Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- How to confirm if the IP Reputation App for Splunk...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to confirm if the IP Reputation App for Splunk Enterprise is connecting to the Honeypot to retrieve bad IPs?
I have set up the app and I think it is working, but how do I confirm that a list of Bad IP is being created? I presume there is a search I can use for this.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andy,
the app is working different then then threat list download's in ES or some other threat intel apps on Splunkbase.
The lookup to IP's is done in realtime via DNS query. so there is no threat list download. It's using the http:BL api: https://www.projecthoneypot.org/httpbl_api.php
To test:
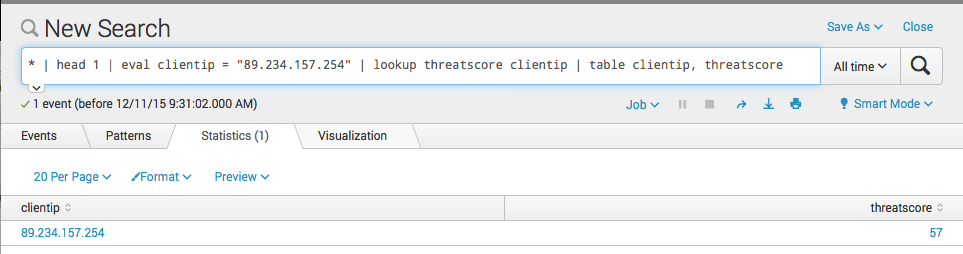
* | head 1 | eval clientip = 89.234.157.254 | lookup threatscore clientip | table clientip, threatscore
In words:
Take any event, add to this event a field called clientip with eval. I took an ip from the project honeypot website that showed bad activity. then doing the scripted lookup. the scripted lookup gives back a new field called threatscore. The ip associated with bad activity should have a threatscore between 1-100 - not 0!
br
Matthias
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Matthias
I get an error when doing this. Here are details from the error log:
Execution costs
Duration (seconds)
Component
Invocations
Input count
Output count
0.00 dispatch.evaluate.head 1 - -
0.39 dispatch.evaluate.search 1 - -
0.00 dispatch.writeStatus 2 - -
0.42 startup.configuration 1 - -
1.05 startup.handoff 1 - -
Search job properties
bundleVersion 18246669895473244130
canSummarize 0
createTime 2015-12-07T16:03:23.000+00:00
cursorTime 2038-01-19T03:14:07.000+00:00
custom {
"dispatch.earliest_time": null,
"dispatch.latest_time": null,
"display.page.search.mode": "verbose",
"search": "* | head 1 | eval clientip = 89.234.157.254 | lookup threatscore clientip | table clientip, threatscore"
}
defaultSaveTTL 604800
defaultTTL 600
delegate None
diskUsage 110592
dispatchState FAILED
doneProgress 1.0
dropCount 0
eai:acl {
"app": "search",
"can_write": "1",
"modifiable": "1",
"owner": "xxxxxxxxxxx",
"perms": {
"read": [
"xxxxxxxxx"
],
"write": [
"xxxxxxx"
]
},
"sharing": "global",
"ttl": "600"
}
earliestTime 1970-01-01T00:00:00.000+00:00
eventAvailableCount 0
eventCount 0
eventFieldCount 0
eventIsStreaming True
eventIsTruncated True
eventSearch search * | head 1
eventSorting desc
isBatchModeSearch False
isDone True
isFailed True
isFinalized False
isPaused False
isPreviewEnabled True
isRealTimeSearch False
isRemoteTimeline False
isSaved False
isSavedSearch False
isTimeCursored 1
isZombie False
keywords None
label None
modifiedTime 2015-12-07T16:03:52.029+00:00
numPreviews 0
pid 7684
priority 5
remoteSearch None
reportSearch None
request {
"adhoc_search_level": "verbose",
"auto_cancel": "30",
"custom.dispatch.earliest_time": null,
"custom.dispatch.latest_time": null,
"custom.display.page.search.mode": "verbose",
"custom.search": "* | head 1 | eval clientip = 89.234.157.254 | lookup threatscore clientip | table clientip, threatscore",
"earliest_time": null,
"indexedRealtime": null,
"latest_time": null,
"preview": "1",
"rf": "*",
"search": "search * | head 1 | eval clientip = 89.234.157.254 | lookup threatscore clientip | table clientip, threatscore",
"status_buckets": "300",
"ui_dispatch_app": "search"
}
resultCount 0
resultIsStreaming True
resultPreviewCount 0
runDuration 0.39
runtime {
"auto_cancel": "30",
"auto_pause": "0"
}
sampleRatio 1
sampleSeed 0
scanCount 0
search search * | head 1 | eval clientip = 89.234.157.254 | lookup threatscore clientip | table clientip, threatscore
searchCanBeEventType 0
searchProviders []
searchTotalBucketsCount 0
searchTotalEliminatedBucketsCount 0
sid 1449504202.98629
statusBuckets 300
ttl 599