Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Hurricane Labs Add-on for Nessus: Getting connecti...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hurricane Labs Add-on for Nessus: Getting connection error using API keys
Dear Hurricane Labs Team,
We have faced a problem with the Hurricane Labs Add-on for Nessus when we try to connect via api access and secret key.
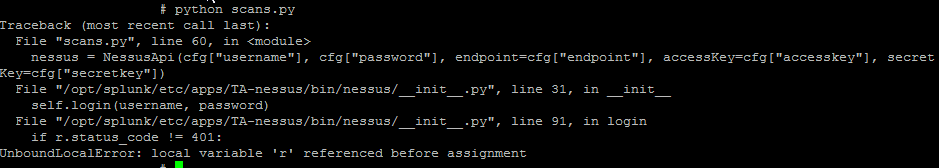
The script returns next error:
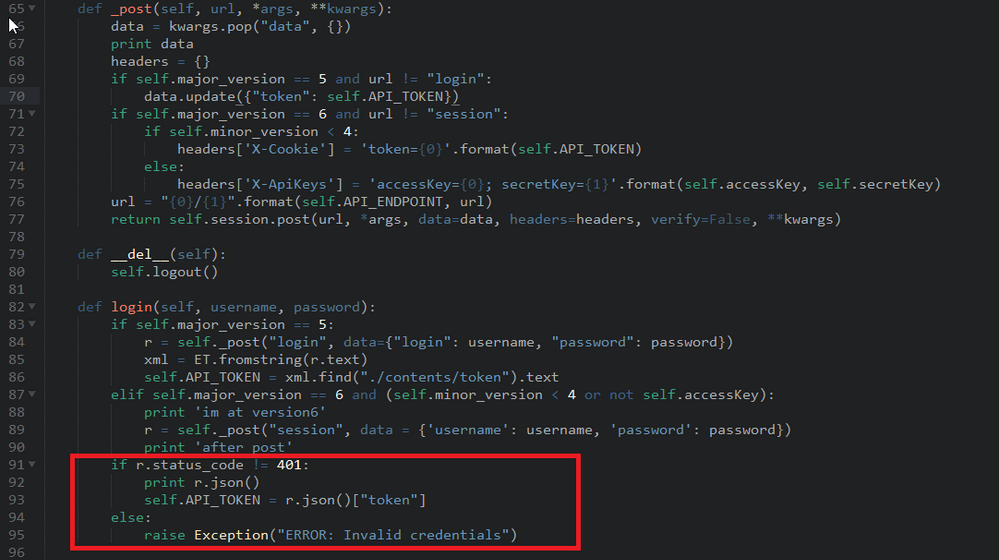
and there is some logical problems with this part of init.py:
Please FIX it. Or explain how to connect in any other way.
Thank you in advance,
Vlada
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey guys sorry for the delay in getting back to you. We'll be releasing a new version of the app to correct this issue. Thanks for the patience and persistence in getting this figured out.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What happens if you remove everything past the number 6 on line 87 in init.py?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
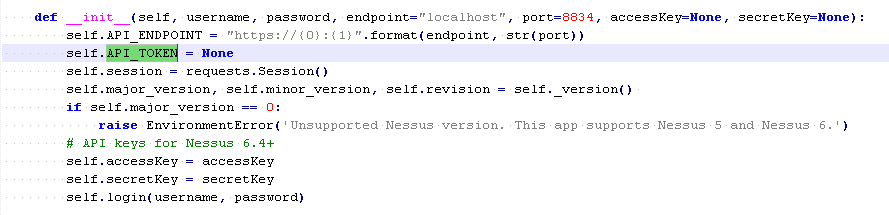
It appears you can probably circumvent this issue by "hardcoding" your api token on line 23 of nessus/__init__.py
For example:
self.API_TOKEN = '14632bb35282171c7b18472287c253668423eb16c1187803'
instead of None
You should be able to get your token using the following curl command:
curl -k -X POST -H 'Content-Type: application/json' -d '{"username":"yourUsername","password":"yourPassword"}' https://[yournessusaddress]:8834/session
which is effectively what the code should be doing... but for some reason it isnt.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When everything after 6 is commented, I have next error :
Traceback (most recent call last):
File "scans.py", line 60, in
nessus = NessusApi(cfg["username"],
cfg["password"],
endpoint=cfg["endpoint"],
accessKey=cfg["accesskey"],
secretKey=cfg["secretkey"]) File
/opt/splunk/etc/apps/TA-nessus/bin/nessus/__init__.py,
line 31, in__init__
self.login(username, password) File
/opt/splunk/etc/apps/TA-nessus/bin/nessus/__init__.py,
line 95, in login
self.API_TOKEN = r.json()["token"] KeyError: 'token'
As far as I understand, the flow reaches line 71 and then, goes strait to 76, as url is "session"
When I comment everything after 6 in line 71, the same error occurs
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok so from what I see you're getting 401 unauthorized which means you've configured the wrong user/pass/etc.
In your error message it looks you're using defaults in the config file.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I looked at the code and errors from my computer vs my phone and have a different opinion now.
It seems they are missing a conditional statement on the login function which would match major version 6 and minor version >= 4 which would get a token from the nessus api.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I completely agree with you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When I modified login function it worked with the same parameters:
def login(self, username, password):
if self.major_version == 5:
r = self._post("login", data={"login": username, "password": password})
xml = ET.fromstring(r.text)
self.API_TOKEN = xml.find("./contents/token").text
elif self.major_version == 6 and (self.minor_version < 4 or not self.accessKey):
r = self._post("session", data = {'username': username, 'password': password})
elif self.major_version == 6 and self.minor_version >4:
r = self._get("session", data = {'username': username, 'password': password})
elif r.status_code != 401 and (self.major_version == 6 and self.minor_version <4):
self.API_TOKEN = r.json()["token"]
**elif r.status_code != 401 and (self.major_version == 6 and self.minor_version >4):
self.API_TOKEN = None**
else:
raise Exception("ERROR: Invalid credentials")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much for the detailed error report! Can you confirm what version of Nessus you're running?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for quick reply.
We use Nessus 6.5.6
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi! any updates?