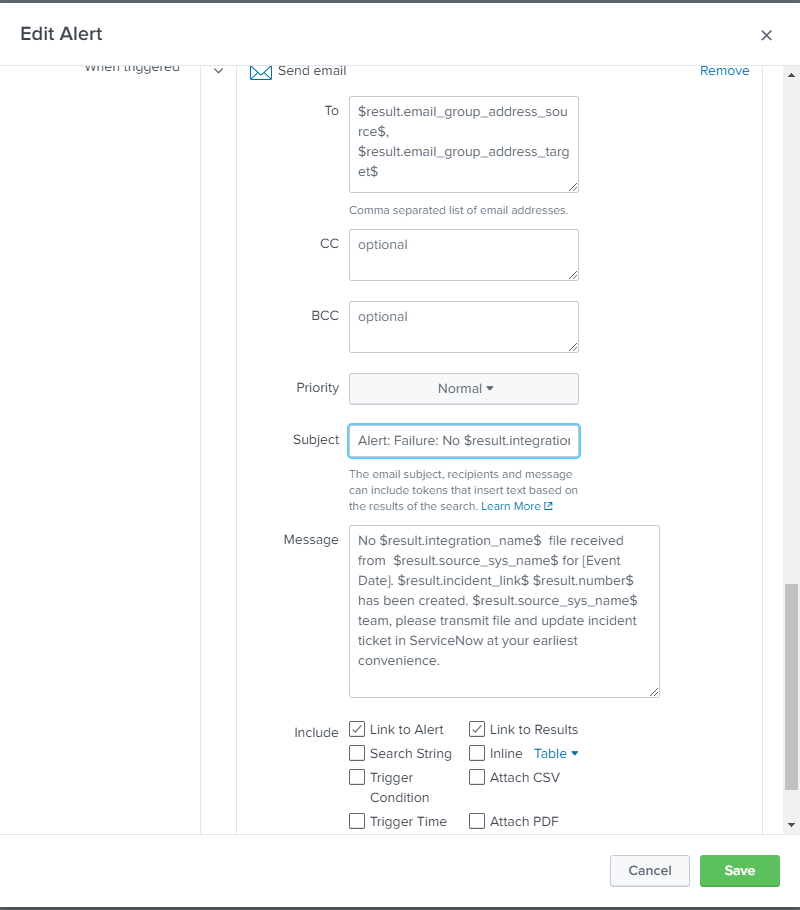
All of these query is located inside of an alert that will be triggered real-time. In our requirements, we need to be able to create new tickets. In my spl query, I just indicated the correlation id so I will not be able to create new ticket and flood the service now db with tickets. My problem is if I dont declare the correlation_id, it doesnt match the incident number that the |snowincidentalert have given. All I know that was working is up to the |rename "Incident Number" as number. After that, it doesn't show any results.
p.s the email alert integration works fine also. It just doesn't give me an email if I remove the correlation_id
-----------------------------------
index="rds_db"
| eval D1=if(transfer_status="Succesful transfer of file from EKS", "Success", "Failure")
| where D1="Failure"
| rename interface_id as "Service ID", priority as "Priority", source_sys_name as "Source", target_sys_name as "Target", integration_name as IntegrationName
| table "Service ID", "Service Name", "Priority", "Source", "Target", "D1", IntegrationName
| eval state="1"
| eval configuration_item=Source
| eval cmdb_ci=Source
| eval contact_type="Splunk ServiceNow Add-on"
| eval assignment_group=Source
| eval category="Application Software"
| eval subcategory="File_Data_Report"
| eval impact="2"
| eval urgency="2"
| eval priority="2"
| eval short_description="No ".IntegrationName." Received"
| eval custom_fields="u_company=testCompany||comments=Here is my comment||description=".Source.": No ".IntegrationName." Received on [Event Date] by ".Target
| eval account="ServiceNow_account"
| eval correlation_id="bda390dfaf3243328a8994022b45d7a3"
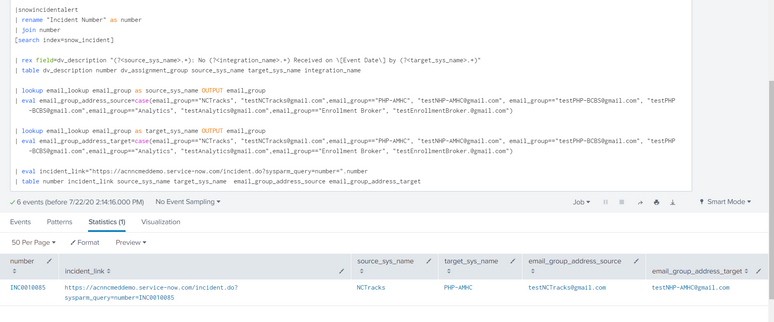
|snowincidentalert
| rename "Incident Number" as number
| join number
[search index=snow_incident]
| rex field=dv_description "(?<source_sys_name>.+): No (?<integration_name>.+) Received on \[Event Date\] by (?<target_sys_name>.+)"
| table dv_description number dv_assignment_group source_sys_name target_sys_name integration_name
| lookup email_lookup email_group as source_sys_name OUTPUT email_group
| eval email_group_address_source=case(email_group=="NCTracks", "testNCTracks@gmail.com",email_group=="PHP-AMHC", "testNCTracks@gmail.com", email_group=="testPHP-BCBS@gmail.com", "testPHP-BCBS@gmail.com",email_group=="Analytics", "testAnalytics@gmail.com",email_group=="Enrollment Broker", "testEnrollmentBroker.@gmail.com")
| lookup email_lookup email_group as target_sys_name OUTPUT email_group
| eval email_group_address_target=case(email_group=="NCTracks", "testNCTracks@gmail.com",email_group=="PHP-AMHC", "testNHP-AMHC@gmail.com", email_group=="testPHP-BCBS@gmail.com", "testPHP-BCBS@gmail.com",email_group=="Analytics", "testAnalytics@gmail.com",email_group=="Enrollment Broker", "testEnrollmentBroker.@gmail.com")
| eval incident_link="https://acnncmeddemo.service-now.com/incident.do?sysparm_query=number=".number
| table number incident_link source_sys_name target_sys_name email_group_address_source email_group_address_target
-----------------------------------